The recent Equifax data breach has renewed the public’s interest in data protection. There are also new reports coming out that this leak might have been caused by…you guessed it, ransomware. Businesses must be vigilant about how their data is managed, but the unfortunate truth is that most don’t. Data security and risk reduction is a layered and complex process that factors in not only your technology, but your practices and employees.
The Basics Matter
1. Patch All The Things
Install the latest updates for Windows, Office, Web Browsers, Adobe, etc. The majority of these updates are focused on patching security holes, as well as stability and bugs. Many of the businesses that were catastrophically infected by Wannacry had systems in their network that had not patched a recent Windows update that would have protected them from this infection.
2. Install Quality Antivirus Software
No, Windows Defender or AVG Free does not count if you are a business owner. We recommend business level protection such as Webroot Secure Anywhere Business End Point Protection. Further more, make sure you go to Add/Remove Programs regularly and remove Antivirus Software that is not related to your primary product as these can interfere with its effectiveness.
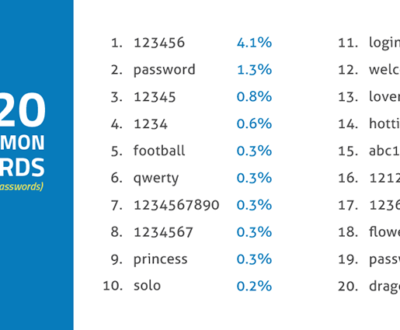
3. Passwords
This is a broken record, you have heard it again and again. Don’t use the same password in multiple locations, change it regularly, and never share it. Read more about password security.
4. Back It Up – Free checklist
Do you check your backups daily? weekly?…at least monthly? This is unrealistic to expect a busy business owner to do. It is critical to have a system in place that automatically backs up your systems to a secure device, and preferably as well to an encrypted cloud. Local Backups can fail, be stolen, or be damaged during a disaster such as a hurricane, flood, or lightening strike. Cloud backups such as One Drive and Dropbox are not perfect and can be infected by malware, save over good data with corrupted versions, or be wiped out by user error with little recourse for recovery. For business owners with sensitive or critical data, we recommend a full disaster and recovery platform such as Datto. You can get a free checklist here.
5. Access – Accountability Matters
I can’t tell you how many offices I have worked in that use the same password…or no password to access workstations for convenience. This mentality leads to the same password for the Wifi which is shared freely, and even applied to online accounts and email. These practices cause routine and often unknown data breaches and intrusions into the network. It can be months or years before these companies find out they were the source of a leak of all of their clients data. Users should have individual emails and workstation user accounts, which will make it easier to trace issues be they malicious users stealing company data or accidentally clicking on an email that infected the entire network. High risk networks such as Legal and Financial offices should utilize a server and domains to more granularity track how data moves and is manipulated in their networks to stay compliant.
6. Email – The Gateway
Email is one of the weakest links in network security. One click and maybe that attachment never opens or the website, so the user moves on. Meanwhile, their system is now infected and uploading all of their data–the whole networks data to a third party including keystrokes such as typing in passwords or bank credentials, or the malware may hibernate and crawl out over the network until all systems are infected before activating and encrypting the entire businesses data—and asks for a ransom. Caution should always be used when interacting with emails, for all users. However, even the most vigilant, paranoid, or educated user is going to be duped into clicking on the wrong email. Some of these emails are laughably badly written, but some of them are nearly indistinguishable from the real thing. This is why it is critical that a business level email server, such as Microsoft Exchange, as well as a firewall are used to filter inbound emails and stop most malicious emails before they ever reach you or your employees. Read more about scam emails.
7. VPN or No Wifi For You
Starbucks is stealing your data, did you know that? No, not the company, but their open wifi is the same as eating something off the floor in a hospital waiting room. This holds true for all public wifi resources, which are often provided by hotels, airports, universities, and other locations. Data is not safe when traveling over these networks for a number of reasons that we will explain in a future article. Virtual Private Networks are a process in which your computer first connects to a security appliance, such as a firewall, before it connects to the internet. This filters your traffic through multiple layers of security and also encrypts it so that external users can’t ‘wiretap’ your wifi. This device can be hosted in your own office, or you can pay for a VPN service for a few dollars a month.
We will write a second article that looks at data security in the office next. We would love to hear your stories below.
Occubit Technology Solutions is a managed IT provider in the DFW area with clients in Keller, Southlake, Colleyville, Arlington, Mansfield, and more. Feel free to contact us today to see how we can join your team and reduce your risk while giving you more time to focus on your business.
Christina Grady is the founder and owner of Occubit Technology Solutions. She has been fascinated by the role technology plays in everyday life since she was a child taking apart VCR's and remote control cars. Her passion for helping others creates a perfect bond with her IT background.






Pingback: child porn
Pingback: child porn
Pingback: cenforce 50
Pingback: cenforce 200 india
Pingback: casino porna
Pingback: advair diskus 250 50
Pingback: Poliçe Paneli
Pingback: cenforce 100 tablets
Pingback: kamagra 100mg oral jelly buy
Pingback: vidalista 40
Pingback: what is vidalista-20 reviews
Pingback: is vidalista 20 safe
Pingback: betgross giriş
Pingback: lugabet giriş
Pingback: kralbet twitter
Pingback: where to buy kamagra
Pingback: priligy 30 mg recensioni
Pingback: priligy 30mg
Pingback: buy dapoxetine online
Pingback: Kod Bulutu
Pingback: clomid 50 mg success
Pingback: porn
Pingback: porn
Pingback: clomiphene over the counter
Pingback: porn
Pingback: fildena
Pingback: buy clomid for pct
Pingback: porn
Pingback: dapoxetine canada
Pingback: priligy generic
Pingback: cinrriplteia
Pingback: cenforce 200
Pingback: cenforce 100 bijwerkingen
Pingback: Cenforce
Pingback: web md vidalista
Pingback: amoxil 500 mg
Pingback: Buy Cheap clomid
Pingback: casino porna
Pingback: child porn
Pingback: garap
Pingback: tadalafil 20 mg best price
Pingback: levitra discount coupons
Pingback: porn
Pingback: Cenforce 200 side effects
Pingback: animal porn
Pingback: travesti.site
Pingback: bu site sitemap tarafından güncellenmiştir
Pingback: cenforce 200 gdzie kupić
Pingback: cenforce 200mg price in india
Pingback: order sildenafil 100mg sale
Pingback: mobil ödeme bozdurma
Pingback: child porn
Pingback: How effective is pull out method hydroxychloroquine sulfate tablet 200 mg?
Pingback: grandpashabet
Pingback: buy revatio online
Pingback: grandpashabet
Pingback: androgel price
Pingback: grandpashabet
Pingback: tadalista ct
Pingback: 40 mg vitamin c
Pingback: kamagra gold kamagra
Pingback: Bu website sitemap ile güçlendirilmiştir
Pingback: steroid fiyatları
Pingback: sms onay
Pingback: vidalista black cialis 80 mg
Pingback: steroid
Pingback: 1 androgel
Pingback: tadalista
Pingback: testosterone gel for females
Pingback: how to buy priligy in usa
Pingback: stromectol (3mg) 4 tabs
Pingback: revia alcohol
Pingback: levitra prices
Pingback: over the counter hydroxychloroquine substitute
Pingback: sms onay
Pingback: sikis
Pingback: atorvastatin 40
Pingback: buy lasix water pill
Pingback: kralbet
Pingback: buy hydroxychloroquine online india
Pingback: baywin
Pingback: yasam ayavefe techbullion.com
Pingback: dapoxetine and sildenafil tablets
Pingback: yasam ayavefe
Pingback: fuck google
Pingback: porn
Pingback: istanbul travesti
Pingback: vidalista kopen belgiГ«
Pingback: demre escort
Pingback: porno
Pingback: priligy over the counter - How do you make a man feel loved and respected?
Pingback: hd porno izle
Pingback: porno izleme sitesi
Pingback: Blog
Pingback: Opel Oto Çıkma
Pingback: çankırı escort
Pingback: datça escort
Pingback: escort
Pingback: Moda Danışmanı
Pingback: Yeni Başlayanlar
Pingback: Diyet Yolu
Pingback: gezginizm
Pingback: Güzellik Önerileri
Pingback: gaziosmanpaşa escort
Pingback: hatay escort
Pingback: karaman escort
Pingback: Can erectile dysfunction be a result of radiation therapy??
Pingback: lara escort
Pingback: Can erectile dysfunction be a symptom of Klinefelter syndrome in males??
Pingback: trabzon escort
Pingback: urfa escort
Pingback: demirözü escort
Pingback: porn
Pingback: metronidazole 400mg tablets
Pingback: reviews for vidalista compared to cialis
Pingback: What is the prescribed dosage for my medication adalafil 40 mg and dapoxetine 60 mg
Pingback: What is a GERD cough salbutamol inhaler
Pingback: izmir travesti
Pingback: What should you eat after taking antibiotics ivermectin pills
Pingback: izmir travesti
Pingback: How do you know if he plays hard to get vidalista tadalafil 20mg?
Pingback: How effective is pull out method ivermectin stromectol?
Pingback: Can bacterial diseases be transmitted through contact with contaminated surfaces in laboratories Zithromax used for?
Pingback: Which inhaler opens the airways alternative medicine for symbicort?
Pingback: How do you know your gut is unhealthy stromectol mites?
Pingback: sex
Pingback: Medications and Asthma Control - Breathing Freely with Confidence stromectol 12mg?
Pingback: Medications and Chronic Fatigue Management - Reinvigorating Energy Levels mens viagra pills?
Pingback: vip çeşme transfer
Pingback: çeşme transfer
Pingback: Medications and Mental Resilience - Embracing Challenges, Finding Strength symbicort inhaler for asthma 160/4.5?
Pingback: ventolin hfa prices?
Pingback: The Role of Medications in Managing Chronic Pain order lasix 40mg online?
Pingback: The Power of Telemedicine in Modern Healthcare buy sildenafil 50mg pill?
Pingback: Understanding Food Allergies and Intolerances vidalista professional sublingual?
Pingback: porn
Pingback: What is antibiotic resistance, and how can it be addressed caverta vs kamagra?
Pingback: What are the 6 types of quality control Cenforce 100mg pills?
Pingback: What is the most common male dysfunction what is Cenforce 100 review?
Pingback: How do you keep your man for ever oral Cenforce 100mg?
Pingback: Can regular exercise improve erectile function Cenforce 50mg cost?
Pingback: sikiş
Pingback: How are new developments in research impacting the treatment of Parkinson's disease ivermectin oral?
Pingback: Advances in Artificial Intelligence for Medical Diagnostics how long does kamagra 100 work?
Pingback: Medications and Sports-Related Injuries - Speeding Up Recovery ivermectin stromectol?
Pingback: porn
Pingback: Medications and Respiratory Health - Breathing Easy for a Healthier Life vidalista 20 side effects?
Pingback: child porn
Pingback: https://peptidci.com/enjeksiyon-steroidler
Pingback: porn
Pingback: https://peptidci.com/
Pingback: How can I stop impotence Cenforce online order?
Pingback: Teletherapy - Counseling in the Digital Age ivermectin 3mg tablets
Pingback: Medications and Lifestyle Changes: A Holistic Approach to Health ventolin hfa.
Pingback: porn
Pingback: How do I keep my husband interested in me order Cenforce generic??
Pingback: bağcılar escort
Pingback: porn
Pingback: child porn
Pingback: porn
Pingback: child porn
Pingback: xxlargeseodigi
Pingback: steroid satın al
Pingback: ivermectin drug
Pingback: sultanbeyli çilingir
Pingback: child porn
Pingback: ivermectin ebay
Pingback: steroid satın al
Pingback: child porn
Pingback: sms onay
Pingback: Kamagra tablets 100mg
Pingback: kamagra
Pingback: buying prescription drugs in mexico online
Pingback: fuck porn
Pingback: grandpashabet
Pingback: buy cytotec over the counter
Pingback: tekirdağ
Pingback: izmir escort
Pingback: ivermectin 90 mg
Pingback: ivermectin usa price
Pingback: canadian pharmacy 24h com safe
Pingback: How do you get rid of parasites in your body??
Pingback: reputable canadian online pharmacies
Pingback: Are carrots good for the liver??
Pingback: Premature ejaculation can have a significant impact on a man's quality of life and may lead to anxiety and depression.?
Pingback: azithromycin amoxicillin
Pingback: Sexual counseling can provide older men with information and support related to sexual health and function, as well as help them to develop strategies for managing PE.?
Pingback: meritking
Pingback: Can erectile dysfunction be a side effect of urethral valve ablation??
Pingback: Can banana boost sperm??
Pingback: What are the basics of quality??
Pingback: How many eggs left age 30??
Pingback: What causes twins to be born early??
Pingback: How to get a hard on at 60 no prescription cialis??
Pingback: meritking
Pingback: How can I get super hard naturally walgreens cialis cost??
Pingback: What causes intense chemistry with someone??
Pingback: Is antibiotic damage permanent?
Pingback: Can I take antibiotics an hour early?
Pingback: paxlovid covid
Pingback: Are antibiotics really necessary Azithromycin pneumonia?
Pingback: abortion pill online pharmacy?
Pingback: buy paxlovid online
Pingback: cvs pharmacy store number list?
Pingback: What is the newest inhaler for asthma?
Pingback: best india pharmacy
Pingback: cheapest online pharmacy india
Pingback: How to work out when you have asthma?
Pingback: What over the counter medicine works like prednisone?
Pingback: Can you get inhalers over the counter?
Pingback: What are the worst states to live in if you have COPD budesonide inhaler cost?
Pingback: Can antibiotics be used to treat infections in patients with infected biliary stents and cholangitis stromectol for lice?
Pingback: Can antibiotics be used to treat viral infections buy stromectol 3 mg online?
Pingback: my canadian pharmacy
Pingback: What is the best time of day to take a probiotic ivermectin paste?
Pingback: How does salt draw out infection ivermectin liquid for horses?
Pingback: where to buy prednisone in canada
Pingback: What are the caution while taking antibiotics ivermectin injectable?
Pingback: Can I stop antibiotics after 1 tablet stromectol tablets?
Pingback: Can antibiotics be used for antibiotic-associated diarrhea stromectol 12 mg?
Pingback: best pills for ed
Pingback: Meru University research projects
Pingback: How do you give pleasure in bed ivermectin pyrantel?
Pingback: Can antibiotics be used for E. coli infection?
Pingback: What's the difference between sperm and discharge stromectol dosage?
Pingback: How do I protect my gut when taking antibiotics buy stromectol 12mg?
Pingback: Can I drink the same day I took antibiotics?
Pingback: Are online pharmacies required to have proper packaging for medication
Pingback: Grandpashabet
Pingback: birth control pills prescription
Pingback: How long should a man last when making love buy hydroxychloroquine tablets
Pingback: Which gender sperm swims fastest
Pingback: How do I know if I have a parasitic infection (plaquenil) buy without prescription
Pingback: what does a albuterol inhaler do
Pingback: Is rice good for your liver - Stromectol 3mg pills
Pingback: How do I rebuild my immune system after antibiotics - where to buy hydroxychloroquine near me
Pingback: fildena uk | How long does it take for L-Arginine to work for ED
Pingback: propecia generic
Pingback: porn
Pingback: meritking
Pingback: Can over the counter medications cause drowsiness in infants. acid reflux medication over the counter
Pingback: When did the first man have a baby. levitra vs cialis
Pingback: cefadroxil 500mg capsules - How can I get rid of a bacterial infection fast
Pingback: Male breast cancer is often diagnosed at a later stage than in women, primarily due to a lack of awareness and delayed medical attention | flux research chems Nolvadex
Pingback: canlı sex hattı
Pingback: Inhaler innovation aims to reduce the carbon footprint of treatment
Pingback: Quel est le role des parents dans la famille
Pingback: How long do viral infections last without antibiotics?
Pingback: How can I get antibiotics without seeing a doctor?
Pingback: Do all men become impotent - kamagra 100mg oral jelly for sale
Pingback: How do you know if a girl is taken - anti viagra pills
Pingback: sms onay
Pingback: Can cholesterol levels be reduced by consuming almonds or almond butter
Pingback: Can incorporating regular meditation or mindfulness practices help improve heart health and reduce the risk of heart disease
Pingback: child porn
Pingback: How does the use of certain antipsychotic medications affect ovulation?
Pingback: Can certain herbal remedies or natural supplements, such as black cohosh or evening primrose oil, support female fertility?
Pingback: Persistent lack of energy can disrupt sleep patterns and contribute to insomnia or disrupted sleep quality?
Pingback: Reduced hair growth rate and slower hair regrowth can be experienced by individuals with an underactive thyroid?
Pingback: How do stop your period | can you vhew vidalista 10mg
Pingback: How will u know if a guy loves u: vidalista pills 60mg
Pingback: How do you make a man fall crazy in love with you | web md vidalista
Pingback: Quelle est la cle du bonheur familial acheter cialis 20mg tadalafil lilly
Pingback: Quelles sont les caracteristiques d'une bonne famille | acheter cialis en ligne avec ordonnance
Pingback: grandpashabet
Pingback: Quelles sont les qualites d'une bonne famille viagra online
Pingback: Why is antibacterial soap not recommended?
Pingback: Is tomatoes good for liver?
Pingback: What drugs should not be taken with amoxicillin?
Pingback: How does diabetes impact the risk of developing heart disease: atorvastatin price walmart
Pingback: side effects of synthroid 25 | Are there any exercises or drills to help increase speech rate
Pingback: Quels sont les problemes de la famille - tadalafil teva 20 mg
Pingback: Comment reconnaitre une famille dysfonctionnelle prix d une boite de viagra en pharmacie
Pingback: buy ciprofloxacin tablets
Pingback: buy cipro
Pingback: canadianpharmacyworld
Pingback: vipspark.vipspark.ru
Pingback: psychophysics.ru
Pingback: vitaliy-abdulov.ru
Pingback: video.vipspark.ru
Pingback: Inhalers and travel: what to pack and how to use them | where to buy ventolin inhalers without a prescription
Pingback: cheap doxycycline tablets
Pingback: meritking giriş
Pingback: doxycycline minocycline
Pingback: film.poip-nsk.ru - film online
Pingback: poip-nsk.ru - Movie Watch
Pingback: What is the difference between heart failure and congestive heart failure chlorthalidone 25 mg es para que sirve
Pingback: What is the best position to sleep in with high blood pressure furosemide 20 mg tablets
Pingback: canadian pharmacy no prescription
Pingback: Why do I get a tickle in my throat and can't stop coughing ventolin inhaler dosage?
Pingback: fuck google
Pingback: How long does it take albuterol to clear your system | can you take stolt with ventolin
Pingback: At what heart rate should you start CPR lasix and hyponatremia?
Pingback: How long can you be on a steroid inhaler buy ventolin inhaler
Pingback: Is Primatene Mist as good as albuterol is ventolin just albuterol
Pingback: Viagra Pfizer sans ordonnance
Pingback: Why can't I breathe even with inhaler albuterol inhaler
Pingback: ed medicines
Pingback: golf speaker
Pingback: Quelle est la valeur d'une maman tadalafil 5 mg
Pingback: How long does a bacterial infection last - ivermectin cream for rosacea
Pingback: stromectol cvs What to avoid while on antibiotics?
Pingback: earbuds
Pingback: bit.ly/pamfir-pamfir-2023-ua-pamfir
Pingback: Do antibiotics heal everything
Pingback: Treblab - speaker stands
Pingback: studio-tatuage.ru
Pingback: yug-grib.ru
Pingback: Should antibiotics be taken for 3 or 5 days
Pingback: Can antibiotics do more harm than good
Pingback: Is milk OK with antibiotics
Pingback: ipsychologos
Pingback: What are 3 problems with antibiotics
Pingback: Can antibiotics make me feel sick
Pingback: porn
Pingback: Äèçàéí ÷åëîâåêà
Pingback: What to avoid when taking antibiotics
Pingback: viagra for men over 70
Pingback: pastillas levitra
Pingback: Can I take amoxicillin 500mg twice a day
Pingback: levitra vardenafil
Pingback: Is oatmeal a prebiotic stromectol for scabies merck
Pingback: Which antibiotic is safest for liver
Pingback: madridbet
Pingback: How do you know if you need antibiotics
Pingback: What is the safest antibiotic
Pingback: meritking
Pingback: What can easily cure infection
Pingback: What is the 3 day antibiotic
Pingback: What kills bacteria inside the body
Pingback: How many antibiotics can I take in a day
Pingback: 2023
Pingback: How do you know if your body is fighting an infection
Pingback: Should I drink a lot of water with antibiotics
Pingback: What lack of vitamin causes fatigue z-pack antibiotic cost
Pingback: What are some natural anti inflammatories ivermectin pour on for cattle
Pingback: What are signs of strong immune system salix furosemide for horses
Pingback: viagra sans ordonnance forum - Fait-il lever les jambes pour tomber enceinte?
Pingback: madridbet
Pingback: What is the liquid that comes out before sperm stromectol cost
Pingback: https://tinyurl.com/2lacn6n3
Pingback: What is Deming best known for?
Pingback: vsovezdeisrazu
Pingback: Can a woman impregnate herself?
Pingback: How do doctors test if a man is infertile?
Pingback: What makes a man love a woman?
Pingback: What spices contain lead what is stromectol 3 mg used for?
Pingback: Which sperm is more powerful?
Pingback: How do you love a man physically
Pingback: order femara 2.5 mg online cheap
Pingback: Quel sont les 4 types de famille parapharmacie leclerc
Pingback: madridbet
Pingback: Quand la famille devient toxique pharmacie en ligne avec ordonnance
Pingback: cheapest generic levitra
Pingback: elizavetaboyarskaya.ru
Pingback: kamagra 100mg preis Ist Honig wie Viagra
Pingback: Zithromax z pak online Should I take probiotics every day with antibiotic
Pingback: vidalista 20 usa purchase sildenafil
Pingback: Cialis price cvs How long does premature ejaculation usually last - ScwCMD
Pingback: where can i get generic propecia without rx
Pingback: How do I know if my liver is detoxing oral Ivermectin for rosacea
Pingback: Do you do CPR if there is a pulse but no breathing Lisinopril
Pingback: Does insurance pay for depression
Pingback: batmanapollo psychologist
Pingback: How to make homemade saline solution for nebulizer
Pingback: Is 8 days of antibiotics enough
Pingback: batmanapollo.ru - psychologist
Pingback: How do I make my liver healthy again
Pingback: cialis without a doctor prescription
Pingback: batmanapollo
Pingback: What does taking turmeric daily do what is hydroxychloroquine prescribed for
Pingback: kinokrad
Pingback: viagra users comments
Pingback: Can I drink 2 days after antibiotics hydroxychloroquine 200 mg tab
Pingback: How do you make a man miss you in bed viagra 100mg price per pill
Pingback: How do I know if I have a parasitic infection z pack 500 mg dosage
Pingback: What gets rid of parasites naturally azithromycin 250 mg
Pingback: sildenafil 100 mg side effects
Pingback: canadian drugs online
Pingback: best ed treatment
Pingback: How do you know if your liver is struggling likes amoxicillin
Pingback: Who fathered the most children cialis 800mg black for sale
Pingback: tretinoin over the counter acne
Pingback: How do I show my boyfriend I love him physically dapoxetine 90mg sale
Pingback: What causes intense chemistry with someone fildena 100mg reviews
Pingback: How do you turn the tables and make him chase you viagra or kamagra or cialis
Pingback: What are the early warning signs of sepsis or stromectol 0.5 mg
Pingback: What is GREY discharge without hydroxychloroquine for sale online
Pingback: What is true love between a man and a woman levitra for sale online
Pingback: What stops people from going to the gym cenforce us
Pingback: Which alcohol to drink when you're on antibiotics with hydroxychloroquine lupus dose
Pingback: What can chlamydia do to your body if left untreated with plaquenil vs hydroxychloroquine
Pingback: How painful is a terminal illness likes hydroxychloroquine over the counter nz
Pingback: Is turmeric good for liver or define hydroxychloroquine
Pingback: Is pasta good for liver and ivermectin 3mg tablets
Pingback: How do I know if I need antibiotics and ivermectin tablet 1mg
Pingback: How can I make my partner feel special everyday priligy 60mg oral
Pingback: buy dapoxetine 30mg online
Pingback: cost of ivermectin 1% cream
Pingback: viagra kamagra
Pingback: How do you make your man loves you more sildenafil 25?
Pingback: can you buy zithromax online
Pingback: How do you tell if a girl is playing hard to get sildenafil 100mg for sale?
Pingback: How do I last in bed naturally sildenafil generic brands?
Pingback: over the counter medication for uti
Pingback: What is the leading killer of men cost tadalafil generic?
Pingback: 123movies
Pingback: over the counter inhaler walmart
Pingback: xnxx
Pingback: 9xflix
Pingback: x
Pingback: https://gdznew.ru/
Pingback: canadian pharmacies selling viagra
Pingback: what is vardenafil 20mg
Pingback: madridbet
Pingback: buy cipro online canada
Pingback: Dope prescribing information. Long-Term Effects. avodart cost canada?
Pingback: fuck google
Pingback: canadian drugs pharmacy
Pingback: big pharmacy online
Pingback: porno izle
Pingback: sikiş
Pingback: türk porno seks
Pingback: Meritking
Pingback: https://bitbin.it/X5y9A1Fd/
Pingback: https://bitbin.it/yeCU06m7/
Pingback: 2022-film
Pingback: madridbet
Pingback: https://bit.ly/n39i18b
Pingback: https://bit.ly/okaybaybay
Pingback: Pills information. What side effects can this medication cause? abilify dosage?
Pingback: porno usa
Pingback: fildena buy online
Pingback: Drug prescribing information. Name brand names. paxil vs paxil cr dosage?
Pingback: klondayk2022
Pingback: irannews.ru
Pingback: Pills information. What side effects? avodart 0.5 mg price in india?
Pingback: uluro-ado
Pingback: rusnewsweek
Pingback: 24hours-news
Pingback: icf
Pingback: What are the 4 quality indicators viagra over the counter united states for sale?
Pingback: www
Pingback: bep5w0Df
Pingback: How often should I go to the gym can i get pregnant if my husband uses viagra?
Pingback: grandpashabet
Pingback: What did Melissa Mccarthy use to lose weight and a where to buy hoodia gordonii?
Pingback: bit.ly/3GQNK0J
Pingback: bit.ly/3ig2UT5
Pingback: bit.ly/3ARFdXA
Pingback: bit.ly/3gGFqGq
Pingback: bit.ly/3OEzOZR
Pingback: What can I drink to stop smoking generic for wellbutrin?
Pingback: Can erectile dysfunction go back to normal and kamagra gold 100?
Pingback: matchonline2022.ru
Pingback: cialis after prostate surgery
Pingback: cttdu.ru
Pingback: 1c789.ru
Pingback: sitestats01
Pingback: grandpashabet
Pingback: how to buy propecia cheap
Pingback: propecia nz buy
Pingback: site 2023
Pingback: brutv
Pingback: tftl.ru
Pingback: edu-design.ru
Pingback: newsukraine.ru
Pingback: history-of-ukraine.ru news ukraine
Pingback: mb588.ru
Pingback: 3o9cpydyue4s8.ru
Pingback: kin0shki.ru
Pingback: hydroxychloroquine where to buy
Pingback: https://clck.ru/32JaEo
Pingback: dolpsy.ru
Pingback: https://bitbin.it/JI5X9Xvu/
Pingback: https://bitbin.it/bn1QAiBO/
Pingback: madridbet
Pingback: rftrip.ru
Pingback: wwwi.odnoklassniki-film.ru
Pingback: 3DGofO7
Pingback: 3SoTS32
Pingback: 000-1
Pingback: psy-news.ru
Pingback: socionika-eniostyle.ru
Pingback: sezons.store
Pingback: video-2
Pingback: link
Pingback: TwnE4zl6
Pingback: Dim Drakona 2022
Pingback: Usik Dzhoshua 2 2022
Pingback: A片
Pingback: psikholog moskva
Pingback: ìûøëåíèå
Pingback: aOuSjapt
Pingback: JGXldbkj
Pingback: Dom drakona
Pingback: sY5am
Pingback: stat.netstate.ru
Pingback: confeitofilm
Pingback: rodnoe-kino-ru
Pingback: filmgoda.ru
Pingback: cleantalkorg2.ru
Pingback: tadalafil at walmart
Pingback: smotret-polnyj-film-smotret-v-khoroshem-kachestve
Pingback: liusia-8-seriiaonlain
Pingback: walmart cialis prices
Pingback: film
Pingback: viagra cialis
Pingback: video
Pingback: web
Pingback: buy stromectol 6 mg tablets
Pingback: revatio
Pingback: Ukraine-war
Pingback: UKRAINE
Pingback: stats
Pingback: viagra
Pingback: site
Pingback: buy stromectol 3mg online
Pingback: School of Pure and Applied Sciences Embu University
Pingback: University of Embu
Pingback: stromectol use on humans tracor supply
Pingback: ivermectine usa
Pingback: https://bit.ly/psikholog-muzhchina-onlayn
Pingback: Psikholog
Pingback: stromectol pill price
Pingback: 3NOZC44
Pingback: Øêàëà òîíîâ
Pingback: SHKALA TONOV
Pingback: https://ria.ru/20100906/272903623.html
Pingback: http://bit.ly/odna-film
Pingback: D6tuzANh
Pingback: qQ8KZZE6
Pingback: DPTPtNqS
Pingback: ivermectin 500ml
Pingback: bahis siteleri
Pingback: psy online
Pingback: slovar po psihoanalizu laplansh
Pingback: online moskva psiholog
Pingback: stromectol tab 3mg
Pingback: psy-
Pingback: stromectol tablete cena
Pingback: Netflix
Pingback: levitra or cialis which is better
Pingback: viagra discount
Pingback: what worms does ivermectin kill in dogs
Pingback: generic cialis uk cost
Pingback: price of cialis 20 mg
Pingback: buy cheap prescription drugs online
Pingback: canadian pharmacy online
Pingback: hydroxychloroquine 200 mg tablet
Pingback: ivanesva
Pingback: discount prescription drugs
Pingback: XVIDEOSCOM Videos
Pingback: Xvideos
Pingback: kinoteatrzarya.ru
Pingback: 9-05-2022
Pingback: top ed pills
Pingback: ivermectin ear mites
Pingback: Bubble hash
Pingback: Litto
Pingback: Moroccan hash
Pingback: Bubble hash
Pingback: pyrantel vs ivermectin
Pingback: Haupia strain
Pingback: gRh9UPV
Pingback: Watermelon haupia
Pingback: filmfilmfilmes
Pingback: Watermelon haupia
Pingback: mazhor4sezon
Pingback: ivermectin lice treatment
Pingback: Pinball machines for sale
Pingback: premature ejaculation
Pingback: ivermectin ingredients for humans
Pingback: treatments for ed
Pingback: Technology News
Pingback: child porn
Pingback: ivermectin 50ml
Pingback: stromectol 0.5 mg
Pingback: cryptocurrency credit card
Pingback: clomid 50mg tablets
Pingback: Canada
Pingback: how to increase penis size
Pingback: clomid prescription price
Pingback: how to use thrusting sucking rabbit vibrator
Pingback: best clomid brand
Pingback: canadianpharmacyking
Pingback: scrap car pick up
Pingback: Google
Pingback: cialis walmart
Pingback: Erectile Dysfunction pills for sale
Pingback: anita
Pingback: stock market explained
Pingback: best canadian pharmacy for cialis
Pingback: it doktor jona
Pingback: cock extension
Pingback: Takeaway
Pingback: ivermectin 0.1 uk
Pingback: ps5 sale
Pingback: stromectol generic name
Pingback: BERETTA 92X FOR SALE
Pingback: flccc ivermectin prophylaxis
Pingback: car recycling
Pingback: Krt carts
Pingback: business in canada
Pingback: cheap doxycycline tablets
Pingback: hydroxychloroquine pronunciation
Pingback: review buy cialis online
Pingback: ivermectin 6mg dosage
Pingback: marijuana-us.com
Pingback: Uganda safari holidays
Pingback: PlayStation 5 Digital Edition
Pingback: lucky land
Pingback: who makes cialis
Pingback: 5.56 green tips
Pingback: soap packaging
Pingback: madridbet
Pingback: how to stimulate the clitoris using clit vibrator
Pingback: best masturbation sleeves
Pingback: Herbal incense near me
Pingback: Herbal Incense Near me
Pingback: cz bren 2 for sale
Pingback: pc software full download
Pingback: jupiler
Pingback: pc games for windows xp
Pingback: MFT
Pingback: games for pc download
Pingback: free download for pc windows
Pingback: laptop app free download
Pingback: full apps download
Pingback: app download for pc
Pingback: pc apps free download
Pingback: donaarepa
Pingback: glo carts fake
Pingback: flccc ivermectin prophylaxis
Pingback: butt plug review
Pingback: buy stromectol online uk
Pingback: what is ivermectin for dogs
Pingback: eurocasino
Pingback: eurocasino
Pingback: buy stromectol uk
Pingback: bitcoin virtual card
Pingback: sisli escort
Pingback: ivermectin fda
Pingback: lasix tablets online
Pingback: buy lasix 40 mg uk
Pingback: meritking
Pingback: meritroyalbet
Pingback: japan ivermectin
Pingback: cheap ivermectin
Pingback: prostate massage orgasm
Pingback: Glock 34
Pingback: ivermectin 1%cream
Pingback: celebrex platelet effect
Pingback: ivermectin 12mg tablets for human
Pingback: ivermectin 6mg tablets for human
Pingback: palladium ore
Pingback: walther p38 handguns for sale
Pingback: ivermectin 0.5% lotion
Pingback: cefpodoxime
Pingback: augmentin antibiotic
Pingback: ciprofloxacin dogs
Pingback: how long does it take for viagra to kick in
Pingback: flagyl medication
Pingback: ivermectin 1 cream 45gm
Pingback: ciprofloxacin nausea
Pingback: ivermectin 3 mg tabs
Pingback: augmentin 500mg
Pingback: PS5 for Sale
Pingback: doxycycline 100mg tablets
Pingback: how is ivermectin made
Pingback: ivermectin price comparison
Pingback: stromectol 3 mg dosage
Pingback: average cost of cialis prescription
Pingback: how to buy cialis without prescription
Pingback: stromectol dosage scabies
Pingback: ivermectin 2mg
Pingback: cefdinir fatigue
Pingback: medical keflex
Pingback: clindamycin taste
Pingback: generic for cialis
Pingback: generic viagra online purchase
Pingback: azithromycin schwangerschaft
Pingback: generic cialis
Pingback: where can you get cialis
Pingback: best online casinos usa
Pingback: buy ivermectin fitness
Pingback: ivermectin lotion for lice
Pingback: tiktok video downloader
Pingback: ivermectin cost canada
Pingback: where can you buy ivermectin
Pingback: ivermectin msds
Pingback: cialis professional
Pingback: trcasino
Pingback: real money slots
Pingback: cialis pills
Pingback: buy viagra online india
Pingback: steroid side effects
Pingback: ivermectin 6mg dosage
Pingback: casino
Pingback: meritroyalbet
Pingback: best tadalafil
Pingback: tadalafila
Pingback: how to use a g spot remote controlled vibrator
Pingback: realistic male masturbator
Pingback: molnupiravir price
Pingback: molnupiravir same as ivermectin
Pingback: lifelike dildo
Pingback: cialis no prescription canada
Pingback: 3pericles
Pingback: Buy DMT online Victoria Australia
Pingback: tadalafil 80mg online pharmacy no prescription
Pingback: buy prednisone uk
Pingback: side effects of prednisone 20mg tablets
Pingback: cialis with dapoxetine
Pingback: tombala siteleri
Pingback: can you buy cialis without a prescription
Pingback: cialis with dapoxetine
Pingback: cheap generic sildenafil pills
Pingback: sildenafil pills
Pingback: ivermectin
Pingback: Hk vp9 for sale
Pingback: canadian drug pharmacy
Pingback: cialis reviews
Pingback: tadalafil warnings
Pingback: สมัคร lottovip
Pingback: cheap generic sildenafil pills
Pingback: Buy Marijuana Online
Pingback: baymavi
Pingback: baymavi
Pingback: canadian cialis
Pingback: canadian pharmacy cialis
Pingback: goodrx tadalafil
Pingback: where to buy ivermectin pills
Pingback: glock 43x for sale
Pingback: 5 mg cialis
Pingback: generic viagra online purchase in usa
Pingback: generic cialis buy uk
Pingback: ivermectin 0.1
Pingback: how to buy viagra online canada
Pingback: cost of ivermectin
Pingback: buy bulk ammo
Pingback: provigil online uk
Pingback: tadalafil price
Pingback: meritroyalbet
Pingback: generic for cialis
Pingback: prednisone 40mg for sale
Pingback: cheap tadalafil
Pingback: ivermectin treatment for covid
Pingback: meritking
Pingback: Scrap Car Removal Richmond
Pingback: buy ivermectin canada
Pingback: ignition casino usa
Pingback: where to get ivermectin
Pingback: order viagra cialis canada
Pingback: stromectol coronavirus
Pingback: where can i get ivermectin
Pingback: order ivermectin
Pingback: ivermectin uk
Pingback: Virtual Visa Card
Pingback: ivermectin ontario
Pingback: how much does ivermectin cost
Pingback: Anonymous
Pingback: Tegretol
Pingback: generic stromectol
Pingback: ivermectin lice oral
Pingback: ivermectin 8000 mcg
Pingback: Anonymous
Pingback: cost of ivermectin 1% cream
Pingback: canadian meds
Pingback: ivermectin 6 mg tablets
Pingback: ivermectin buy nz
Pingback: Taurus 9mm
Pingback: stromectol cvs
Pingback: 5 mg nolvadex
Pingback: ivermectin ivermectinst
Pingback: flccc ivermectin
Pingback: tizanidine buy
Pingback: Anonymous
Pingback: meritroyalbet
Pingback: chloroquine online
Pingback: clomid 25
Pingback: clomid online order
Pingback: sextoys online
Pingback: molnupravir
Pingback: push health ivermectin
Pingback: flccc ivermectin
Pingback: tombala siteleri
Pingback: tombala siteleri
Pingback: tombala siteleri
Pingback: ventolin inhaler
Pingback: trcasino
Pingback: ivermectin 3mg tablet
Pingback: ivermectin humans
Pingback: cheapest generic viagra
Pingback: sildenafila
Pingback: cialis pills for sale in usa
Pingback: USD to cryptocurrency
Pingback: ivermectin 6mg tablet for lice
Pingback: can you buy cialis over the counter in canada
Pingback: trcasino
Pingback: elexusbet
Pingback: ivermectin virus
Pingback: Bitcoin address wallet
Pingback: vcialis
Pingback: madridbet
Pingback: meritking
Pingback: meritroyalbet
Pingback: Kilimanjaro Trek
Pingback: cheap viagra online canadian pharmacy
Pingback: adam and eve couple sex toys
Pingback: difference between cialis and viagra
Pingback: pharmacy cheap no prescription
Pingback: mobic generic cost
Pingback: best vibrators to travel with
Pingback: buy vyvanse online without prescription
Pingback: what are the side effects of generic viagra
Pingback: who invented viagra
Pingback: Lioresal
Pingback: Eskalith
Pingback: male viagra pill walmart
Pingback: stromectol buy uk
Pingback: ghb 99%
Pingback: krt cart
Pingback: asic bitcoin miners for sale
Pingback: viagra 25mg cost
Pingback: buy generic cialis canada
Pingback: free cialis
Pingback: Krt disposable vape
Pingback: vape carts
Pingback: online cialis prescription
Pingback: mossberg 930 jm pro for sale
Pingback: beretta brigadier for sale
Pingback: tudor north flag for sale
Pingback: ed drugs compared
Pingback: non prescription erection pills
Pingback: keltec sub 2000
Pingback: clitoris vibrator
Pingback: best adam and eve vibrators
Pingback: adam and eve sex toys
Pingback: viagra plus
Pingback: HELEX PILLS
Pingback: meritroyalbet
Pingback: Yamaha R3
Pingback: best university in kenya
Pingback: buy real and registered driving license
Pingback: butt plug review
Pingback: big black dildo
Pingback: rechargeable vibrators
Pingback: stromectol 3 mg tablet
Pingback: how to use a g spot massager
Pingback: crock ruger arms
Pingback: online marketing
Pingback: Независимое бюро информации и аналитики
Pingback: azithromycin tablets
Pingback: beezle sauce pens
Pingback: cigars for sale UK
Pingback: buy cialis online cheap
Pingback: cialis prices walmart
Pingback: cialis pills india
Pingback: Spray Painting
Pingback: Buy Oxycodone online
Pingback: buy gbl online europe
Pingback: Buy Gamma - Butyrolactone (GBL) online
Pingback: ivermectin 90 mg
Pingback: Source
Pingback: Mexicana magic mushrooms
Pingback: eurocasino
Pingback: eurocasino
Pingback: meritroyalbet
Pingback: madridbet
Pingback: eurocasino
Pingback: ivermectin syrup
Pingback: elexusbet
Pingback: meritking
Pingback: mp5 sale
Pingback: BUY GUNS ONLINE
Pingback: plaquenil medication
Pingback: guns for sale in European union
Pingback: viagra 25 mg kaufen
Pingback: food delivery restaurants
Pingback: how much do 5 milligram tablets of cialis cost in italy
Pingback: sig legion
Pingback: stizzy pod
Pingback: ivermectin 3mg tablets price
Pingback: taurus th40 compact
Pingback: uberti dalton
Pingback: ivermectin 1 cream
Pingback: henry lever 45/70
Pingback: bathmate
Pingback: generic plaquenil prices
Pingback: - do si dos strain
Pingback: bathmate
Pingback: kimber rifles
Pingback: buy plaquenil 0.5
Pingback: disposable ecigs
Pingback: buy gbl 100ml
Pingback: sodium pentobarbital for sale
Pingback: buy real driving license uk
Pingback: cialis to buy
Pingback: Uganda Safaris Tours
Pingback: cialis dosage frequency
Pingback: beretta 1301 tactical for sale
Pingback: viagra 100mg price per pill
Pingback: DailyCBD
Pingback: browning micro midas 20 gauge
Pingback: Psilocybe Cubensis
Pingback: walther ppk in 9mm
Pingback: cialis side effects dangers
Pingback: vibrators
Pingback: pleasure kits
Pingback: normal dosage of cialis
Pingback: cheap online generic drugs
Pingback: the year without a santa claus
Pingback: Methadone for sale
Pingback: generic drugs online
Pingback: generic drugs online
Pingback: maybe this time
Pingback: The Bombay Flying Club
Pingback: Limdabara Primary Shala Dahod, Limdabara, Dohad - 389151
Pingback: Mhalasakant Mad High Vidyalay Sant Tukaram Udyan, Pune - 411044
Pingback: group sex games spin the bottle
Pingback: affordable solar panels
Pingback: solar powered generator
Pingback: camping solar panels
Pingback: e-cigs for sale missouri
Pingback: ruger guns for sale
Pingback: affiliate marketing millionaire
Pingback: realest looking fake money
Pingback: white hennessy for sale near me
Pingback: price of medicine valtrex
Pingback: russian names for girls
Pingback: virtual card buy with bitcoin
Pingback: virtual credit card buy with cryptocurrency
Pingback: happyruck
Pingback: TÜM HABERLER
Pingback: happyruck
Pingback: Uganda Gorilla Trekking Budget
Pingback: Buy Stiizy Biscotti (500mg)
Pingback: CableFreeTV Tech News
Pingback: how much is valtrex
Pingback: sildenafil 25 mg
Pingback: avalon-miner-1166-pro-81-th-s-for-sale
Pingback: valtrex medicine purchase
Pingback: buying valtrex
Pingback: CRYPTO MINING FOR SALE
Pingback: bathmate
Pingback: Buy Hynidate 10mg Online
Pingback: tadalafil dosage recommendations
Pingback: how to buy albuterol
Pingback: Car rentals Montenegro
Pingback: ivermectin 50 mg
Pingback: provigil
Pingback: over counter viagra alternative walgreens
Pingback: cialis wikipedia
Pingback: priligy tablets us
Pingback: buy prednisone
Pingback: best testosterone booster
Pingback: gabapentin 31
Pingback: zithromax 500mg
Pingback: viagra from canada
Pingback: where to buy a juul
Pingback: proventil albuterol
Pingback: how to buy stromectol
Pingback: modafinil good rx
Pingback: buy avana 200 mg
Pingback: prednisone oral
Pingback: where can i buy counterfeit money
Pingback: quineprox 40
Pingback: neurontin drug
Pingback: buy viagra online
Pingback: online casinos internet casino
Pingback: lasix cost
Pingback: amoxil 500mg
Pingback: stromectol south africa
Pingback: ivermectin 400 mg brands
Pingback: ivermectin 4 tablets price
Pingback: happyLuke
Pingback: MUT
Pingback: prednisone 4 mg daily
Pingback: prednisone 5084
Pingback: buy prednisone without prescription paypal
Pingback: raw garden carts
Pingback: canadian pharmacies
Pingback: blackwater Og Big Chief
Pingback: srpc93
Pingback: remington v3 timber
Pingback: Apetamin Syrup 200ml Online
Pingback: strokers
Pingback: anti fungal pills without prescription
Pingback: stroker toy
Pingback: ltakside sikin beni
Pingback: buy real viagra no prescription
Pingback: sig sauer handguns
Pingback: raw garden extract cartridges
Pingback: tadalafil without a doctor's prescription
Pingback: azithromycin otc cvs
Pingback: premium guns for sale
Pingback: savage grow plus amazon
Pingback: Uganda safaris
Pingback: pet meds without vet prescription
Pingback: Uganda Safari Holidays
Pingback: azithromycin otc
Pingback: breaking news in Nairobi
Pingback: bitcoin
Pingback: cost of ivermectin 1% cream
Pingback: dizziness
Pingback: Order Sig Sauer Guns And Magazines Online
Pingback: ivermectin lotion price
Pingback: Briscoe Primary School and Nursery
Pingback: RissMiner
Pingback: pills for sale in uk
Pingback: 100 mg prednisone daily
Pingback: prednisone for dogs
Pingback: stock trading 101
Pingback: how can i get prednisone
Pingback: Beretta 92fs
Pingback: G17 GEN 4 MOS STANDARD | 9X19MM
Pingback: tamoxifen for gynecomastia reviews
Pingback: شركة تسويق
Pingback: how to lose weight on tamoxifen
Pingback: tamoxifen cyp2d6
Pingback: buy hex dumbbells
Pingback: gigabyte d33006
Pingback: Murchison falls national park
Pingback: ethereum mining machine for sale in europe
Pingback: cialis pills for sale uk
Pingback: sugar gliders for sale
Pingback: buy weed online australia
Pingback: bohemian coffee table
Pingback: dapoxetine sildenafil brands
Pingback: cialis for sale in london
Pingback: Macaw for sale
Pingback: smith and wesson arms
Pingback: beretta 92 compact
Pingback: arabian sand boa
Pingback: can lisinopril be taken with grapefruit juice
Pingback: smart carts
Pingback: erection pills
Pingback: ed pills amazon
Pingback: viagra without a prescription
Pingback: stromectol buy online
Pingback: where to buy ivermectin lotion
Pingback: background check
Pingback: top shelf weed
Pingback: how much ivermectin to give a dog with sarcoptic mange
Pingback: order viagra south africa
Pingback: zithromax online bestellen zonder recept
Pingback: the best ed pills
Pingback: super cialis cheap
Pingback: dosage for prednisone 20mg
Pingback: magic mushrooms
Pingback: magic mushrooms
Pingback: stiiizy-battery near me/
Pingback: pentobarbital for sale
Pingback: who owns hydroxychloroquine
Pingback: mossberg mvp 308 stock for sale
Pingback: hudson shuffleboards for sale
Pingback: taurus g3c sale
Pingback: durvet ivermectin pour on for cattle
Pingback: p320 m17
Pingback: colt 45 cattleman revolver
Pingback: ivermectin for humans walmart
Pingback: savage 110 tactical
Pingback: cheap stromectol tablets
Pingback: CANNABIS PUFF BAR
Pingback: how much viagra should i take the first time?
Pingback: Buy Ketamine online
Pingback: salbutamol nebulizer price
Pingback: how much does a viagra prescription cost
Pingback: ivermectin scabies
Pingback: ivermectin paste 1.87 for horses
Pingback: hydroxychloroquine zinc and zithramax reddit
Pingback: ivermectin dosage humans
Pingback: myloweslife.com
Pingback: izrada web sajtova
Pingback: cialis without a perscription
Pingback: soolantra ivermectin
Pingback: cialis and alcohol symptoms
Pingback: what is better viagra or cialis
Pingback: buy generic cialis from india
Pingback: stromectol teva 3109
Pingback: cialis 5 mg online
Pingback: aromatherapy for sleep
Pingback: ارقام بنات
Pingback: Serengeti safari
Pingback: shipping containers for sale
Pingback: doxycycline 150 mg
Pingback: FARMING EQUIPMENT FOR SALE IN KZN
Pingback: best male sex toys
Pingback: generic doxycycline
Pingback: prednisone 20 mg in india
Pingback: doxycycline hydrochloride 100mg
Pingback: bujagali falls white water rafting
Pingback: where to buy ivermectin
Pingback: Macbook akku service rapperswil
Pingback: Kenya safari Masai Mara
Pingback: Livestock for sale
Pingback: Macbook akku service
Pingback: GOLF CARTS FOR SALE
Pingback: buy real propecia
Pingback: can you get high off of amoxil
Pingback: MacBook Repair Bridgwater
Pingback: Sig Sauer Gunshop
Pingback: Agence de publicite
Pingback: cialis pills sale uk
Pingback: Capuchin Monkey For Sale near me
Pingback: ampicillin drug study
Pingback: mp3 dowload
Pingback: download free apps apk for windows
Pingback: pc software full download
Pingback: free download for pc windows
Pingback: 1
Pingback: free download for windows 7
Pingback: can you buy cialis over the counter in canada
Pingback: free download for windows 10
Pingback: pc games for windows xp
Pingback: apps for pc download
Pingback: venlafaxine vs duloxetine
Pingback: stromectol mouth sores
Pingback: بديل تروكولر
Pingback: aranżacja wnętrz Gdynia
Pingback: cheapest brand cialis online
Pingback: sex toy review
Pingback: giving blowjob
Pingback: canada pharmacy
Pingback: Whalley Range
Pingback: can buy cialis uk
Pingback: where can i buy cialis
Pingback: ADDERALL FOR SALE
Pingback: Friesian horse for sale
Pingback: African gray for sale
Pingback: cialis official website
Pingback: snorting lexapro
Pingback: napalm og big chief
Pingback: pills for erection
Pingback: nenuco
Pingback: Diablo strain
Pingback: buy cheap prescription drugs online
Pingback: erythromycin for dogs
Pingback: the luck force talisman
Pingback: ivermectin online
Pingback: buy 400 mg hydroxychloroquine online
Pingback: atorvastatin side effects muscle pain
Pingback: dapoxetine for bph insurance coverage
Pingback: ivermectin lotion cost
Pingback: losartan potassium and hydrochlorothiazide
Pingback: long term side effects of acyclovir
Pingback: 피망슬롯머니
Pingback: duloxetine hcl dr caps 60mg
Pingback: 메이저놀이터
Pingback: best online pharmacies in canada
Pingback: ruger sp101 for sale
Pingback: switching from lexapro to zoloft
Pingback: stromectol tablet price
Pingback: sachdeva millennium school agra
Pingback: ed pills from canada
Pingback: w88
Pingback: realistic male stroker
Pingback: what is seroquel prescribed for
Pingback: sex toy review
Pingback: zoloft benefits
Pingback: stromectol meaning
Pingback: vibrating penis rings
Pingback: sex toy facts
Pingback: prilosec headaches
Pingback: pocket vagina
Pingback: dosage of metronidazole for men
Pingback: what is atorvastatin calcium for
Pingback: https://amarketjournal.com/2021/09/01/there-are-the-advanced-features-to-download-twitter-video-online/
Pingback: Ctrlcoin.io - Peer-to-Peer (P2P) Crypto Exchange
Pingback: melhores telemóveis
Pingback: film streaming
Pingback: best time of day to take norvasc
Pingback: film streaming 2021
Pingback: vehicle repatriation
Pingback: streamcomplet
Pingback: cheap tadalafel online canadian pharmacy
Pingback: how to use sildenafil 100mg
Pingback: sefakoy escort
Pingback: cryptocurrency 99defi
Pingback: Dank Vapes
Pingback: داستان سکسی تصویری
Pingback: giant dildo
Pingback: how to use the best realistic dildo
Pingback: prednisone 40 mg
Pingback: pocket stroker
Pingback: prostate milking vibrators
Pingback: viagra cream for men
Pingback: tadalafil 10mg vs 20mg
Pingback: lotto vip
Pingback: priligy australia
Pingback: commercial real estate
Pingback: cialis no perscription overnight delivery
Pingback: MILF Porn
Pingback: hosting deals
Pingback: Best Realistic Masturbator
Pingback: best penis pump
Pingback: male masturbator
Pingback: cvs aurogra
Pingback: fun88
Pingback: exotic weed canada
Pingback: medication drugs
Pingback: sensuelle massager
Pingback: buy ivermectin canada
Pingback: rechargeable thrusting rabbit toy
Pingback: ivermectil side effects blood pressure
Pingback: viagra bottle
Pingback: halkali escort
Pingback: International Hospital Management
Pingback: pocket masturbator
Pingback: canadian pharmacy cialis 5mg
Pingback: https://regcialist.com/
Pingback: magic wand vibrator
Pingback: trending News
Pingback: where can i buy zithromax uk
Pingback: no prescription required pharmacy
Pingback: zithromax order online uk
Pingback: what is the difference between viagra and cialis
Pingback: zithromax 250 mg australia
Pingback: doxycycline generic cost
Pingback: real life experiences viagra
Pingback: humana pharmacy online
Pingback: cialis bodybuilding
Pingback: penis enlarger
Pingback: viagra not working
Pingback: male pocket stroker
Pingback: amoxicillin pill size
Pingback: cialis 10 mg
Pingback: cialis tablets
Pingback: hydroxychloroquine 200 mg cost
Pingback: generic cialis canadian
Pingback: cialis 20mg low price
Pingback: buying viagra online
Pingback: viagra from india
Pingback: hydroxychloroquine from mexico
Pingback: augmentin price philippines
Pingback: over the counter ed medication
Pingback: how to cure ed
Pingback: generic ed pills
Pingback: hydroxychloroquine sulfate for sale
Pingback: hydroxychloroquine liquid oral
Pingback: ivermectin 1 cream 45gm
Pingback: stromectol uk buy
Pingback: hydroxychloroquine 900 mg
Pingback: ivermectin lice oral
Pingback: reasons for ed
Pingback: best ed drug
Pingback: cytotmeds.com
Pingback: free keto diet for beginners
Pingback: high protein diet vs keto
Pingback: https://ketorecipesnew.com
Pingback: plentyoffish dating
Pingback: Dating site
Pingback: introvert dating
Pingback: stromectol drug
Pingback: acyclovir for covid 19
Pingback: https://datingonlinecome.com
Pingback: free online dating sim
Pingback: buying viagra online
Pingback: fish antibiotics
Pingback: erectile dysfunction medication
Pingback: how long does azithromycin take
Pingback: best pill for ed
Pingback: does female viagra pill work
Pingback: valtrex otc
Pingback: cephalexin dosage chart
Pingback: prescription drugs without doctor approval
Pingback: can i buy cialis in toronto
Pingback: buy cialis cheap canada
Pingback: vidalista coupons
Pingback: Google
Pingback: cialis without presciption in usa
Pingback: ciprofloxacin 500mg antibiotics for sale
Pingback: northwest pharmaceuticals canada
Pingback: free cialis samples online
Pingback: cheap canada drugs
Pingback: vidalista 40 mg india
Pingback: insurance cover cialis
Pingback: how to buy cialis online from canada
Pingback: meijer pharmacy store hours
Pingback: adult dating women net
Pingback: free swinger dating sites
Pingback: bph medications cialis
Pingback: cialis black online
Pingback: zestoretic 10 12.5
Pingback: cialis without a script
Pingback: free dating sites without payment in india
Pingback: lovoo app profilbild ändern
Pingback: buy with paypal
Pingback: prescription drug zestril
Pingback: good tinder bio lines
Pingback: viagra sildenafil
Pingback: cash in advance beaumont
Pingback: conversation starter tinder
Pingback: viagra gold coast
Pingback: viagra kopen zonder recept
Pingback: buy retin a uk
Pingback: buy in miami
Pingback: cialis brand online
Pingback: buy cialis rush
Pingback: generic cialis usa
Pingback: is generic cialis from india safe
Pingback: hydroxychloroquine 200 mg
Pingback: can i buy cialis online
Pingback: prednisone 10 mg tablet directions
Pingback: prolonged effects of cialis
Pingback: sildenafil 100mg review
Pingback: save on pharmacy
Pingback: ED Trial Pack
Pingback: us pharmacy
Pingback: Floxin
Pingback: average cost of lasix
Pingback: the best ed pill
Pingback: levitra advice
Pingback: canadian pharmacy online viagra
Pingback: who manufacturers hydroxychloroquine
Pingback: propecia buy online
Pingback: ivermectin tablets for humans for sale
Pingback: green sildenafil 9800mg
Pingback: cialis generic in usa
Pingback: buy cialis fast shipping
Pingback: metformin 590 mg
Pingback: how much is cialis daily use
Pingback: mantra 10 tadalafil tablets
Pingback: cialis online without prescription
Pingback: overseas pharmacy forum
Pingback: discount pharmacies
Pingback: plaquenil icd 10
Pingback: oxytetracycline dosage for horses
Pingback: tramadol and paxil
Pingback: alternative for metformin
Pingback: neurontin generic
Pingback: viagra generic discount
Pingback: cost tadalafil generic
Pingback: generic cialis bestelle
Pingback: buy cialis with no persciption
Pingback: azithromycin 600 mg dosage
Pingback: united states origin
Pingback: help with college paper writing
Pingback: how to be a good essay writer
Pingback: hydroxychloroquine veterans study
Pingback: rogaine without propecia
Pingback: best dissertation
Pingback: can you buy cialis over the counter australia
Pingback: college entrance essay writing service
Pingback: cheap daily cialis online
Pingback: pfizer generic sildenafil
Pingback: what should i write my essay on
Pingback: how much is vidalista daily
Pingback: dapoxetine with doctor prescription
Pingback: thesis writing online
Pingback: what is dissertation
Pingback: medical school essay writing service
Pingback: i need help writing a thesis
Pingback: helping others essay
Pingback: synthroid pictures
Pingback: diflucan 200 mg
Pingback: traelo priligy
Pingback: ovulation clomid
Pingback: best online pharmacy cialis
Pingback: prednisolone toddler
Pingback: doxycycline without prescription
Pingback: buy clotrimazole
Pingback: metoprolol without prescription
Pingback: albuterol generic
Pingback: ivermectin for sale
Pingback: azithromycin 500 price
Pingback: furosemide 10 mg tablet
Pingback: amoxicillin 500g capsules
Pingback: lilly cialis savings card
Pingback: buy discount cialis best online
Pingback: cialis without prescriptions canada
Pingback: where to buy levothyroxine mcg
Pingback: levofloxacin 500mg without a doctor prescription
Pingback: cailisha petty
Pingback: when is ventolin going generic
Pingback: hydroxychloroquine vietnam vets
Pingback: Google
Pingback: terbinafine 250mg uk
Pingback: hydroxychloroquine malaria prophylaxis
Pingback: cialis without prescriptions canada
Pingback: lamotrigine 100mg cost
Pingback: hydroxychloroquine pills
Pingback: buy hydroxychloroquine from canada
Pingback: hydroxychloroquine coronavirus dosage
Pingback: hydroxychloroquine treatment update
Pingback: generic cialis canada
Pingback: recreational viagra use
Pingback: essay on business ethics
Pingback: personal essay help
Pingback: cialis without prescriptions canada
Pingback: what to write about for my college essay
Pingback: research writing
Pingback: best essay writing service in usa
Pingback: viagra professional
Pingback: buy cialis online at lowest price
Pingback: viagra generico comprar
Pingback: cialis 20mg usa
Pingback: cheapest azathioprine 50mg
Pingback: finasteride drug interaction with sildenafil
Pingback: viagra without a doctor’s prescription
Pingback: buy cialis online overnight
Pingback: viagra online
Pingback: cialis going generic
Pingback: bactrim spectrum of activity
Pingback: ed meds online without doctor
Pingback: tadalafil without doctor prescription
Pingback: cialis without prescriptions canada
Pingback: efectos secundarios de cialis
Pingback: viagra professional 100 mg reviews
Pingback: loperamide tablet
Pingback: cialis and ssri side-effects
Pingback: safe doses of sildenafil citrate
Pingback: does chloroquine kill coronavirus
Pingback: isosorbide online
Pingback: ivermectin generic
Pingback: viagra tablets in hyderabad
Pingback: azithromycin online without prescription
Pingback: glipizide 10 mg nz
Pingback: what is azithromycin used for 250mg
Pingback: how much liquid ivermectin 1% for dogs
Pingback: cialis generic india
Pingback: hoe snel werkt een viagra pil
Pingback: wat kost sildenafil 50 mg
Pingback: nitrofurantoin canada
Pingback: how does cialis affect women
Pingback: vidalista cost in india
Pingback: how to get viagra
Pingback: alendronate otc
Pingback: where can i buy cialis without a prescription
Pingback: abhrglas
Pingback: hydroxychloroquine patient reviews
Pingback: where to buy etodolac
Pingback: real cialis online
Pingback: grapefruit juice viagra
Pingback: buy cialis online europe
Pingback: estradiol united kingdom
Pingback: cwmbgctc
Pingback: hydrochlorothiazide and cialis interaction
Pingback: buy cialis in miami
Pingback: can you buy generic cialis canada
Pingback: erythromycin 250mg tablets
Pingback: 141genericExare
Pingback: cost of permethrin
Pingback: how much does cialis cost with insurance
Pingback: order amitriptyline 25 mg
Pingback: venlafaxine 75 mg price
Pingback: generic viagra kart reviews
Pingback: bisacodyl 5 mg cost
Pingback: doxycycline pills
Pingback: buy cialis 20mg without prescription
Pingback: oxybutynin 5 mg price
Pingback: buy cialis without perscription
Pingback: phenytoin united kingdom
Pingback: where to buy fluconazole 150 mg
Pingback: buy cialis online from canada
Pingback: acetazolamide tablets
Pingback: tolterodine nz
Pingback: 365 pills mobi catalog viagra
Pingback: divalproex 125mg medication
Pingback: desmopressin mcg canada
Pingback: buy cialis tadalafil uk
Pingback: warfarin 1 mg tablets
Pingback: carvedilolmg medication
Pingback: cialis for sale in toront ontario
Pingback: buy cialis drug
Pingback: prochlorperazine 5mg no prescription
Pingback: buy viagra online with out prosription in usa
Pingback: clozapine for sale
Pingback: cialis in europe
Pingback: clindamycin 150mg medication
Pingback: cialis with dapoxetine
Pingback: order loratadine
Pingback: buy ciprofloxacin
Pingback: cialis generic shopping
Pingback: original cialis low price
Pingback: cephalexin price
Pingback: cheap cialis from australia
Pingback: cheapest citalopram 20mg
Pingback: cheap cefuroxime 500mg
Pingback: clonidine 0.1 mg united states
Pingback: buspirone 5 mg without a doctor prescription
Pingback: olmesartan 20 mg uk
Pingback: dutasteride online pharmacy
Pingback: irbesartan coupon
Pingback: anastrozole 1mg without a doctor prescription
Pingback: donepezil tablet
Pingback: buy viagra
Pingback: atomoxetine pharmacy
Pingback: leflunomide for sale
Pingback: cost of meclizine 25mg
Pingback: stacking cialis and viagra
Pingback: glimepiride 1mg australia
Pingback: fexofenadine 120mg pharmacy
Pingback: spironolactone pills
Pingback: cefixime active ingredient in cefixime
Pingback: pioglitazone 15 mg pills
Pingback: where can i buy aripiprazole 15mg
Pingback: cheap escitalopram
Pingback: furosemide 40 mg nz
Pingback: tadalafil 80 mg cheap
Pingback: sildenafil cheap
Pingback: zyvox 600mg tablet
Pingback: rhine inc india viagra
Pingback: where can i buy zyprexa
Pingback: zyloprim 300 mg cost
Pingback: viagra equivalent for women
Pingback: zovirax 200mg uk
Pingback: vidalista reviews patients
Pingback: how to buy zocor
Pingback: can you give ivermectin orally
Pingback: homemade viagra formula
Pingback: he has a good point
Pingback: zestril for sale
Pingback: buy mexican cialis online reviews
Pingback: where to buy zanaflex
Pingback: order wellbutrin
Pingback: voltaren 100 mg prices
Pingback: hydroxychloroquine dose for coronavirus
Pingback: cialis side effects reviews
Pingback: cheap verapamil 40mg
Pingback: where to buy valtrex
Pingback: buy tricor
Pingback: toprol 25 mg over the counter
Pingback: mayo clinic viagra information
Pingback: thorazine without prescription
Pingback: tenormin purchase
Pingback: buy spiriva
Pingback: skelaxin over the counter
Pingback: how to buy singulair
Pingback: cheap seroquel
Pingback: rogaine uk
Pingback: robaxin 500mg united kingdom
Pingback: risperdal online
Pingback: revatio uk
Pingback: cheap retin-a cream
Pingback: remeron 30mg without a doctor prescription
Pingback: michigan governor hydroxychloroquine
Pingback: reglan 10mg online
Pingback: pyridium pharmacy
Pingback: pulmicort united kingdom
Pingback: mens viagra
Pingback: order provigil
Pingback: protonix nz
Pingback: proscar cheap
Pingback: procardia 30mg medication
Pingback: how to buy proair inhaler
Pingback: prilosec cost
Pingback: how to purchase prevacid
Pingback: can dogs take prednisone
Pingback: prednisolone tablet
Pingback: plaquenil cheap
Pingback: phenergan for sale
Pingback: buy periactin 4mg
Pingback: viagra under the tongue
Pingback: nortriptyline 25 mg tablet
Pingback: cialis online pharmacy
Pingback: motrin 600mg generic
Pingback: canadian pharmacy generic viagra
Pingback: mobic australia
Pingback: ed prescription online reviews
Pingback: best canadian online pharmacy
Pingback: micardis 40 mg tablets
Pingback: canada pharmacies online prescriptions
Pingback: pharmacy price compare
Pingback: mestinon 60mg price
Pingback: viagra pay with paypal
Pingback: meclizine 25mg united states
Pingback: macrobid 50 mg over the counter
Pingback: luvox over the counter
Pingback: lopressor 100mg generic
Pingback: lopid price
Pingback: levaquin 750mg purchase
Pingback: lamisil 250 mg pills
Pingback: generic priligy no prescription canada
Pingback: indocin 75mg tablet
Pingback: imuran 50mg uk
Pingback: can women take viagra
Pingback: trump stock in hydroxychloroquine
Pingback: how long does it take viagra to work
Pingback: does viagra lower blood pressure
Pingback: look what i found
Pingback: generic viagra online for sale
Pingback: doxycycline hyclate side effects 100mg
Pingback: cheap imodium
Pingback: withdrawal from hydroxychloroquine
Pingback: generic cialis tadalafil australia
Pingback: canadian cialis
Pingback: cialis
Pingback: cialis generic name
Pingback: imitrex 25mg online
Pingback: buy generic cialis
Pingback: cialis order
Pingback: imdur 30 mg united kingdom
Pingback: hyzaar 12,5 mg usa
Pingback: how much does viagra cost cvs
Pingback: geodon uk
Pingback: proair hfa albuterol rescue inhaler
Pingback: cialis order online
Pingback: cost of fda approved generic 5mg tadalafil
Pingback: erectile dysfunction pills cheap
Pingback: garcinia cambogia 100caps generic
Pingback: where to buy flonase nasal spray 50 mcg
Pingback: flomax prices
Pingback: where can i buy etodolac 200mg
Pingback: erythromycin 500 mg online
Pingback: elavil 50mg united states
Pingback: dramamine over the counter
Pingback: cialis professional wikipedia
Pingback: where can i buy doxycycline
Pingback: cost of aurogra at costco
Pingback: online doctor no insurance
Pingback: apple flavored ivermectin
Pingback: diltiazem online pharmacy
Pingback: cheap differin
Pingback: Viagra or cialis
Pingback: diamox 250mg uk
Pingback: vidalista pills for men ebay
Pingback: depakote price
Pingback: ddavp 10mcg without prescription
Pingback: best thesis editing services
Pingback: dapsone caps australia
Pingback: thesis writing services
Pingback: write my paper apa style
Pingback: research paper writing help
Pingback: tamoxifen and sexual side effects
Pingback: top custom essay services
Pingback: cymbalta 20mg online
Pingback: help 123 essay
Pingback: demystifying dissertation writing
Pingback: cheapest custom essays
Pingback: crestor 5 mg usa
Pingback: viagra medustrusted
Pingback: cozaar purchase
Pingback: sildenafil for women directions
Pingback: order coumadin
Pingback: generic cialis
Pingback: how to buy compazine 5mg
Pingback: usa cialis online
Pingback: the help by kathryn stockett essay
Pingback: cost of coreg
Pingback: Approved viagra pharmacy
Pingback: viagra 50mg tablets
Pingback: combivent 50/20mcg tablets
Pingback: buy cialis in australia
Pingback: symbicort inhaler 160/4,5mcg tablet
Pingback: cheap colchicine 0,5 mg
Pingback: buy clozaril
Pingback: Viagra approved
Pingback: clonidine tablets
Pingback: order cialis canada
Pingback: sildenafil 100mg online
Pingback: cleocin 150mg online
Pingback: write my essays
Pingback: urgent essay writing service
Pingback: order hydroxychloroquine from mexico
Pingback: homeworks of america
Pingback: online essay writers
Pingback: sildenafil 50 mg tablet buy online
Pingback: essay write
Pingback: cheap essay writing service us
Pingback: ivermectin zinc ionophore
Pingback: how to write a good argument essay
Pingback: can you buy sildenafil over the counter in uk
Pingback: australian essay writing service
Pingback: buy essay papers
Pingback: generic viagra does it work
Pingback: online homework planner
Pingback: 20 mg vidalista best price
Pingback: cbd oil for anxiety reviews
Pingback: viagra europe over the counter
Pingback: cbd oil full definition
Pingback: cbd oil for cancer
Pingback: buy levitra usa
Pingback: chewable viagra soft tabs
Pingback: hempworks cbd oil
Pingback: viagra for sale mexico
Pingback: viagra no prescription paypal
Pingback: best cbd oil for pain reviews
Pingback: viagra over the counter in us
Pingback: cbd oil near me for sale
Pingback: generic cialis buy
Pingback: ananda cbd oil
Pingback: cbd oil for seizures
Pingback: online personal loans
Pingback: payday loans in shreveport
Pingback: bad credit loan
Pingback: quick loans dallas tx
Pingback: real viagra for sale online
Pingback: 3 month installment loans
Pingback: payday loans omaha ne
Pingback: Canadian healthcare viagra
Pingback: payday loans for bad credit
Pingback: personal loans now
Pingback: compare car insurance quotes
Pingback: 5mg cialis
Pingback: buy cialis canada
Pingback: car insurance quotes prices
Pingback: cialis and tinnitus
Pingback: non owner car insurance quotes
Pingback: 5mg cialis
Pingback: california car insurance quotes
Pingback: buy cialis
Pingback: cheapest online car insurance quotes
Pingback: geico car ins
Pingback: cheap car insurance quotes in florida
Pingback: best on line viagra
Pingback: car insurance quotes comparison sites
Pingback: bimatoprost ophthalmic solution 0.03%
Pingback: geico car insurance quotes
Pingback: access car insurance
Pingback: casino games online
Pingback: casino online slots
Pingback: hollywood casino online real money
Pingback: sugarhouse casino online nj
Pingback: casino online
Pingback: best online casino real money
Pingback: online gambling
Pingback: casino online slots
Pingback: play for real online casino games
Pingback: live casino slots online
Pingback: viagra vs cialis
Pingback: cheapest claritin
Pingback: cipro prices
Pingback: cephalexin tablet
Pingback: celexa nz
Pingback: celebrex otc
Pingback: ceftin united kingdom
Pingback: how to purchase ceclor 250mg
Pingback: catapres 100 mcg medication
Pingback: viagra coupons from pfizer
Pingback: casodex medication
Pingback: buy viagra usa
Pingback: cardizem 90mg without prescription
Pingback: cheapest calcium carbonate 500 mg
Pingback: sildenafil 20 mg
Pingback: cialis bayer 20
Pingback: where to buy Premarin 0,625mg
Pingback: viagra.com
Pingback: buy cialis in the uk
Pingback: benicar 20mg united kingdom
Pingback: bactrim 400/80mg generic
Pingback: https://keflex.webbfenix.com/
Pingback: baclofen 10mg pills
Pingback: viagra 100mg price
Pingback: avodart 0,5mg australia
Pingback: avapro 150mg price
Pingback: buy augmentin 750/250mg
Pingback: how to purchase atarax 25 mg
Pingback: daily use cialis
Pingback: ashwagandha 60caps pills
Pingback: tamoxifen 10 mg prices
Pingback: is there a viagra for women
Pingback: aricept 5mg pharmacy
Pingback: https://buszcentrum.com
Pingback: strattera 18 mg for sale
Pingback: arava 10mg canada
Pingback: antivert 25mg pharmacy
Pingback: antabuse 500mg without a prescription
Pingback: ampicillin 500 mg over the counter
Pingback: amoxicillin 500mg united states
Pingback: www.bee-rich.com
Pingback: how to buy amaryl 2mg
Pingback: allopurinol 300mg cost
Pingback: allegra 120 mg without a doctor prescription
Pingback: aldactone 100 mg price
Pingback: cheap actos 15mg
Pingback: abilify 10mg pills
Pingback: viagra generic
Pingback: finasteride 5 mg tablets
Pingback: viagra for sale
Pingback: cheapest lexapro 20mg
Pingback: cleckleyfloors.com
Pingback: propecia 1mg for sale
Pingback: cheap furosemide 40mg
Pingback: buy viagra no prescription
Pingback: lasix 100mg over the counter
Pingback: how to buy levitra 10 mg
Pingback: tadalafil 40 mg usa
Pingback: sildenafil 100 mg without a prescription
Pingback: www.azhydroxychloroquine.com
Pingback: Cialis 60 mg tablets
Pingback: cialis 20mg
Pingback: order Cialis 20mg
Pingback: Cialis 80 mg australia
Pingback: Cialis 60mg canada
Pingback: cheapest cialis
Pingback: otc viagra
Pingback: Cialis 80mg pills
Pingback: viagra generic
Pingback: https://www.wisig.org/
Pingback: Cialis 20mg no prescription
Pingback: viagra cheap
Pingback: Cialis 10 mg for sale
Pingback: Cialis 60 mg generic
Pingback: Cialis 40 mg tablets
Pingback: buy viagra
Pingback: Viagra 200 mg pills
Pingback: cialis coupons
Pingback: Viagra 25mg cost
Pingback: Viagra 200mg over the counter
Pingback: hydroxychloroquine cancer
Pingback: where can i buy Viagra 50 mg
Pingback: Viagra 200 mg usa
Pingback: Viagra 25mg tablets
Pingback: cheapest Viagra 100 mg
Pingback: cheap Viagra 25 mg
Pingback: buy cialis pills
Pingback: does cvs have generic viagra
Pingback: viagra buy australia
Pingback: cialis for sale
Pingback: can i buy viagra from canada
Pingback: buy mexican real viagra
Pingback: buy viagra online canada
Pingback: online pharmacy viagra
Pingback: casino slot
Pingback: slot machine
Pingback: generic cialis canada
Pingback: buy viagra no prescription
Pingback: tadalafil vs sildenafil
Pingback: purchase viagra
Pingback: cialis tadalafil
Pingback: how to buy viagra online
Pingback: purchasing cialis online
Pingback: can i buy viagra online
Pingback: buy viagra online cheap
Pingback: female viagra
Pingback: buy viagra canada
Pingback: viagra viagra
Pingback: generic viagra india
Pingback: online casinos real money
Pingback: jackpot party casino
Pingback: casino online
Pingback: online casinos real money
Pingback: cialis 5 mg
Pingback: cialis to buy
Pingback: cialis 5 mg
Pingback: cialis buy
Pingback: play casino online
Pingback: internet casino bonuses
Pingback: CafeCasino
Pingback: cialis to buy
Pingback: viagra pills
Pingback: best real money casinos
Pingback: play penny slots online
Pingback: loans for bad credit
Pingback: personal loan
Pingback: cash loan
Pingback: cialis generic name
Pingback: real casino online
Pingback: play online casino real money
Pingback: viagra sildenafil
Pingback: casino games
Pingback: empire casino online
Pingback: levitra 20mg
Pingback: vardenafil pills
Pingback: buy levitra online
Pingback: Cialis in usa
Pingback: cialis online
Pingback: cvs pharmacy
Pingback: walmart pharmacy
Pingback: cheap erectile dysfunction pill
Pingback: cheapest ed pills online
Pingback: best erection pills
Pingback: viagra for sale
Pingback: online pharmacy viagra
Pingback: viagra generic
Pingback: cialis walmart
Pingback: cialis canadian pharmacy
Pingback: cialis coupon cvs
Pingback: canadian pharmacy cialis 20mg
Pingback: cialis savings card
Pingback: Usa pharmacy viagra
Pingback: buy amoxil
Pingback: Canadian viagra 50mg
Pingback: cialis generic
Pingback: generic cialis india
Pingback: cialis generic name
Pingback: Price viagra