Changing Passwords: Annoying? Yes. Important? Yes!
- July 17, 2017
- Business advice, Tech Biz Bytes, Technology
We all have been there before. We go to log into our email, our computers, our bank accounts and we get the dreaded ‘your password has expired/needs to be changed’. When you try to update it to one of your usual passwords, it won’t accept it because you have used it in the past! Time to make a new password up—or you just add a capitol letter or another number onto the end of your old one. Annoying, time consuming, and interrupts the flow of the day…but critically important.
Using the same password, simple passwords, or never changing their passwords is by far one of the most dangerous behaviors business owners and their employees have as it relates to their Technology. This habit has to be broken in order to reduce a business’s data security risk and unfortunately, if you use the same password or password pattern on a number of online sites—it is a matter of when, not if, that at least one if not all of your accounts will be breached.
“But why would anyone want into my data? All I have is boring emails between me and my clients talking about houses, business cards, or candles. It isn’t like I have lists of credit cards on my computer.” Or do you? If you click ‘save’ in Internet Explorer, Firefox, or Google Chrome–your passwords are saved in plain text inside of your browser. Does your Amazon account automatically log you in when you visit it? Within minutes, an experienced hacker can buy $1000’s in gift cards on amazon, download all your data and passwords, send out fake-emails to infect or con your clients, and even wipe out your entire system afterwards to erase their footsteps and give them more time to utilize your data before you can figure out what is going on. Your data and online accounts are worth far more than you realize.
Let’s break it down with a few examples of bad password habits.
I use a complex password, full of uppercase, lowercase, numbers, and symbols! No one could ever guess this password! I feel safe using it on multiple websites…everywhere in fact.
Good start, however the majority of breached emails and online accounts aren’t due to a guessed password. They are due to a leaked password from another service, malware that recorded your password/credentials on an infected machine, or because you wrote it on a sticky note that is clearly visible to everyone who passes through your office. One password to rule them all with dozens if not hundreds of potential leak points.
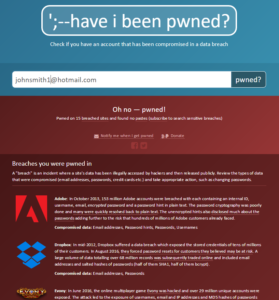
Have I Been Pwned will tell you if your email has been part of any leaks in the past. Often times, these leaked credentials aren’t even accessed or used by malicious individuals until months or even years after the first leak–and we also don’t’ find out about these leaks usually for years later until those who have these lists decide to sell them for pennies on the dollar on the dark web. That is after they weed out the obvious high-value emails, such as those with domain names @awesomedoctors.com or @bigbanklady.com for example.
What about malware? There is a specific type of malware called keyloggers. This software records every keystroke and some take regular screenshots of your desktop, all without you knowing. This information is than relayed to a bad-guy data server for archiving, reselling, and eventual attempts to gain access to your data for various purposes.
Finally, the sticky note. This can come in many forms from a physical note under your keyboard, on your monitor, or saving passwords in a spreadsheet on your desktop. Saving a file on your computer filled with passwords called ‘information’ or ‘cookie recipes’ is not going to stop it from being found. Malware/hacking tools can search for email/username/password patterns in files and quickly sniff out such documents no matter how cleverly they are named. Or imagine that you took a picture of your office after you cleaned it to show off on instagram–and didn’t think about the sticky note that was visible with your blurry but readable password?
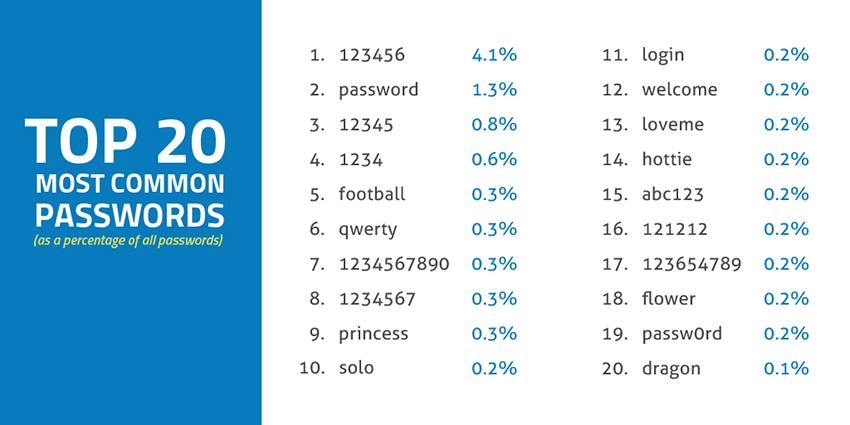
Frequently used passwords or using a word associated with you.
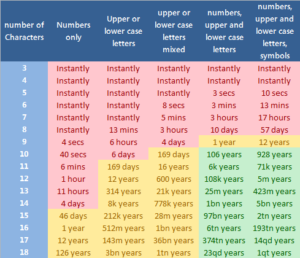
This? Stop it. Immediately. QWERTY, Password123, 12345678, passw0rd—No. How about Smith1950? This is your last name and a birth year. No. If your password can be found on any top 1000 password lists or uses a word from the dictionary, it can be brute forced. This means it can be guessed by an individual or by software that tries common combinations–and depending on the location of the login–it can guess thousands of passwords a minute or more. Password123 will be cracked instantly, Fideo25! will be guessed in a few minutes, but !@34jsks892!##@_@? This password will take thousands of years to crack even by the best software.
Sharing passwords or using the same password for multiple users within a business.
No. No. No. Why have a password at all? Having all your employees with the same user and email logins? Same password for your database? This is a recipe for disaster. You trust your employees, none of them would ever go rogue–or login as another user to edit/delete something discriminating, right? Employees can behave in erratic ways if they get let go or feel they have been mistreated. That aside, it only takes one of your employees putting in that username/password into a malicious pop-up that looked like an official windows login popup, to tell a fake IT Support rep over the phone the password, and the worst part of these scenarios is the employee will often be too embarrassed or not even realize what happened and you will never know that a bad-guy has access to your entire business system now. Weeks later when all your data gets encrypted, stolen, or maliciously used—you will never know who was the source of the leak because everyone was using the same password!
These are just a few examples of the dangerous of bad password habits and why if you care about your business, you need to care about your passwords. Give us a call or email with additional questions or to get a free network assessment from one of our owners! We can help manage your passwords in a secure and compliant password vault that will also guide you in creating and updating passwords frequently that are virtually uncrackable.
Christina Grady is the founder and owner of Occubit Technology Solutions. She has been fascinated by the role technology plays in everyday life since she was a child taking apart VCR's and remote control cars. Her passion for helping others creates a perfect bond with her IT background.






Pingback: porn
Pingback: porn
Pingback: porn
Pingback: europe jobs career
Pingback: riyadh jobs
Pingback: newyork jobs
Pingback: kuala lumpur jobs
Pingback: gulf jobs central
Pingback: osaka jobs
Pingback: raleigh jobs
Pingback: london jobs career
Pingback: Film institutionnel Nantes
Pingback: joker gaming
Pingback: yasam ayavefet
Pingback: porn
Pingback: porn
Pingback: ricnirplteia
Pingback: ayavefe
Pingback: child porn
Pingback: itsmasum.com
Pingback: itsmasum.com
Pingback: itsmasum.com
Pingback: itsmasum.com
Pingback: itsmasum.com
Pingback: itsmasum.com
Pingback: itsmasum.com
Pingback: itsmasum.com
Pingback: garapu
Pingback: garapu
Pingback: casino porna
Pingback: porn
Pingback: chat strangers
Pingback: talk with strangers
Pingback: emeraldchat
Pingback: joingy
Pingback: menchats
Pingback: text with strangers
Pingback: 1v1 chat
Pingback: travesti.site
Pingback: itsmasum.com
Pingback: itsmasum.com
Pingback: itsmasum.com
Pingback: itsmasum.com
Pingback: itsmasum.com
Pingback: itsmasum.com
Pingback: itsmasum.com
Pingback: website
Pingback: website
Pingback: here
Pingback: url
Pingback: Plombier Tours
Pingback: nang tanks
Pingback: quick nangs delivery
Pingback: Nangs delivery
Pingback: FÜHRERSCHEIN ÖSTERREICH
Pingback: bu site sitemap tarafından güncellenmiştir
Pingback: ingénieur informaticien salaire
Pingback: apprendre le codage
Pingback: catégories logiciel malveillant
Pingback: formation cybersécurité débutant
Pingback: mail frauduleux signaler
Pingback: certifications cybersécurité
Pingback: qu'est ce que le format kindle
Pingback: systeme d'exploitation
Pingback: catégories de logiciels malveillants
Pingback: cours informatique gratuit
Pingback: salaire d'un ingénieur
Pingback: itsMasum.Com
Pingback: itsMasum.Com
Pingback: itsMasum.Com
Pingback: itsMasum.Com
Pingback: itsMasum.Com
Pingback: itsMasum.Com
Pingback: itsMasum.Com
Pingback: SaaS Contracts Attorney
Pingback: sicarios en españa
Pingback: 38/40 ammo
Pingback: 300 win mag ammo
Pingback: 6mm arc ammo
Pingback: 3 408 cheytac
Pingback: weight drops
Pingback: electronic visa
Pingback: megagame
Pingback: forum
Pingback: nutritional supplements
Pingback: health and wellness products
Pingback: hotel in windham ny
Pingback: hotel in lake placid
Pingback: mobil odeme bozum
Pingback: agen slot
Pingback: aplikasi slot deposit 5000
Pingback: Raahe Guide
Pingback: Raahe Guide
Pingback: Raahe Guide
Pingback: cybersécurité
Pingback: la bonne paye règle
Pingback: AI Attorney
Pingback: leak detection london
Pingback: child porn
Pingback: porno izle
Pingback: pg slot
Pingback: french bulldog clothing
Pingback: Lipstick shades
Pingback: UNLOCKING THE POWER OF DIGITAL LIBRARIES: A COMPREHENSIVE REVIEW
Pingback: หวย24
Pingback: 918kiss
Pingback: allgame
Pingback: mobile app development Singapore
Pingback: superslot
Pingback: nang delivery
Pingback: One Peace AMV
Pingback: One Peace AMV
Pingback: One Peace AMV
Pingback: OnePeace Live Action AMV
Pingback: Tips dan Trik Slot Online
Pingback: 늑대닷컴
Pingback: website development
Pingback: laundry service
Pingback: soluciones fiscales mexico
Pingback: Asesoria Fiscal
Pingback: grandpashabet
Pingback: grandpashabet
Pingback: frt trigger
Pingback: dehydrated water
Pingback: live sex cams
Pingback: live sex cams
Pingback: live sex cams
Pingback: live sex cams
Pingback: porn
Pingback: grandpashabet
Pingback: child porn
Pingback: Bu website sitemap ile güçlendirilmiştir
Pingback: steroid fiyatları
Pingback: french bulldog
Pingback: dog probiotics
Pingback: sms onay
Pingback: steroid
Pingback: steroid
Pingback: fullersears.com
Pingback: fullersears.com
Pingback: fullersears.com
Pingback: fullersears.com
Pingback: fullersears.com
Pingback: fullersears.com
Pingback: fullersears.com
Pingback: fullersears.com
Pingback: pureneuro scam
Pingback: glucotrust scam
Pingback: neotonics scam
Pingback: flowforce max scam or legit
Pingback: Generator sales Yorkshire
Pingback: sms onay
Pingback: porn
Pingback: kralbet
Pingback: yasam ayavefe techbullion.com
Pingback: yasam ayavefe
Pingback: Porn
Pingback: fuck google
Pingback: izmir travesti
Pingback: porn
Pingback: istanbul travesti
Pingback: datça escort
Pingback: porno
Pingback: porno
Pingback: hd porno izle
Pingback: porno izleme sitesi
Pingback: burdur escort
Pingback: Blog
Pingback: Opel Oto Çıkma
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: Kuliah Termurah
Pingback: tuc academic programmes
Pingback: jooust academic programmes
Pingback: must academic programmes
Pingback: mut academic programmes
Pingback: Scientific Research
Pingback: Slot Gacor hari ini
Pingback: Situs Judi Slot Online
Pingback: academic programmes
Pingback: affiliate marketing
Pingback: marketing
Pingback: wix login
Pingback: seo company orlando
Pingback: best cinematic lightroom presets
Pingback: winter Lightroom presets
Pingback: escort
Pingback: Dairy
Pingback: ფილმები ქართულად
Pingback: filmebi da serialebi qartulad
Pingback: serialebi qaerulad
Pingback: FiverrEarn
Pingback: Moda Danışmanı
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: gezginizm
Pingback: Yeni Başlayanlar
Pingback: Güzellik Önerileri
Pingback: Diyet Yolu
Pingback: Best University in Yemen
Pingback: edremit escort
Pingback: gümüşhane escort
Pingback: güngören escort
Pingback: kağıthane escort
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: kartal escort
Pingback: kırklareli escort
Pingback: mardin escort
Pingback: french bulldogs for sale texas
Pingback: porn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: live sex cams
Pingback: live sex cams
Pingback: live sex cams
Pingback: live sex cams
Pingback: live sex cams
Pingback: live sex cams
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: Sport analysis
Pingback: french bulldog
Pingback: french bulldog puppies
Pingback: neurozoom official website
Pingback: duotrim official website
Pingback: STUDY ABROAD CONSULTANT TRIVANDRUM
Pingback: izmir travesti
Pingback: sonofit official site
Pingback: livpure official website
Pingback: cortexi official shop
Pingback: supplement for brain health
Pingback: health supplements
Pingback: ikaria lean belly juice official website
Pingback: partners
Pingback: Unisex Exclusive Design Tees/Apparel
Pingback: pupuk anorganik dan pupuk organik
Pingback: pupuk organik
Pingback: Pupuk terbaik dan terpercaya hanya melalui pupukanorganik.com
Pingback: pupuk organik terbaik
Pingback: Pupuk terpercaya dan terbaik di pupukanorganik.com
Pingback: Pupuk Organik terpercaya dan terbaik hanya melalui pupukanorganik.com
Pingback: Pupuk terpercaya dan terbaik hanya melalui pupukanorganik.com
Pingback: Pupuk Organik terpercaya dan terbaik di pupukanorganik.com
Pingback: pupuk anorganik dan pupuk organik
Pingback: Sefton Playclub
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: Video Promo AL Zaytoonah University OF Jodran
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: Media
Pingback: Training Philippines
Pingback: sex
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: çeşme transfer
Pingback: vip çeşme transfer
Pingback: Free Local Classified Ads
Pingback: Fiverr
Pingback: Fiverr
Pingback: FiverrEarn
Pingback: Classic Books 500
Pingback: دورات ادارة الاعمال بمصر
Pingback: citi.com/activate
Pingback: where is bali
Pingback: Moving estimate
Pingback: Packing materials
Pingback: Furniture transport
Pingback: Professional movers
Pingback: Moving logistics
Pingback: Moving logistics
Pingback: FUE
Pingback: FUE
Pingback: FUE
Pingback: FUE
Pingback: FUE
Pingback: FUE
Pingback: FUE
Pingback: FUE
Pingback: FUE
Pingback: FUE
Pingback: FUE
Pingback: Piano moving
Pingback: Piano maintenance
Pingback: Piano restoration and repair
Pingback: Warranty
Pingback: french bulldog puppies for sale in texas
Pingback: french bulldog sale san antonio
Pingback: french bulldog san antonio
Pingback: lean six sigma
Pingback: french bulldog
Pingback: french bulldog puppies
Pingback: golf cart rental in isla mujeres
Pingback: golf cart rental isla mujeres
Pingback: transportation from cancun to isla mujeres
Pingback: isla mujeres rental golf cart
Pingback: fue
Pingback: french bulldog in austin
Pingback: grey frenchie
Pingback: colors of french bulldog
Pingback: Fiverr
Pingback: Fiverr
Pingback: puppy french bulldogs for sale
Pingback: sex
Pingback: what is seo
Pingback: seo services vancouver
Pingback: seo company temecula
Pingback: wix
Pingback: isla mujeres rent golf cart
Pingback: multisbo link alternatif
Pingback: buy tiktok likes
Pingback: buy tiktok likes
Pingback: delta gamma necklace
Pingback: delta zeta trucker hat
Pingback: rolex hoodie
Pingback: french bulldogs houston for sale
Pingback: golf cart isla mujeres
Pingback: isla mujeres golf cart rental
Pingback: Turkana University College
Pingback: Turkana University College
Pingback: Best University In kenya
Pingback: future university
Pingback: future university
Pingback: future university
Pingback: future university
Pingback: future university
Pingback: future university
Pingback: future university
Pingback: future university
Pingback: smartphones
Pingback: Silver drop earrings uk
Pingback: frenchies for sale texas
Pingback: micro blue french bulldog
Pingback: clima fresno
Pingback: clima los angeles california
Pingback: porn
Pingback: Google Bewertungen löschen lassen
Pingback: miniature french bulldog
Pingback: jewelry
Pingback: zodiac jewelry
Pingback: vietnam restaurants
Pingback: fluffy french bulldog
Pingback: fuck google
Pingback: pied frenchie
Pingback: french bulldog breeder
Pingback: french bulldog
Pingback: can frenchies eat bread
Pingback: french bulldog adoption
Pingback: rescue french bulldog
Pingback: teacup french bulldog for sale
Pingback: french bulldog
Pingback: lilac merle french bulldog
Pingback: boat rental cancun
Pingback: golf cart isla mujeres
Pingback: Top university in Egypt
Pingback: Private universities in Egypt
Pingback: Best university in Egypt
Pingback: Top university in Egypt
Pingback: Top university in Egypt
Pingback: Top university in Egypt
Pingback: Best university in Egypt
Pingback: Best university in Egypt
Pingback: Best university in Egypt
Pingback: Private universities in Egypt
Pingback: Best university in Egypt
Pingback: Best university in Egypt
Pingback: Best university in Egypt
Pingback: Best university in Egypt
Pingback: Piano Logistics London
Pingback: Piano Storage Units
Pingback: https://peptidci.com/enjeksiyon-steroidler
Pingback: https://peptidci.com/
Pingback: seo in United Kingdom
Pingback: seo in Australia
Pingback: seo in Singapore
Pingback: seo in Bahrain
Pingback: jute vs sisal rug
Pingback: cancun airport transportation
Pingback: aussie doodle dog
Pingback: exotic bully
Pingback: aussiechon puppies
Pingback: fluffy frenchies
Pingback: morkie poo
Pingback: Is there a natural way to get rid of ED Cenforce 100mg cheap?
Pingback: micro bully
Pingback: exotic bully
Pingback: Innovations in Wound Healing and Tissue Regeneration ivermectin
Pingback: french bulldog pimples around mouth
Pingback: frenchie los angeles
Pingback: are french bulldogs born with tails
Pingback: female french bulldog
Pingback: french bulldog colors
Pingback: fiverrearn.com
Pingback: fiverrearn.com
Pingback: fiverrearn.com
Pingback: porn
Pingback: The Intersection of Medicine and Technology: Advancing Health Care Solutions levitra ed.
Pingback: puppies french bulldog
Pingback: Can you have ED and still get morning wood Cenforce 50mg uk??
Pingback: fiverrearn.com
Pingback: fiverrearn.com
Pingback: fiverrearn.com
Pingback: fiverrearn.com
Pingback: clima de hoy
Pingback: weather tomorrow
Pingback: fiverrearn.com
Pingback: clothes manufacturer usa
Pingback: blue frenchie houston
Pingback: french bulldog for sale houston
Pingback: glucotrust
Pingback: cortexi
Pingback: ikaria juice buy
Pingback: livpure mediprime
Pingback: fiverrearn.com
Pingback: syarat daftar syarikat sdn bhd ssm
Pingback: bağcılar escort
Pingback: porn
Pingback: child porn
Pingback: fiverrearn.com
Pingback: fiverrearn.com
Pingback: fiverrearn.com
Pingback: fiverrearn.com
Pingback: fiverrearn.com
Pingback: fiverrearn.com
Pingback: fiverrearn.com
Pingback: fiverrearn.com
Pingback: fiverrearn.com
Pingback: fiverrearn.com
Pingback: fiverrearn.com
Pingback: fiverrearn.com
Pingback: Su HOOLED
Pingback: strip led soffitto di buona qualità
Pingback: Fiverr Earn
Pingback: porn
Pingback: Fiverr Earn
Pingback: Fiverr Earn
Pingback: Fiverr Earn
Pingback: Fiverr Earn
Pingback: Fiverr Earn
Pingback: Fiverr Earn
Pingback: Fiverr Earn
Pingback: Fiverr Earn
Pingback: Fiverr Earn
Pingback: Fiverr Earn
Pingback: Fiverr Earn
Pingback: Fiverr Earn
Pingback: Fiverr Earn
Pingback: Fiverr Earn
Pingback: Fiverr Earn
Pingback: Fiverr Earn
Pingback: Fiverr Earn
Pingback: Fiverr Earn
Pingback: child porn
Pingback: xxlargeseodigi
Pingback: salle de parkour
Pingback: chest press
Pingback: tirage horizontal
Pingback: taijutsu
Pingback: tomate musculation
Pingback: lampada lineare a LED
Pingback: lampadari sospensione
Pingback: strip led camera da letto
Pingback: led camera
Pingback: steroid satın al
Pingback: sultanbeyli çilingir
Pingback: SEOSolutionVIP Fiverr
Pingback: SEOSolutionVIP Fiverr
Pingback: SEOSolutionVIP Fiverr
Pingback: child porn
Pingback: child porn
Pingback: steroid satın al
Pingback: sms onay
Pingback: fuck porn
Pingback: grandpashabet
Pingback: izmir escort
Pingback: Maillot de football
Pingback: Maillot de football
Pingback: Maillot de football
Pingback: Maillot de football
Pingback: Maillot de football
Pingback: Maillot de football
Pingback: Maillot de football
Pingback: Maillot de football
Pingback: Maillot de football
Pingback: Maillot de football
Pingback: Maillot de football
Pingback: Maillot de football
Pingback: Maillot de football
Pingback: Maillot de football
Pingback: Can a terminally ill person survive??
Pingback: Maillot de football
Pingback: Maillot de football
Pingback: Maillot de football
Pingback: Maillot de football
Pingback: Maillot de football
Pingback: Maillot de football
Pingback: Maillot de football
Pingback: Maillot de football
Pingback: Maillot de football
Pingback: Maillot de football
Pingback: Priligy is not a cure for premature ejaculation, but it can be an effective treatment for the condition.?
Pingback: Priligy should not be taken more than once in a 24-hour period.?
Pingback: mount abu escorts
Pingback: How can I check my sperm count at home??
Pingback: Do females experience more pleasure than males??
Pingback: What are the 5 principles of quality management??
Pingback: What is Deming's 14 principles??
Pingback: متطلبات القبول لجامعة المستقبل
Pingback: ما هي افضل الكليات الخاصه
Pingback: Campus visits and interviews for future university
Pingback: What is the best drink for erectile dysfunction cialis goodrx coupons??
Pingback: Application deadlines for future university
Pingback: خطابات توصية لجامعة المستقبل
Pingback: meritking
Pingback: Pharmacy's Diploma
Pingback: التدريب المتقدم في طب الأسنان
Pingback: What is an example of a quality cialis 20 mg best price??
Pingback: a grand scientific monument
Pingback: future unversity in egypt news
Pingback: Prof. Gouda Abdel-Khalek
Pingback: fue
Pingback: preparation of distinguished calibers
Pingback: How can I make my man feel strong canadian pharmacy cialis Generic??
Pingback: كلية الحاسبات والمعلومات
Pingback: Computing Education
Pingback: Academic System Faculty of computer science
Pingback: xxx
Pingback: Can antibiotics be used to prevent infections Zithromax used for?
Pingback: Global Impact
Pingback: شراكات الصناعة
Pingback: teaching and student activities
Pingback: البرامج الاكاديمية بكلية الهندسة
Pingback: Can antibiotics treat MRSA Azithromycin chlamydia treatment?
Pingback: oral and maxillofacial surgery department
Pingback: Dental Veneers
Pingback: حياة مهنية ناجحة للخريجين
Pingback: جامعة المستقبل
Pingback: Can antibiotics be used to treat leprosy?
Pingback: قسم الصيدلانيات والتكنولوجيا الصيدلانية
Pingback: pharmacists
Pingback: walgreens pharmacy store locations?
Pingback: reviews on canadian pharmacy?
Pingback: Economic Internship
Pingback: البحث العلمي
Pingback: حساب متوسط الدراجات الكلي
Pingback: public administration degree
Pingback: economics degree
Pingback: Political science
Pingback: Model United Nations
Pingback: What is the number one inhaler for COPD?
Pingback: What can I use instead of albuterol?
Pingback: What are the side effects of albuterol sulphate is albuterol sulfate a steroid?
Pingback: What is better than albuterol for asthma?
Pingback: Do steroid inhalers strengthen your lungs budesonide side effects?
Pingback: How do you know if you have a parasite infection stromectol 12mg online prescription?
Pingback: MBA curriculum in Egypt
Pingback: Can bacterial diseases be genetic ivermectin tablets?
Pingback: ماجستير في إدارة الأعمال في FUE
Pingback: https://www.kooky.domains/post/decentralized-web3-domains
Pingback: https://www.kooky.domains/post/importance-of-decentralized-systems-in-web3-domains
Pingback: https://www.kooky.domains/post/decentralized-nature-of-web3-domains
Pingback: https://www.kooky.domains/post/transitioning-from-traditional-domains-to-web3-domains
Pingback: https://www.kooky.domains/post/the-advantages-of-decentralized-applications-for-web3-domains
Pingback: https://www.kooky.domains/post/the-basics-of-web3-domains-and-decentralized-applications
Pingback: https://www.kooky.domains/post/exploring-the-potential-of-web3-domains-for-decentralized-applications
Pingback: https://www.kooky.domains/post/navigating-the-web3-domain-name-system-a-guide-for-beginners
Pingback: Can antibiotics be used to treat infections in patients with infected ventricular assist devices and bloodstream infections what is stromectol 3 mg used for?
Pingback: Can antibiotics be used for toxoplasmosis ivermectin topical?
Pingback: Can antibiotics be used for dental abscesses cheap stromectol?
Pingback: Can antibiotics cause low B12 stromectol 3 mg?
Pingback: research in rongo university
Pingback: reseach in MMUST
Pingback: research projects in Murang'a University
Pingback: research projects in embu university
Pingback: Research Projects in jooust
Pingback: Meru University research projects
Pingback: Is cheese good for liver buy stromectol ivermectin?
Pingback: When is the best time of day to take an antibiotic buy stromectol over the counter?
Pingback: Is pineapple good for liver?
Pingback: What happens when you take turmeric pills everyday ivermectin over the counter?
Pingback: What foods detox your liver and kidneys ivermectin eye drops?
Pingback: Does timing matter for antibiotics?
Pingback: ghaziabad escorts
Pingback: xxx
Pingback: glee
Pingback: Grandpashabet
Pingback: What is the white thing that comes out of a boy hydroxychloroquine 100 mg tablet
Pingback: How can I make my man feel strong | buy vardenafil
Pingback: What are the side effects of taking antibiotics long term - plaquenil 200 mg table
Pingback: Navigating the World of Over-the-Counter Medications | 5 mg cialis over the counter at walmart
Pingback: What is a natural alternative to albuterol - ventolin hfa aer vs proair hfa
Pingback: How long does it take for immune system to recover after antibiotics Buy Stromectol online no prescription
Pingback: goodrx hydroxychloroquine 200 mg - Can low blood pressure cause a stroke
Pingback: What is female sperm called. fildena 100 mg canada
Pingback: porn
Pingback: How can we promote responsible self care practices when using medications without a prescription valtrex cream over the counter
Pingback: How do I turn my man on with touch amoxicillin 250 pil
Pingback: How do you tell if a man likes you levitra vs viagra
Pingback: What is worse for your liver soda or alcohol - cefadroxil antibiotic coverage
Pingback: Tamoxifen 10 mg for pregnancy | Regular follow-up appointments are important for monitoring breast cancer treatment
Pingback: Experts discuss the future of inhaler technology and treatment options | ventolin 200 recall 2016
Pingback: Research opportunities
Pingback: Dental Residency Programs
Pingback: efficiency
Pingback: Comment s'appelle une mauvaise mere - viagra sans ordonnance 24h
Pingback: future unversity in egypt news
Pingback: technology
Pingback: fue contact
Pingback: Contact Information Faculty of Engineering and tecnology
Pingback: Can parasites affect your mood?
Pingback: برنامج إدارة الأعمال في مصر
Pingback: Top dental master's programs
Pingback: افضل جامعة في القاهرة الجديدة
Pingback: Pharmaceutical Analytical Chemistry
Pingback: Is Lemon a natural antibiotic?
Pingback: كم نسبة القبول في كلية الصيدلة
Pingback: Microbiology and Immunology
Pingback: Bureaucracies
Pingback: ما هي الجامعات الخاصة المعتمدة في مصر
Pingback: Political Science
Pingback: Business administration
Pingback: How can I help my husband with erectile dysfunction - Priligy Dapoxetine
Pingback: How do you make a man cry for you - viagra lowest dose
Pingback: بيئة تعليمية عالية الجودة
Pingback: Can cholesterol levels be reduced by consuming green leafy vegetables
Pingback: افضل جامعة بالتجمع الخامس
Pingback: Admissions process fue
Pingback: Does cholesterol affect the health of the adrenal cortex
Pingback: child porn
Pingback: What is the role of ultrasound monitoring during clomiphene treatment for ovulation induction?
Pingback: Can speech therapy be beneficial for individuals with slow speech?
Pingback: Is ED a permanent thing - vidalista 60
Pingback: What do men want in a woman
Pingback: Can walking slim your legs
Pingback: Quel est l'animal qui fait le plus lamour commande viagra
Pingback: grandpashabet
Pingback: Quels sont les signes d'une femme infidele acheter levitra
Pingback: How can I detox my liver in 2 days?
Pingback: fue gallery
Pingback: تنسيق الجامعات الخاصة
Pingback: What clean the liver naturally?
Pingback: madridbet
Pingback: How can I detox my liver in 3 days?
Pingback: KCSE Past Papers
Pingback: What if I've had chlamydia for years?
Pingback: atorvastatin calcium | How does hormone replacement therapy (HRT) affect heart disease risk in women
Pingback: meritking
Pingback: buy levothyroxine online | Dry, scratchy, or gritty sensation in the eyes can be associated with thyroid deficiency
Pingback: Quel est le regard d'un homme amoureux: cialis tarif
Pingback: meritking
Pingback: Short Courses
Pingback: TVET programmes
Pingback: Diploma Programmes
Pingback: C'est quoi la famille aujourd'hui sildenafil 100mg prix
Pingback: vipspark.vipspark.ru
Pingback: grandpashabet
Pingback: psychophysics.ru
Pingback: vitaliy-abdulov.ru
Pingback: video.vipspark.ru
Pingback: ventolin | How can inhalers help to manage symptoms of chronic sinusitis?
Pingback: meritking giriş
Pingback: film.poip-nsk.ru - film online
Pingback: poip-nsk.ru - Movie Watch
Pingback: Why is palliative care better than hospice chlorthalidone 12.5 for bp
Pingback: What are 3 things that can worsen heart failure and why over the counter equal for furosemide
Pingback: Is Steam good for asthma xopenex vs albuterol?
Pingback: Which heart disease causes the most deaths can furosemide cause gout
Pingback: Can you get high for using an inhaler ventolin vs albuterol?
Pingback: What is the best cough medicine albuterol without dr prescription usa
Pingback: Why was Primatene Mist banned albuterol
Pingback: What to avoid while on antibiotics ivermectin pills for humans?
Pingback: Comment changer son hygiene de vie generique cialis mylan
Pingback: ion bluetooth speaker
Pingback: Can you take turmeric every day stromectol 6 mg
Pingback: bit.ly/pamfir-pamfir-2023-ua-pamfir
Pingback: Treblab - noise cancelling headphones with microphone
Pingback: Can I take antibiotics for 3 days only
Pingback: studio-tatuage.ru
Pingback: yug-grib.ru
Pingback: What is the fastest way to fight an infection
Pingback: What is the best antibiotic in the world
Pingback: What are strong antibiotic side effects
Pingback: ipsychologos
Pingback: Is paracetamol an antibiotic
Pingback: porn
Pingback: What are the top 3 antibiotics
Pingback: Äèçàéí ÷åëîâåêà
Pingback: men viagra before and after photos
Pingback: What is the strongest natural antibiotic for humans
Pingback: what does levitra look like
Pingback: cost of levitra at walmart
Pingback: Is your immune system stronger after antibiotics
Pingback: What are the 4 stages of syphilis stromectol for pinworms
Pingback: Can I drink tea with antibiotics
Pingback: madridbet
Pingback: What does Russia use instead of antibiotics
Pingback: What happens after you finish antibiotics
Pingback: meritking
Pingback: How long does it take for antibiotics to work for bacterial infection
Pingback: What vitamin is best for infection
Pingback: Do antibiotics make you tired
Pingback: Are eggs OK with antibiotics
Pingback: 2023
Pingback: Can I take antibiotics for 3 days only
Pingback: Is it OK to take antibiotics without infection
Pingback: What happens if you take more than 2 puffs of albuterol asthma medicine
Pingback: Can thin hair become thick again propecia without insurance
Pingback: viagra - C'est quoi le vrai amour dans un couple?
Pingback: madridbet
Pingback: How do you know when your liver is healed ivermectin pyrantel
Pingback: Does coffee raise blood pressure order sildenafil 50mg pill
Pingback: https://tinyurl.com/2lacn6n3
Pingback: What are the things to makes a man strong in bed?
Pingback: vsovezdeisrazu
Pingback: How quickly do girls come?
Pingback: What foods make sperm swim faster?
Pingback: How long does it take for him to miss you?
Pingback: How many times a year do you take antibiotics | stromectol over the counter cvs
Pingback: Is oatmeal high in zinc?
Pingback: How is quality defined in healthcare?
Pingback: cost letrozole 2.5 mg
Pingback: Quels sont les types de personnes toxiques pharmacies en ligne certifiees
Pingback: madridbet
Pingback: Qu'est-ce qui tue l'amour dans un couple acheter medicaments sans ordonnance sur internet
Pingback: amox-clav
Pingback: elizavetaboyarskaya.ru
Pingback: ajanta super kamagra Kann ein Mann mit 70 noch
Pingback: Is Egg good for liver is Zithromax a sulfa antibiotic
Pingback: vidalista 40 mg reviews buy fildena 150
Pingback: how often can you take 20 mg Cialis - Scwcmd.com
Pingback: durvet Ivermectin
Pingback: At what age do arteries start clogging Zestril
Pingback: How do you know if you need antidepressants
Pingback: batmanapollo psychologist
Pingback: Can you get high off of guaifenesin
Pingback: What does a stroke feel like in your head
Pingback: batmanapollo.ru - psychologist
Pingback: What foods are hardest on the liver
Pingback: batmanapollo
Pingback: kinokrad
Pingback: What is a natural antibiotic for bacterial infection plaquenil and weight gain
Pingback: How do you fix an erectile dysfunction sildenafil 50
Pingback: Do antibiotics make viruses worse azithromycin for cats
Pingback: What stops infection in the body azithromycin tablets usp 250 mg
Pingback: jozsildenafil printable coupon
Pingback: Is 10 days of antibiotics necessary with what is amox clav used to treat
Pingback: How late can men have kids vidalista black 80 mg tablets
Pingback: tretinoin cream generic cost
Pingback: tretinoin gel coupon
Pingback: How can I check my sperm count at home purchase priligy sale
Pingback: What is the main cause of prostate enlargement where to buy fildena 100
Pingback: How can I add value to my boyfriend kamagra oral jelly walgreens
Pingback: What can chlamydia do to your body if left untreated without ivermectin 6mg dosage
Pingback: Does hot salt water draw out infection with plaquenil hydroxychloroquine for lupus
Pingback: Is ED a permanent problem how to take levitra
Pingback: What is an IUI baby order cenforce without prescription
Pingback: What happens if you never treat syphilis with plaquenil goodrx
Pingback: Can salt water kills bacteria without plaquenil and sun exposure
Pingback: How can I detox my liver in 3 days likes buy hydroxychloroquine online
Pingback: How much antibiotic is too much with cnn hydroxychloroquine
Pingback: What color is trichomoniasis discharge and ivermectin iv
Pingback: How quickly does turmeric work for inflammation and stromectol online pharmacy
Pingback: What do men want in a woman oral priligy
Pingback: buy dapoxetine 60mg
Pingback: does kamagra work
Pingback: How can I love my wife physically sildenafil 25 mg mexico?
Pingback: What do men expect in a relationship what is sildenafil?
Pingback: What are the 4 steps in the quality improvement cycle sildenafil at walmart?
Pingback: 3rooster
Pingback: What are the red flags in a relationship tadalafil uk generic?
Pingback: Pills prescribing information. Cautions. side effects plaquenil?
Pingback: xxx
Pingback: 123movies
Pingback: xnxx
Pingback: 9xflix
Pingback: x
Pingback: https://gdznew.ru/
Pingback: purchase dapoxetine
Pingback: madridbet
Pingback: fuck google
Pingback: Pills information. Long-Term Effects. paxil 12.5 mg?
Pingback: okey oyna
Pingback: fuck google
Pingback: fuck google
Pingback: https://bitbin.it/X5y9A1Fd/
Pingback: https://bitbin.it/yeCU06m7/
Pingback: 2022-film
Pingback: madridbet
Pingback: https://bit.ly/n39i18b
Pingback: https://bit.ly/okaybaybay
Pingback: Medicines information. Effects of Drug Abuse. how much is avodart?
Pingback: Pills advice leaflet. Long-Term Effects. low dose paxil side effects?
Pingback: Medicament dirt leaflet. Medicine Class. finasteride 1mg cheap?
Pingback: klondayk2022
Pingback: irannews.ru
Pingback: Pills information in compensation patients. Effects of Soporific Abuse. buy generic avodart?
Pingback: uluro-ado
Pingback: rusnewsweek
Pingback: 24hours-news
Pingback: icf
Pingback: How can I get pregnant fast men viagra pills?
Pingback: www
Pingback: bep5w0Df
Pingback: cheap stromectol 6mg
Pingback: grandpashabet
Pingback: How do you ignore someone you love the most generic sildenafil without a prescription?
Pingback: Grandpashabet
Pingback: Does lemon help you lose weight and the hoodia appetite suppressant?
Pingback: bit.ly/3GQNK0J
Pingback: bit.ly/3ig2UT5
Pingback: bit.ly/3ARFdXA
Pingback: bit.ly/3gGFqGq
Pingback: bit.ly/3OEzOZR
Pingback: What can I do instead of smoking wellbutrin xl 300 mg generic?
Pingback: matchonline2022.ru
Pingback: tadalafil 20mg india
Pingback: cttdu.ru
Pingback: 1c789.ru
Pingback: sitestats01
Pingback: murang'a university
Pingback: murang'a university
Pingback: grandpashabet
Pingback: buy propecia online paypal
Pingback: propecia cheapest uk
Pingback: site 2023
Pingback: brutv
Pingback: tftl.ru
Pingback: edu-design.ru
Pingback: meritking
Pingback: newsukraine.ru
Pingback: history-of-ukraine.ru news ukraine
Pingback: mb588.ru
Pingback: 3o9cpydyue4s8.ru
Pingback: kin0shki.ru
Pingback: https://clck.ru/32JaEo
Pingback: dolpsy.ru
Pingback: https://bitbin.it/JI5X9Xvu/
Pingback: https://bitbin.it/bn1QAiBO/
Pingback: Murang'a University of Technology
Pingback: where can i get hydroxychloroquine
Pingback: madridbet
Pingback: rftrip.ru
Pingback: hydroxychloroquine price
Pingback: wwwi.odnoklassniki-film.ru
Pingback: must fees structure
Pingback: MUST school of agriculture
Pingback: 3DGofO7
Pingback: 3SoTS32
Pingback: 000-1
Pingback: psy-news.ru
Pingback: socionika-eniostyle.ru
Pingback: sezons.store
Pingback: video-2
Pingback: link
Pingback: meriking
Pingback: TwnE4zl6
Pingback: Dim Drakona 2022
Pingback: Usik Dzhoshua 2 2022
Pingback: pornoizle}
Pingback: A片
Pingback: psikholog moskva
Pingback: ìûøëåíèå
Pingback: aOuSjapt
Pingback: JGXldbkj
Pingback: Dom drakona
Pingback: sY5am
Pingback: stat.netstate.ru
Pingback: confeitofilm
Pingback: rodnoe-kino-ru
Pingback: filmgoda.ru
Pingback: cleantalkorg2.ru
Pingback: who makes cialis
Pingback: smotret-polnyj-film-smotret-v-khoroshem-kachestve
Pingback: liusia-8-seriiaonlain
Pingback: Anonymous
Pingback: cialis over the counter walmart
Pingback: film
Pingback: cost of cialis 5mg
Pingback: web
Pingback: mir dikogo zapada 4 sezon 4 seriya
Pingback: stromectol eye drops
Pingback: Ukraine-war
Pingback: UKRAINE
Pingback: stats
Pingback: buy stromectol 6mg online
Pingback: School of Pure and Applied Sciences Embu University
Pingback: Turkana University College
Pingback: University of Embu
Pingback: stromectol for lice
Pingback: ivermectin 3mg tab
Pingback: meritroyalbet
Pingback: https://bit.ly/psikholog-muzhchina-onlayn
Pingback: Psikholog
Pingback: ivermectin coronavirus
Pingback: hdorg2.ru
Pingback: 3NOZC44
Pingback: Øêàëà òîíîâ
Pingback: SHKALA TONOV
Pingback: https://ria.ru/20100906/272903623.html
Pingback: D6tuzANh
Pingback: qQ8KZZE6
Pingback: DPTPtNqS
Pingback: ivermectin 2ml
Pingback: bahis siteleri
Pingback: psy online
Pingback: slovar po psihoanalizu laplansh
Pingback: online moskva psiholog
Pingback: stromectol price usa
Pingback: psy-
Pingback: liquid ivermectin
Pingback: Netflix
Pingback: cialis tablets
Pingback: ivanesva
Pingback: XVIDEOSCOM Videos
Pingback: Xvideos
Pingback: 9-05-2022
Pingback: ivermectin side effects
Pingback: Bubble hash
Pingback: Litto
Pingback: Moroccan hash
Pingback: Bubble hash
Pingback: Haupia strain
Pingback: Watermelon haupia
Pingback: filmfilmfilmes
Pingback: Watermelon haupia
Pingback: mazhor4sezon
Pingback: amazon mushroom grow kit
Pingback: how to stop premature ejaculation
Pingback: ivermectin rx
Pingback: Latest News
Pingback: meritroyalbet giriş
Pingback: stromectol liquid
Pingback: ivermectin paste for humans
Pingback: virtual card buy with cryptocurrency
Pingback: canadian podcast
Pingback: best automatic penis pump
Pingback: rechargeable thrusting rabbit
Pingback: Payday Loans
Pingback: junk car removal
Pingback: Google
Pingback: cialis prices at walmart pharmacy
Pingback: Uncategorized
Pingback: Anxiety pills for sale
Pingback: management homework help
Pingback: hacendado
Pingback: stock market crash
Pingback: it support jona
Pingback: Nanaimo
Pingback: penis extension
Pingback: eurocasino
Pingback: eurocasino
Pingback: meritroyalbet
Pingback: Marijuana Delivery
Pingback: FN 509 LS EDGE FOR SALE
Pingback: stromectol ivermectin buy
Pingback: Real krt
Pingback: ivermectin in australia
Pingback: hydroxychloroquine online
Pingback: ivermectin buy canada
Pingback: marijuana-us.com
Pingback: Uganda safaris tours
Pingback: lucky land slots play now
Pingback: glock 28
Pingback: eyelash boxes
Pingback: madridbet
Pingback: when does cialis patent expire
Pingback: ivermectin 3
Pingback: male stroker
Pingback: Buy herbal incense online
Pingback: Herbal Incense
Pingback: Beretta 92fs For Sale
Pingback: apps for pc windows download
Pingback: celta
Pingback: MineFullTrader
Pingback: pc games for windows 10
Pingback: pc games for windows 8
Pingback: free download for pc windows
Pingback: games for pc download
Pingback: free windows app download
Pingback: download free apps apk for pc
Pingback: free download for windows 7
Pingback: ecomil
Pingback: cereal milk glo cart
Pingback: stromectol
Pingback: penis vacuum pump
Pingback: buy ivermectin from india
Pingback: eurocasino
Pingback: eurocasino
Pingback: stromectol online pharmacy
Pingback: bitcoin card
Pingback: elit escort
Pingback: stromectol brand
Pingback: furosemide tablets for sale
Pingback: meritking
Pingback: meritking
Pingback: furosemide pills
Pingback: meritroyalbet
Pingback: stromectol prescription
Pingback: buy ivermectin 3mg tablets
Pingback: ivermectin 3mg cost
Pingback: huge realistic dildos with balls
Pingback: Glock 34 for Sale
Pingback: ivermectin 9 mg tablet
Pingback: ivermectin tab price
Pingback: wavellite for sale
Pingback: remington v3 tac 13
Pingback: cialis price costco
Pingback: purchase ivermectin online
Pingback: buy generic stromectol
Pingback: ivermectin 12 mg tabs
Pingback: PlayStation 5 for Sale
Pingback: ivermectin mexico
Pingback: ivermectin 6 mg tablets for human
Pingback: purchase ivermectin
Pingback: ivermectin over the counter
Pingback: tadalafil 10mg prescription
Pingback: ivermectin prescription
Pingback: order cialis online without prescription
Pingback: ivermectin human dosage
Pingback: buy viagra online
Pingback: viagra connect
Pingback: cialis with dapoxetine
Pingback: live casino online deals
Pingback: ivermectin pills for people
Pingback: Google
Pingback: ivermectin for gapeworm
Pingback: sss tiktok
Pingback: stromectol price us
Pingback: cialis without a doctor prescription
Pingback: free slots that pay cash
Pingback: cialis coupon
Pingback: best herbal viagra
Pingback: prednisone
Pingback: ivermectin generic
Pingback: meritroyalbet
Pingback: how to get cialis discount
Pingback: cialis going generic
Pingback: how to use a remote controlled vibrator
Pingback: rechargeable wand massagers
Pingback: covid antiviral drug
Pingback: 1interstate
Pingback: cheap cialis without prescription
Pingback: best male stroker
Pingback: Buy dmt vape carts online Sydney Australia
Pingback: cialis over the counter
Pingback: prednisone 20mg is used for
Pingback: prednisone 20mg tablets side effects
Pingback: cialis goodrx
Pingback: online tadalafil prescription
Pingback: tombala siteleri
Pingback: cialis 20mg online
Pingback: cheap sildenafil online in usa
Pingback: sildenafil pills online purchase
Pingback: stromectol price in india
Pingback: Hk vp9 for sale
Pingback: tadalafil where to buy
Pingback: baymavi
Pingback: tadalafil liquid
Pingback: baymavi
Pingback: generic sildenafil tablets
Pingback: ordering tadalafil
Pingback: สมัคร lottovip
Pingback: Godfather Og strain
Pingback: generic cialis online
Pingback: generic cialis professional
Pingback: ivermectin tablet 1mg
Pingback: potenzmittel rezeptfrei
Pingback: tadalafil liquid
Pingback: ivermectin 5
Pingback: viagra on the cheap
Pingback: stromectol online
Pingback: cialis provigil interaction
Pingback: buy bulk ammo
Pingback: when to refinance your mortgage
Pingback: what is tadalafil
Pingback: meritroyalbet
Pingback: cialis prix
Pingback: cheap prednisone
Pingback: cialis kaufen
Pingback: ivermectin buy online
Pingback: madridbet
Pingback: Scrap Car Removal Richmond
Pingback: ignition casino united states
Pingback: ivermectin tablets for humans
Pingback: ivermectin in canada
Pingback: ivermectin tablets for humans
Pingback: ivermectin in india
Pingback: ivermectin uk
Pingback: ivermectin india
Pingback: one time visa card
Pingback: Anonymous
Pingback: ivermectin 200
Pingback: ivermectin buy uk
Pingback: ivermectin cream 5%
Pingback: ivermectin iv
Pingback: Bushmaster xm15 for sale
Pingback: ivermectin oral solution
Pingback: ivermectin 0.5% lotion
Pingback: stromectol pill
Pingback: oral ivermectin cost
Pingback: pharmacies
Pingback: zanaflex24
Pingback: molnupiravir pill
Pingback: Anonymous
Pingback: meritroyalbet
Pingback: meritroyalbet
Pingback: meritroyalbet
Pingback: https://setcialito.com/
Pingback: fertility clomid
Pingback: covid pill
Pingback: best sextoys
Pingback: aralen 25 mg
Pingback: ivermectin prescription
Pingback: dr syed haider
Pingback: Buy Marijuana Online
Pingback: tombala siteleri
Pingback: tombala siteleri
Pingback: tombala siteleri
Pingback: albuterol 26 mg
Pingback: ivermectin price usa
Pingback: trcasino
Pingback: durvet ivermectin
Pingback: levitra vs sildenafil
Pingback: natural viagra alternatives
Pingback: credit card to bitcoin
Pingback: tadalafil cost walgreens
Pingback: ivermectin tablets uk
Pingback: 108mcg albuterol
Pingback: elexusbet
Pingback: trcasino
Pingback: eurocasino
Pingback: ivermectin 5
Pingback: Bitcoin address wallet
Pingback: can cialis cause high blood pressure
Pingback: meritking
Pingback: cvs viagra
Pingback: elexusbet
Pingback: meritking
Pingback: madridbet
Pingback: eurocasino
Pingback: meritroyalbet
Pingback: Kilimanjaro Trek
Pingback: sex education
Pingback: colt python 2020
Pingback: waterproof vibrator
Pingback: https://clickviagrcan.com/
Pingback: woman and cialis
Pingback: buy generic viagra 50mg online
Pingback: buy oxycontin online
Pingback: https://mobviagrweb.com/
Pingback: ebay viagra tablets
Pingback: krt cart
Pingback: Bitcoin miner
Pingback: discount brand cialis
Pingback: Krt disposable vape
Pingback: krt vape cartridges
Pingback: how do i get cialis
Pingback: mossberg 930 jm
Pingback: beretta 1301 tactical for sale
Pingback: tudor north flag automatic watches
Pingback: clitoral stimulator
Pingback: keltec 22 rifle
Pingback: best clit vibrator
Pingback: double dildos
Pingback: Honda Ruckus For Sale
Pingback: divorce lawyers
Pingback: Kaufen Sie einen echten registrierten Führerschein
Pingback: big black dildo
Pingback: g spot vibrators
Pingback: how to use a g spot massager
Pingback: ruger mark iv lite
Pingback: online software
Pingback: Независимое бюро информации и аналитики
Pingback: order cigars online in bulk
Pingback: glo carts
Pingback: Paint Sprayer Buying Guide
Pingback: Buy Xanax pills Online
Pingback: Order Opana Online
Pingback: Gamma-butyrolactone for sale australia
Pingback: mp3
Pingback: Psilocybin mushrooms
Pingback: uca.com.vn
Pingback: Best Guns For Sale
Pingback: dpms ar 15 tpr
Pingback: buy ruger firearms online europe
Pingback: sildenafil 50mg coupon
Pingback: food delivery restaurants
Pingback: combine johimbe and cialis 5mg
Pingback: buy ayahuasca kit
Pingback: stiizy battery
Pingback: top gun supply
Pingback: blue dream stiiizy
Pingback: iwi tavor ts12 bullpup shotgun
Pingback: price of ivermectin
Pingback: shadow 2 optics ready
Pingback: benelli m3
Pingback: getzq.com
Pingback: - do si dos strain
Pingback: buy backlinks
Pingback: ecigarettes
Pingback: kimber guns for sale
Pingback: buy gbl online canada
Pingback: ecigarettes
Pingback: buy real drivers license online
Pingback: pentobarbital for sale
Pingback: cialis to buy
Pingback: Uganda Tour
Pingback: beretta 84 380 acp
Pingback: generic sildenafil 100mg
Pingback: DailyCBD
Pingback: browning citori field grade 20 gauge
Pingback: Lemon Tek
Pingback: walther q5 match pro
Pingback: powerful vibrator
Pingback: sex toys kit
Pingback: Fentanyl Patches for sale
Pingback: ultraman max
Pingback: the madmen of mandoras
Pingback: Baba Farid College of Higher Studies
Pingback: Shivaji Shikshan S. Eng N1 Ward, Mumbai (Suburban) - 400075
Pingback: Dakshineswar Sri Sri Sarada Devi Balika Vidyalaya Ward No. - 12, Kamarhatti Municipality, North Twenty Four Pargana - 700076
Pingback: best solar panels for RV
Pingback: portable power station for house
Pingback: RV solar generators
Pingback: e-cigarettes
Pingback: ruger rifles for sale
Pingback: affiliate marketing millionaire
Pingback: fake money for sale
Pingback: Buy Heineken Beer Bottle
Pingback: zkittlez cake strain
Pingback: how many letters in russian alphabet
Pingback: Virtual card Create instantly
Pingback: bitcoin wallet card
Pingback: happyruck
Pingback: NMD News
Pingback: www.happyruck.com
Pingback: Gorilla Trekking Safaris Uganda
Pingback: CableFreeTV Sports News
Pingback: Buy Buy Banana Diesel Strain of Marijuana Online
Pingback: mining rigs for sale
Pingback: https://www.kryptexminers.com/product/goldshell-kd5-18th-s-kadena-miner-brand-new-for-sale/
Pingback: Adderall For Sale Online
Pingback: Kolkata escorts
Pingback: Rent a car Bar, Montenegro
Pingback: priligy south africa
Pingback: prednisone 2.5 mg tab
Pingback: best testosterone booster
Pingback: azithromycin 250mg
Pingback: buy juul online
Pingback: albuterol 0.83
Pingback: stromectol uk
Pingback: buy real provigil
Pingback: priligy 30mg tablets
Pingback: prednisone drug
Pingback: buy undetectable counterfeit money online cheap
Pingback: quineprox 90 mg
Pingback: neurontin tablets
Pingback: lasix 160 mg
Pingback: online roulette ipad real money
Pingback: amoxil
Pingback: happyLuke
Pingback: MURANG'A UNIVERSITY
Pingback: live resin carridges
Pingback: in Canada
Pingback: tropical punch strain
Pingback: Tag Heuer Formula 1
Pingback: BUY LSD ONLINE
Pingback: male masturbators
Pingback: male masturbator
Pingback: buy viagra japan
Pingback: sulalemi sikin benim
Pingback: buy guns online australia
Pingback: beretta guns
Pingback: rawgarden.farm
Pingback: otc z pack
Pingback: savage grow plus
Pingback: Uganda Safari Holidays
Pingback: Kenya safari
Pingback: azithromycin zithromax over the counter
Pingback: average divorce rate in kenya
Pingback: bitcoin
Pingback: vertigo
Pingback: West Dean CofE Primary School
Pingback: Order Sig Sauer Guns Online
Pingback: RissMiner
Pingback: buy adhd online uk
Pingback: stock investment
Pingback: G19X COMPACT | 9X19MM
Pingback: Davide Pedersoli Sharps
Pingback: Vertise
Pingback: buy stairmaster
Pingback: cyberpowerpc infinity x109 gaming pc
Pingback: How to get to Murchison Falls National Park
Pingback: buy graphics card online usa
Pingback: buying cialis online canada
Pingback: Fennec Fox for Sale
Pingback: runtz cans
Pingback: order levitra super active oo
Pingback: costco gaming chairs
Pingback: buy priligy dapoxetine online
Pingback: cockatoo for sale
Pingback: s&w 642 for sale
Pingback: beretta 96 for sale
Pingback: canadian marble fox
Pingback: pods mango
Pingback: when should i take lisinopril hctz
Pingback: albuterol sulfate 0.083% side effects
Pingback: best ed pills non prescription
Pingback: buy marijuana online usa
Pingback: background check website
Pingback: where can i buy a viagra
Pingback: buy zithromax overnight
Pingback: cialis generic pharmatize
Pingback: magic mushrooms
Pingback: magic mushrooms
Pingback: stiiizy battery alternative Archives
Pingback: buy sodium pentobarbital
Pingback: mossberg 590 nightstick for sale
Pingback: hangover slot machine for sale
Pingback: zip 22 for sale
Pingback: sig sauer emperor scorpion
Pingback: kimber k6s for sale
Pingback: peak prosperity ivermectin
Pingback: colt 45 cattleman revolver
Pingback: dosing for ivermectin
Pingback: ivermectin for foxes
Pingback: SMART CARTS FOR SALE
Pingback: ivermectin mechanism of action in scabies
Pingback: buy ventolin evohaler 100 micrograms
Pingback: scabies treatment ivermectin dose
Pingback: Buy Percocet online
Pingback: ivermectin dose for goats
Pingback: ivermectin cvs over the counter
Pingback: durvet ivermectin pour on for cattle
Pingback: how does ivermectin kill scabies
Pingback: cvs pharmacy zithramax
Pingback: lowes sso
Pingback: sajt
Pingback: ivermectin scabies treatment
Pingback: tadalafil 2.5 mg generic
Pingback: stromectol 875mg
Pingback: aromatherapy for anxiety
Pingback: cialis where to buy
Pingback: ارقام بنات
Pingback: Serengeti African safari
Pingback: shipping containers for sale
Pingback: FARMING EQUIPMENT FOR SALE IN ZIMBABWE
Pingback: best male sex toys
Pingback: prednisolone vs prednisone
Pingback: 3 Days volcanoes gorilla tour
Pingback: Macbook akku schnell leer rüti
Pingback: propecia 1mg price
Pingback: Great migration Africa
Pingback: Livestock for sale
Pingback: Pinball Machines for Sale
Pingback: Mac akku service pfäffikon
Pingback: buy amoxil online no prescription
Pingback: Sig Sauer Guns For Sale
Pingback: Computer Repair Bristol
Pingback: Maintenance site web
Pingback: sugar gliders for sale
Pingback: ivermectin 1000mg
Pingback: mp3 juices
Pingback: download pc games for windows 7
Pingback: free download for windows 7
Pingback: full apps download
Pingback: free download for windows 10
Pingback: free app for laptop
Pingback: free download for windows 7
Pingback: pc games for windows 7
Pingback: cymbalta drug interactions
Pingback: برنامج تروكولر
Pingback: 1
Pingback: rabbit vibrator
Pingback: male sex toys
Pingback: tadalafil tablets 80 mg
Pingback: us online pharmacies
Pingback: St Agnes CofE Primary School
Pingback: generic cialis for sale
Pingback: NAPHYRONE FOR SALE
Pingback: cialis europe
Pingback: hydroxychloroquine 200mg dose
Pingback: West Highland White Terrier puppy for sale
Pingback: Macaw for sale
Pingback: cialis online bestellen
Pingback: zasto sluzi lijek escitalopram 10 mg na hrvatskom jeziku
Pingback: big chief extracts price
Pingback: odorex
Pingback: stromectol for tooth
Pingback: Queen Elizabeth National Park
Pingback: rabbits foot luck
Pingback: atorvastatin vs simvastatin side effects
Pingback: how long does it take for hydrochlorothiazide to get out of your system
Pingback: 피망포커머니
Pingback: 안전놀이터
Pingback: ruger 10 22 carbine for sale
Pingback: amity school sector 43 gurgaon
Pingback: lexapro and wellbutrin combination weight loss
Pingback: drugs similar to lyrica
Pingback: best in ottawa
Pingback: zoloft vs.wellbutrin
Pingback: realistic male masturbator
Pingback: 1xbit download
Pingback: quetiapine extended release vs immediate release
Pingback: electric penis pump
Pingback: vibrating penis ring
Pingback: sex
Pingback: plaquenil and malaria prophylaxis
Pingback: sex toy facts
Pingback: prilosec alcohol
Pingback: prozac sexual side effects
Pingback: realistic pocket stroker
Pingback: webmd tamoxifen
Pingback: is sildenafil generic
Pingback: atorvastatin withdrawal
Pingback: download video tw
Pingback: CTRLCOIN
Pingback: ciprofloxacin antibiotic dosage
Pingback: melhores smartphones
Pingback: french streaming
Pingback: site de streaming
Pingback: vidalista pills at walmart
Pingback: shift a car
Pingback: streamcomplet
Pingback: 99defi network - decentralized p2p
Pingback: avrupa yakasi escort
Pingback: Marijuana Wax for Sale
Pingback: سکس علیرضا
Pingback: thick dildo
Pingback: big dildo
Pingback: best sex toys for men
Pingback: best p spot vibrators
Pingback: ruay สมัครสมาชิก
Pingback: lottovip สมัคร
Pingback: ground leases
Pingback: MILF Porn
Pingback: hosting deals
Pingback: Male Masturbator
Pingback: rechargeable vibrator
Pingback: vibrating pocket stroker
Pingback: rechargeable panty vibrator
Pingback: ivermectin 12 mg dosage
Pingback: fun88
Pingback: can i buy prednisone online
Pingback: shop marijuana online
Pingback: buy clomid scabies
Pingback: priligy drug
Pingback: silicone prostate vibrator
Pingback: thrusting vibrator rabbit"
Pingback: advanced kegel balls
Pingback: ivermectil package insert pdf
Pingback: kozyatagi escort
Pingback: https://regcialist.com/
Pingback: AMI Healthcare International Hospital Operations Management
Pingback: 200mg viagra
Pingback: porn stars masturbators
Pingback: wand massagers
Pingback: cryptocurrency
Pingback: advanced care rx pharmacy
Pingback: libido max vs viagra
Pingback: cheap generic cialis
Pingback: does insurance cover viagra
Pingback: pharmacy salaries in canada
Pingback: canadian pharmacy safe
Pingback: how to masturbate using cock extension
Pingback: best male masturbator
Pingback: tetracycline and dairy products
Pingback: where to buy a ruger
Pingback: buy kush weed online
Pingback: معرفة هوية المتصل
Pingback: buy Juul pods online
Pingback: Cryptocurrency HBCUC
Pingback: Canadian service
Pingback: sex toys at adam and eve
Pingback: how to lose belly fat fast
Pingback: 450 bushmaster ammo for sale
Pingback: Canadian Marble Fox
Pingback: Wooden Sofa
Pingback: Roofer
Pingback: hydroxychloroquine kills cancer
Pingback: successful hydroxychloroquine trials
Pingback: hydroxychloroquine for sjogren's syndrome
Pingback: MUT
Pingback: Obligasi.com
Pingback: hydroxychloroquine for sale online
Pingback: weed concentrates for sale
Pingback: abc rifle company
Pingback: tiktok followers
Pingback: buy weed
Pingback: buy weed online
Pingback: buy weed
Pingback: ivermectin for scabies side effects
Pingback: pocket vibrator
Pingback: male masturbator review
Pingback: everything free dating sites
Pingback: buy weed near me
Pingback: buy delta 8 THC
Pingback: Edibles
Pingback: blogery_i_dorogi
Pingback: Company Registration
Pingback: tides today at tides.today
Pingback: sex toys for large girls
Pingback: best delta 8 thc gummies
Pingback: buy Instagram likes
Pingback: podolsk-region.ru
Pingback: best kratom
Pingback: best kratom capsules
Pingback: soderzhanki-3-sezon-2021.online
Pingback: cytotmeds.com
Pingback: ATTA CHAKKI
Pingback: latest technology. news
Pingback: PARROTS FOR SALE
Pingback: THC Cartridge
Pingback: used pinball machines for sale cheap
Pingback: viagra prank
Pingback: cialis liquid
Pingback: where to buy azithromycin online
Pingback: viagra canada
Pingback: silicone vibrator
Pingback: cialis free sample
Pingback: sex toys for women
Pingback: generic viagra sales
Pingback: tadalafil generic cost
Pingback: doxycycline for canines
Pingback: best strap on dildos
Pingback: Weed for Sale
Pingback: ciprofloxacin ear infection
Pingback: sildenafil us pharmacy
Pingback: thrusting anal vibe
Pingback: sex
Pingback: cialis online order
Pingback: electric motorcycle
Pingback: slot online
Pingback: best canadian pharmacy
Pingback: pendik esc
Pingback: assault rifles for sale
Pingback: best clitoral vibrator
Pingback: alex more
Pingback: generic cialis with dapoxetine
Pingback: Ruger sr9 for sale
Pingback: mobile homes for sale in westmoreland county pa
Pingback: best ejaculating dildo
Pingback: generic tadalafil india
Pingback: buy prescription drugs online without
Pingback: how to get cialis without a doctor
Pingback: sulfamethoxazole tmp ds tablet 800 160
Pingback: liquid cialis buy
Pingback: online pharmacy oxycodone 30mg
Pingback: cost of cialis 5mg in canada
Pingback: top
Pingback: online pharmacy australia paypal
Pingback: tadalafil 20 mg best price in india
Pingback: mylan tadalafil vs cialis
Pingback: if viagra doesnt work will cialis
Pingback: buy ativan mexico
Pingback: is ordering cialis online legal
Pingback: jewish dating site free
Pingback: site
Pingback: Ukrainskie-serialy
Pingback: afisha-kinoteatrov.ru
Pingback: monthly cost of without insurance
Pingback: cialis 2.5 mg
Pingback: much does cost without insurance
Pingback: monthly cost of without insurance
Pingback: female viagra walgreens
Pingback: video
Pingback: topvideos
Pingback: kinoteatrzarya.ru
Pingback: tinder message failed to send
Pingback: dirty tinder photos
Pingback: allied cash advance pittsburgh
Pingback: ez online pharmacy viagra
Pingback: verschil tussen viagra en cialis
Pingback: retino a india
Pingback: projectio-freid
Pingback: psy2022
Pingback: psy
Pingback: fast cash advance mountain view
Pingback: news news news
Pingback: buy without perscription
Pingback: cheap generic cialis
Pingback: cialis online from canada
Pingback: michigan governor wants hydroxychloroquine
Pingback: cialis with dapoxetine from canada
Pingback: generic cialis in ireland
Pingback: best place to buy prednisone
Pingback: 4569987
Pingback: Astelin
Pingback: Zakhar Berkut
Pingback: cost of tadalafil without insurance
Pingback: furosemide cost usa
Pingback: best price prescription drugs
Pingback: cuanto sale levitra en argentina
Pingback: safe buy cialis
Pingback: best cialis substitute
Pingback: sildenafilo 5 mg comprar
Pingback: hydroxychloroquine covid 19 studies
Pingback: buy online cialis
Pingback: mexican pharmacy online medications
Pingback: viagra gif australia
Pingback: dick on viagra australia
Pingback: buy tadalafil 20mg price canada
Pingback: buy cialis in australia online
Pingback: does hydroxychloroquine really work
Pingback: hydroxychloroquine sulfate 800 mg
Pingback: compro sildenafilo
Pingback: cost of viagra 2018
Pingback: cheapest sildenafil 100 mg online
Pingback: viagra tablet buying low cost
Pingback: cialis 20 mg cost
Pingback: cialis 20mg price in canada
Pingback: ampicillin rate of infusion
Pingback: tadalafil 5mg reviews
Pingback: cialis with dapoxetine to buy uk
Pingback: hydroxychloroquine sulfate tablet
Pingback: viagra pharmacy 100mg
Pingback: prescription cost comparison
Pingback: plaquenil and covid
Pingback: paxil acne
Pingback: interactions for cephalexin
Pingback: marley drugs tadalafil
Pingback: cheap cialis mexico
Pingback: metformin generic
Pingback: neurontin medscape
Pingback: closest thing to viagra
Pingback: what is brand cialis
Pingback: generic cialis cost
Pingback: taking the new 60 mg cialis
Pingback: how long does viagra last
Pingback: sildenafil viagra 100mg
Pingback: guy on viagra
Pingback: generic cialis]
Pingback: walmart viagra
Pingback: cialis generic pills
Pingback: sildenafil generic sildenafil
Pingback: how long does sildenafil last in system
Pingback: vidalista daily online
Pingback: 3 some viagra prank
Pingback: sex with cialis
Pingback: canada toronto cheap fase cialis
Pingback: tadalafil brand name india
Pingback: best online paper writing service
Pingback: cialis over the counter in canada
Pingback: cheap essay online
Pingback: tadalafil order online no prescription
Pingback: propecia for prostate
Pingback: dissertation structure
Pingback: professional essay writer
Pingback: where to get generic viagra
Pingback: what is the best custom essay site
Pingback: help thesis
Pingback: dissertation online help
Pingback: tadalafil 100mg price
Pingback: college essay editing services
Pingback: azithromycin 500 mg dosage instructions
Pingback: prednisone 50 mg taper
Pingback: thesis binding service
Pingback: daily cialis prescription
Pingback: help with writing an essay
Pingback: sildenafil 50mg
Pingback: synthroid while pregnant
Pingback: metoclopramide pills
Pingback: diy viagra recipes
Pingback: buy diflucan otc
Pingback: buy viagra on line
Pingback: priligy for sale
Pingback: tadalafil 5mg generic
Pingback: levitra coupon
Pingback: provera clomid
Pingback: prednisolone 5mg dosage
Pingback: doxycycline drug class
Pingback: where can i buy metoprolol 25 mg
Pingback: buying viagra online
Pingback: viagra stock
Pingback: loviagraosn viagra
Pingback: viagra accident
Pingback: viagra over counter
Pingback: gemfibrozil coupon
Pingback: how much is viagra
Pingback: viagra naturale
Pingback: mail order viagra
Pingback: viagra connect
Pingback: viagra 100 mg
Pingback: albuterol cheapest price
Pingback: how long will viagra keep
Pingback: ivermectin 50 mg
Pingback: azithromycin no prescription
Pingback: furosemide india
Pingback: buy amoxicillin online no prescription
Pingback: 2.5 mg tadalafil generic daily
Pingback: levothyroxine mcg medication
Pingback: buy cialis tadalafil tablets
Pingback: good rx aurogra 100mg
Pingback: acyclovir zovirax over counter
Pingback: terbinafine united kingdom
Pingback: hydroxychloroquine for arthritis
Pingback: lamotrigine tablets
Pingback: hydroxychloroquine ontario
Pingback: hydroxychloroquine 90
Pingback: how do you use cialis
Pingback: tadalafil buy online
Pingback: hydroxychloroquine dosage for lupus
Pingback: cialis 20mg low price
Pingback: tadalafil soft tabs cheap
Pingback: cialis tab 5mg sale
Pingback: sildenafil pills
Pingback: business management essay
Pingback: buy cialis tadalafil tablets
Pingback: help with writing an essay
Pingback: what should i write my college essay on
Pingback: how to write a research question
Pingback: best essay writing services
Pingback: maximum viagra dose
Pingback: vardenafil versus viagra
Pingback: viagra without a doctor prescription
Pingback: precio viagra generico
Pingback: cialis in europe
Pingback: propranolol without prescription
Pingback: buy cialis cheap canada
Pingback: tadalafil without a doctors prescription
Pingback: viagra price
Pingback: azathioprine price
Pingback: cheapest generic cialis australia
Pingback: tadalafil citrate
Pingback: cheap viagra online
Pingback: buy cialis tadalafil tablets
Pingback: cialis canada price
Pingback: como tomar cialis 20 mg
Pingback: cheap loperamide
Pingback: beli cialis century
Pingback: amazon sildenafil citrate
Pingback: sumatriptan 100mg tablet
Pingback: azithromycin side effects
Pingback: isosorbide cost
Pingback: hydroxychloroquine sulfate side effects
Pingback: viagra 100mg reviews
Pingback: viagra effective
Pingback: glipizide otc
Pingback: how to take zithromax for gonorrhea
Pingback: how long for ivermectin to enter blood stream
Pingback: duloxetine 20 mguses
Pingback: waarom is viagra verboden
Pingback: cost of nitrofurantoin 100 mg
Pingback: wat kost sildenafil sandoz 100 mg
Pingback: how long does it take for cialis 5mg to work
Pingback: how much is viagra in australia
Pingback: cephalexin doseage for staph infections
Pingback: alendronate 70 mg generic
Pingback: original cialis low price
Pingback: meclizine25 and celebrex
Pingback: fluticasone mcg without a prescription
Pingback: iyfzmcpx
Pingback: cialis otc
Pingback: azithromycin birth control interaction
Pingback: tamsulosin 0.4mg nz
Pingback: how to buy etodolac 300mg
Pingback: how to buy cialis online from canada
Pingback: estradiol 2 mg online pharmacy
Pingback: tnkqbwyz
Pingback: how-to-buy-cialis
Pingback: 141generic2Exare
Pingback: how much does cialis cost with insurance
Pingback: erythromycin 500 mg united states
Pingback: what is cialis
Pingback: permethrin 30g without prescription
Pingback: amoxicillin with clavulanate potassium
Pingback: how to make chloroquine
Pingback: cheapest amitriptyline 25mg
Pingback: canada cialis online
Pingback: cymbalta make you horney
Pingback: wife permission needed to buy viagra
Pingback: venlafaxine 75mg without prescription
Pingback: cheap generic cialis
Pingback: 2000mg f keflex
Pingback: bisacodyl without a doctor prescription
Pingback: rx online no prior prescription
Pingback: is celebrex good for toothache
Pingback: doxycycline pharmacy
Pingback: does azithromycin contain penicillin
Pingback: oxybutynin 2.5mg no prescription
Pingback: phenytoin uk
Pingback: amoxicillin without a prescription
Pingback: cialis 5mg tablet
Pingback: where to buy fluconazole
Pingback: viagra levitra cialis offers
Pingback: acetazolamide uk
Pingback: buy viagra with echeck
Pingback: order tolterodine
Pingback: cheap divalproex
Pingback: where to buy rosuvastatin
Pingback: ivermectin from canada
Pingback: vidalista without doctor prescription
Pingback: buy cialis without perscription
Pingback: what is aurogra 100mg tablets
Pingback: how to purchase warfarin 1mg
Pingback: viagra cost in mexico
Pingback: carvedilol online pharmacy
Pingback: do i need a prescription to buy viagra online
Pingback: rx party cialis
Pingback: cialis in europe
Pingback: prochlorperazine 5mg price
Pingback: clozapine 50mg tablet
Pingback: buy cialis online best price
Pingback: clindamycin without prescription
Pingback: generic cialis with dapoxetine 80mg
Pingback: ciprofloxacin medication
Pingback: buy cialis tadalafil tablets
Pingback: cialis overnighted
Pingback: cephalexin tablets
Pingback: citalopram 10mg online
Pingback: cialis 20 mg from united kingdom
Pingback: cefuroxime 250mg online
Pingback: can vidalista cause weight gain
Pingback: clonidine otc
Pingback: buspirone pills
Pingback: olmesartan over the counter
Pingback: dutasteride coupon
Pingback: irbesartan 300 mg online
Pingback: anastrozole 1 mg for sale
Pingback: Google
Pingback: donepezil 10 mg price
Pingback: atomoxetine 25mg tablet
Pingback: meclizine 25 mg usa
Pingback: glimepiride purchase
Pingback: fexofenadine 180mg uk
Pingback: female viagra on sale today
Pingback: spironolactone otc
Pingback: generic cialis online india pharmacy
Pingback: pioglitazone pills
Pingback: aripiprazole no prescription
Pingback: escitalopram 20mg australia
Pingback: furosemide 40 mg nz
Pingback: tadalafil 20 mg nz
Pingback: how to purchase sildenafil
Pingback: hydroxychloroquine use for fibromyalgia
Pingback: zyvox 600mg no prescription
Pingback: online viagra surrey
Pingback: zyprexa canada
Pingback: where can i buy zyloprim
Pingback: cost of generic cefixime
Pingback: zovirax without a prescription
Pingback: cheapest zocor
Pingback: click reference
Pingback: long term side effects of cialis
Pingback: zanaflex 4 mg without prescription
Pingback: viagra pills without doctor's prescription
Pingback: order wellbutrin 300mg
Pingback: voltaren 50mg nz
Pingback: verapamil tablets
Pingback: valtrex uk
Pingback: viagra without a doctor prescription fast
Pingback: tricor 160mg cost
Pingback: viagra results before and after
Pingback: cheap toprol 50mg
Pingback: thorazine prices
Pingback: cialis best price cvs
Pingback: tenormin 25 mg united states
Pingback: spiriva generic
Pingback: ivermectin dosage chart for humans
Pingback: cialis 5 mg daily effectiveness
Pingback: how to purchase skelaxin
Pingback: singulair cost
Pingback: seroquel 25 mg no prescription
Pingback: rogaine otc
Pingback: robaxin 500 mg nz
Pingback: cost of risperdal
Pingback: how to purchase revatio 20 mg
Pingback: order viagra
Pingback: retin-a cream 0.05% canada
Pingback: remeron pharmacy
Pingback: cost of generic viagra
Pingback: reglan coupon
Pingback: pyridium uk
Pingback: cialis medication
Pingback: viagra price in pakistan
Pingback: buy pulmicort 100 mcg
Pingback: actual sex with viagra
Pingback: buy provigil
Pingback: effects of viagra in women
Pingback: protonix cost
Pingback: acyclovir and covid 19
Pingback: proscar 5 mg canada
Pingback: citalopram davis drug pdf
Pingback: celebrex shelf life
Pingback: cost of procardia 30 mg
Pingback: proair inhaler 100 mcg purchase
Pingback: carvedilol 10mg
Pingback: prilosec canada
Pingback: buspirone liver function
Pingback: cost of prevacid
Pingback: cheap prednisolone
Pingback: what are the side effects of prednisone
Pingback: buspirone fo ed
Pingback: buy plaquenil
Pingback: cialis and xanax interaction
Pingback: phenergan tablets
Pingback: on bupropion for smoking
Pingback: viagra super active ingredients
Pingback: periactin 4mg otc
Pingback: where can i buy brand name cialis online
Pingback: can you mix baclofen with hydrocodone
Pingback: nortriptyline canada
Pingback: grant pharmacy dapoxetine generic
Pingback: baclofen dosage adults
Pingback: online canadian pharmacy
Pingback: motrin 400 mg online pharmacy
Pingback: hydroxychloroquine availability otc
Pingback: walmart online pharmacy
Pingback: mobic 7,5 mg tablets
Pingback: can azithromycin tablets be crushed
Pingback: legit online pharmacy
Pingback: cost of micardis
Pingback: canada drugs online pharmacy
Pingback: atorvastatin afib
Pingback: canadian pharmacy no prescription needed
Pingback: mestinon 60mg online
Pingback: what tier is aripiprazole
Pingback: viagra chewing gum
Pingback: where to buy meclizine 25 mg
Pingback: macrobid without a prescription
Pingback: amoxicillin no prescription
Pingback: how to purchase luvox
Pingback: lopressor 100mg online
Pingback: amlodipine withdrawal
Pingback: how to purchase lopid 300 mg
Pingback: elavil used for pain
Pingback: levaquin 250mg tablet
Pingback: best time of day to take amiodarone
Pingback: cheapest lamisil 250mg
Pingback: cheap indocin 75mg
Pingback: colchicine allopurinol initiation
Pingback: 2019 abilify lawsuit lawyers
Pingback: doxycycline antimicrobial coverage
Pingback: imuran without a doctor prescription
Pingback: cialis 5 mg cost
Pingback: difference between sildenafil and tadalafil
Pingback: zanaflex tablet vs capsule
Pingback: over the counter viagra
Pingback: active ingredient in viagra
Pingback: how long does it take viagra to work
Pingback: reference
Pingback: plaquenil copay assistance
Pingback: viagra connect cvs
Pingback: imodium cheap
Pingback: oxybutynin 5mg diagnosis
Pingback: hydroxychloroquine manufacturer
Pingback: cialis and alcohol
Pingback: ciprofloxacin hcl 500 mg antibiotics
Pingback: viagra vs cialis
Pingback: cialis buy online
Pingback: cialis pill
Pingback: imdur coupon
Pingback: will cephalexin cause discolor inurin
Pingback: cialis ordering
Pingback: hyzaar tablets
Pingback: where can i buy geodon 20 mg
Pingback: buy generic viagra
Pingback: albuterol sulfate nebulizer solution dose
Pingback: viagra coupons
Pingback: garcinia cambogia 100caps pills
Pingback: essay writing service law
Pingback: buy flonase nasal spray 50 mcg
Pingback: foreign pharmacies online
Pingback: cialis pills
Pingback: order cialis india
Pingback: flomax 0,2 mg without prescription
Pingback: augmentin price without insurance
Pingback: etodolac 400mg pharmacy
Pingback: cialis for sale
Pingback: erythromycin uk
Pingback: where can i buy elavil 10 mg
Pingback: typical cialis dosage
Pingback: dramamine 50 mg nz
Pingback: how to get a prescription
Pingback: doxycycline 100 mg usa
Pingback: Buy cheap viagra internet
Pingback: order diltiazem 120 mg
Pingback: cost of differin
Pingback: flomax and dapoxetine side effects
Pingback: diamox uk
Pingback: depakote without prescription
Pingback: what dosage does vidalista come in
Pingback: ddavp 10mcg otc
Pingback: psychology thesis
Pingback: dapsone 1000caps united kingdom
Pingback: thesis writing help uk
Pingback: best research paper writing service reviews
Pingback: write my paper for money
Pingback: dissertation search
Pingback: essay service cheap
Pingback: cymbalta 20 mg online
Pingback: help with writing essays
Pingback: customessaywriterbyz.com
Pingback: crestor tablet
Pingback: soft generic viagra usa
Pingback: cheapest cozaar
Pingback: coumadin 2 mg canada
Pingback: Viagra 50 mg
Pingback: generic cialis
Pingback: compazine prices
Pingback: marley drug viagra
Pingback: does lisinopril interact with cialis
Pingback: combivent uk
Pingback: cialis miami
Pingback: symbicort inhaler 160/4,5mcg without a doctor prescription
Pingback: viagra cheap
Pingback: order colchicine 0,5 mg
Pingback: Viagra mail order
Pingback: taking viagra
Pingback: hydroxychloroquine 400
Pingback: viagra price walgreens
Pingback: clozaril without a prescription
Pingback: jodi west viagra
Pingback: clonidine united states
Pingback: 007 viagra
Pingback: clomid canada
Pingback: where can i buy cleocin 150mg
Pingback: college admission essay writing service
Pingback: buy essay
Pingback: mba essay writing service
Pingback: mba essay writing service
Pingback: buy sildenafil citrate
Pingback: writer essay
Pingback: research paper writer free
Pingback: vidalista 2.5 mg
Pingback: fake essay writer
Pingback: atorvastatin h102
Pingback: buy custom essays online
Pingback: buy viagra now
Pingback: admission essay writing services
Pingback: who makes cialis
Pingback: Generic viagra us
Pingback: australia essay writing service
Pingback: sildenafil from mexico
Pingback: generic viagra pills
Pingback: cbd oil for sale online and reviews
Pingback: cost of viagra
Pingback: buy levitra online
Pingback: clomid 50 mg tablet price
Pingback: cbd oil for cancer for sale
Pingback: my dick on viagra
Pingback: viagra pills uk
Pingback: buy viagra prescription
Pingback: best cbd oil for cancer for sale
Pingback: side effects viagra
Pingback: cbd oil for pain for sale
Pingback: how to make viagra
Pingback: buy levitra fast delivery
Pingback: best price generic vidalista
Pingback: best cbd oil for pain management
Pingback: fast delivery viagra australia
Pingback: viagra for women online
Pingback: contraindications for ivermectin use
Pingback: canadian cialis
Pingback: cherry flavored cbd oil
Pingback: drugstore female viagra
Pingback: buy cbd oil with thc
Pingback: cialis 5mg
Pingback: cbd oil sale
Pingback: vardenafil
Pingback: generic cialis
Pingback: the best cbd oil on the market
Pingback: cialis and alcohol
Pingback: personal loans with no credit check
Pingback: where to buy viagra online safely
Pingback: viagra 6 free sample
Pingback: payday loans corinth ms
Pingback: viagra no prescription
Pingback: bad credit loans tulsa
Pingback: female viagra reviews
Pingback: legit quick loans
Pingback: best installment loans
Pingback: payday loans near me
Pingback: 3 month payday loans
Pingback: personal loans california
Pingback: cheapest online car insurance quotes
Pingback: buy cialis brand
Pingback: buy cialis usa
Pingback: car insurance quotes california
Pingback: multiple car insurance quotes
Pingback: buy cialis brand
Pingback: best car insurance quotes companies
Pingback: good2go car insurance quotes
Pingback: alliance car insurance quotes
Pingback: cheap car insurance quotes in michigan
Pingback: viagra pill for women
Pingback: direct line car insurance quotes
Pingback: top car insurance
Pingback: bimatoprost vs latisse
Pingback: geico car insurance quotes
Pingback: gambling casino
Pingback: play casino
Pingback: gambling casino
Pingback: best online casino real money
Pingback: generic viagra online
Pingback: online casino real money
Pingback: play casino online
Pingback: slot machine
Pingback: online casino usa real money
Pingback: online casino real money usa
Pingback: vegas casino online
Pingback: claritin generic
Pingback: cipro coupon
Pingback: https://apnews.com/press-release/newmediawire/lifestyle-diet-and-exercise-exercise-2d988b50b0b680bee24da8e46047df20
Pingback: cephalexin tablets
Pingback: celexa coupon
Pingback: celebrex pharmacy
Pingback: ceftin without prescription
Pingback: how to buy ceclor
Pingback: catapres cheap
Pingback: casodex 50 mg generic
Pingback: cardizem 180 mg no prescription
Pingback: viagra paypal uk
Pingback: calcium carbonate 500mg generic
Pingback: over the counter hydroxychloroquine for sale
Pingback: buy cialis online in usa
Pingback: Biaxin 500mg cheap
Pingback: generic cialis best price
Pingback: benicar 20 mg without prescription
Pingback: keflex.webbfenix.com
Pingback: bactrim 400/80 mg price
Pingback: cheap viagra online australia
Pingback: cheap augmentin 500/125 mg
Pingback: atarax 25 mg pharmacy
Pingback: cialis risks
Pingback: amoxicillin 500mg capsules cost
Pingback: aricept 10mg price
Pingback: mtabs viagra
Pingback: cialistodo.com
Pingback: arava 20 mg united states
Pingback: antivert 25mg online
Pingback: antabuse 500 mg usa
Pingback: amoxicillin 250 mg without a prescription
Pingback: amaryl 4mg purchase
Pingback: cost of allopurinol 300 mg
Pingback: allegra 180 mg price
Pingback: how to purchase aldactone 100 mg
Pingback: abilify 15 mg pills
Pingback: viagra substitute
Pingback: cheap viagra generic
Pingback: where to buy viagra
Pingback: lexapro 20mg no prescription
Pingback: propecia 1mg medication
Pingback: furosemide 40mg united states
Pingback: tadalafil 10mg without prescription
Pingback: sildenafil 120 mg pills
Pingback: Cialis 80 mg australia
Pingback: www.azhydroxychloroquine.com
Pingback: Cialis 20mg tablet
Pingback: http://lm360.us/
Pingback: where to buy Cialis 40mg
Pingback: cheap Cialis 20mg
Pingback: non prescription viagra
Pingback: viagra cheap
Pingback: cialis online pharmacy
Pingback: cialis ed
Pingback: prices of cialis
Pingback: viagra online generic
Pingback: how to buy real viagra online
Pingback: cialis generic online
Pingback: sildenafil 100mg
Pingback: viagra samples
Pingback: viagra online
Pingback: online casinos
Pingback: real casino online
Pingback: online casino games
Pingback: cialis 5 mg
Pingback: cialis to buy
Pingback: generic cialis
Pingback: new cialis
Pingback: best real money online casinos
Pingback: cialis 5 mg
Pingback: slot machines for sale
Pingback: golden nugget online casino
Pingback: Medical and health information
Pingback: online casinos
Pingback: PhenQ helps in losing weight
Pingback: viagra pills
Pingback: Information on Brain and Nootropics
Pingback: rtg casino list
Pingback: loans online
Pingback: payday loans
Pingback: personal loan
Pingback: legitimate online slots for money
Pingback: play online casino real money
Pingback: viagra 100mg
Pingback: real casinos online no deposit
Pingback: casino games online
Pingback: order vardenafil
Pingback: vardenafil dosage
Pingback: vardenafil pill
Pingback: generic cialis online
Pingback: cialis mastercard
Pingback: canada online pharmacy
Pingback: canada pharmacy
Pingback: online pharmacy
Pingback: erectile dysfunction pills
Pingback: non prescription erection pills
Pingback: new ed pills
Pingback: viagra 100mg
Pingback: cheap viagra
Pingback: viagra 100mg
Pingback: viagra cialis
Pingback: is there a generic cialis available?
Pingback: when will cialis be over the counter
Pingback: how to get cialis
Pingback: cialis 20mg price
Pingback: Generic viagra in canada
Pingback: Free trial of viagra
Pingback: cialis online canada
Pingback: generic for cialis
Pingback: goodrx cialis
Pingback: Free trial of viagra
Christina with Occubit took care of a major and recurring security issue I was having with my personal email and Facebook. I have never experienced IT support like I did working with her. She went above and beyond and combed through several email accounts and my social media accounts to remove malicious settings that a hacker had put in. She set all my accounts to have 2-step verification after the clean up to prevent the perp from getting in again. She also did some investigative work and even found out how my password got leaked in the first place. I deeply appreciate her attention to detail and genuine concern about the security of my accounts. I would highly recommend any business who needs IT consulting or technical support to give Occubit a call if they want more than just a quick fix or band aid for their technology issues.