Spilled Coffee, Dropped, and Infected: What Data Disasters Look Like
- October 10, 2017
- Business, Business advice, Tech Biz Bytes, Technology
We’ve all been there in one way or another. Dropping a phone in the pool, knocking a laptop off the arm of the couch, or spilling coffee on your keyboard. Here are some tips and tricks to prepare for these accidents and what to do after the fact.
Dropped Bumped Smashed
- Cracked screens on laptops, tablets, and phones. Good news, your data is likely still safe even if you can’t see anything on your screen and can be easily recovered.
- Physical damage to internal data storage (hard disk drive or HDD) can present in a few ways and is most frequently caused by drops or bumps. You may hear an unusual revving or clicking sound, see an error message ‘no boot disk found’, or have random blue-screens/shut downs. This is far more likely to happen to a laptop as it uses a mechanical hard disk for recording information, where as all tablets and phones use flash memory. Solid State Drives are large versions of flash memory and will be found in many Ultrabooks and high end Laptops. While these types of memory storage also can fail, the risk is substantially reduced when compared to a traditional hard disk drive. We can perform data recoveries on physically damaged disks or setup a secure and encrypted backup to prevent catastrophic data loss.
Water Coffee Rain
- Spilled coffee on your laptop keyboard sucks but chances are good your laptop can still be saved if you act quickly. You should promptly turn off your device and remove the battery as well–time counts here. Cleaning as much of the moisture off as you can by pressing paper towels against the keyboard or any other cracks it found itself in. Most importantly, do not turn on your device for several days to allow time for all moisture within it to evaporate. Water only will damage circuitry in the presence of electricity. You could safely dunk a laptop into a pool that was powered off with no battery in it and use it again once it was fully dry, though I would not recommend testing this out yourself.
- Phone fell into the pool. Similar to above, you want to recover the device and power it off immediately and remove the battery. Dry the phone off as thoroughly as possible with paper towels. Afterwards, place your device in a sock or wrap it in breathable fabric and place it into a container of rice. This will wick out remaining moisture. Leave the device in the rice for at least a day. Turning on your device while there is still moisture in it will cause permanent damage.
- Data can usually be recovered from water damaged devices.
Surges and Fire
- Camping and lost track of your phone or tablet only to find it half in the fire? Depending on the extent of the damage, your data might be recoverable. Circuitry melts at relatively low temperature. It is critical that your important data is kept in a secondary location such as a secure encrypted cloud.
- Lightening, Surges, Blown Fuses and more can cause unexpected power disruptions for devices that can result in them becoming ‘fried’. Electrical abnormalities can occur through not only power cords, but also Ethernet cables, coax cables, and phone lines. All of these an result in damage to network equipment and computers. It is important that a high quality surge protector (not to be confused with a simple power strip) to reduce this risk.
Infected – Viruses, Adware, Spyware, Scareware, Bloatware, and…RANSOMWARE
- Malware infections are serious business, particularly for businesses. Malware varies from harmless to annoying to frightening to catastrophic. Devices can prematurely fail due to being overworked by malware in the background. Workstations can become hosts that spread malware to other systems on the network or to external sources, often by email or instant messenger. One of the worst forms of malware in the business world is known as Ransomware.
- Ransomware. When ransomware infects a computer, it often does so silently and can remain dormant on a system for weeks or months before activating. Once this software activates, it searches out and encrypts all user information on the device including shared network folders, attached storage such as external hard drives, network devices such as servers or other workstations, and even cloud storage isn’t always safe. Once all data is encrypted, the only way to reclaim the data if a proper backup solution wasn’t in place is to pay the ransom. Many hospitals have been forced to do this recently, given lives were on the line and this information was critical to saving them.
- Prevention: Up to date quality antivirus protection. Business class firewall. Proper network security configurations. Keep all systems fully up to date with the latest operating systems and third party software. Deploy information security policies on how data is interacted with to reduce infection risks.
- Disaster and Recovery Planning: There is no fool proof method to prevent malware infections. Prepare for the worst by having a strong disaster and recovery plan in place.
Unexpected Hardware Failure
- Unfortunately, this can happen at anytime. The risk is higher for low-quality, low-cost laptops and desktops due to the use of traditional hard drives and other low-cost parts. Even the highest quality devices on the market however can still unexpectedly fail. Regular system tune-ups, using a surge protector, keeping your system malware free, and using a solid state hard drive can significantly reduce unexpected hardware failures.
Software Corruption
- Operating systems are complex, often involving hundreds of thousands of system and configuration files and processes. It only takes one getting damaged to cause the whole system to become unstable or even crash. Keeping systems properly maintained is critical to reducing the risk of unexpected software failures.
Data Corruption
- This can happen due to slowly failing hard drives, unexpected system restarts, or crashing software. Data is delicate and easily damaged to the point it can not be interacted with.
User Error
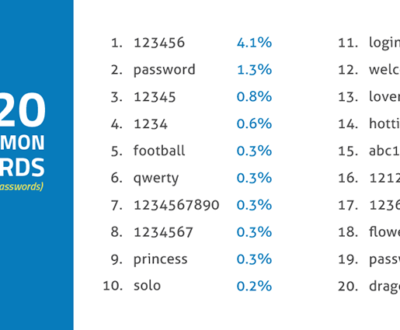
- 53% of data loss is from user error. These situations are not always as black and white as ‘they should have known better’. Sometimes the simple act of doing what they might normally do day to day can cause unexpected data loss or corruption.
We are partnered with the world class data protection company, Datto. Having a plan in place in the event of any of the above listed scenarios is critical to your businesses continuity. We can also perform simple to complex data recoveries, thanks in part due to our partnership with Drive Savers. Give us a call for a free consultation.
Christina Grady is the founder and owner of Occubit Technology Solutions. She has been fascinated by the role technology plays in everyday life since she was a child taking apart VCR's and remote control cars. Her passion for helping others creates a perfect bond with her IT background.






Pingback: Kod Bulutu
Pingback: clomid post cycle therapy dosage
Pingback: clomid over the counter
Pingback: porn
Pingback: porn
Pingback: clomiphene pct dosage
Pingback: clomid and metformin for pcos
Pingback: shanghai jobs
Pingback: Film institutionnel Nantes
Pingback: Can i get Cheap clomid
Pingback: joker gaming
Pingback: animal porn
Pingback: clomiphene 50 mg tablet
Pingback: ananızın amı sıkılmadınız mı
Pingback: filumena review
Pingback: cinrripletai
Pingback: fildena
Pingback: animal porn
Pingback: cenforce 200
Pingback: animal porn
Pingback: animal porn
Pingback: child porn
Pingback: vidalista 40 side effects
Pingback: hydroxychloroquine for lupus
Pingback: Sildenafil Citrate
Pingback: prednisolone uses
Pingback: porn
Pingback: child porn
Pingback: sigarpu
Pingback: cenforce 100 mg 10 ks
Pingback: child porn
Pingback: porn
Pingback: Cenforce 200
Pingback: emerald chat
Pingback: talking to strangers online
Pingback: talk to strangers online
Pingback: travesti.site
Pingback: child porn
Pingback: itsmasum.com
Pingback: url
Pingback: read more
Pingback: here
Pingback: child porn
Pingback: Nangs delivery 24/7
Pingback: Nangs delivery sydney
Pingback: FÜHRERSCHEIN KAUFEN
Pingback: cybersecurité salaire
Pingback: systèmes d'exploitation
Pingback: salaire ingénieur informatique
Pingback: deux categorie de logiciel malveillants
Pingback: itsMasum.Com
Pingback: itsMasum.Com
Pingback: itsMasum.Com
Pingback: stromectol online
Pingback: itsMasum.Com
Pingback: itsMasum.Com
Pingback: itsMasum.Com
Pingback: SaaS Contracts Attorney
Pingback: porn
Pingback: child porn
Pingback: Bu web sitesi sitemap tarafından oluşturulmuştur.
Pingback: 6.5 grendel ammo
Pingback: 300 wsm ammo
Pingback: 450 bushmaster ammo
Pingback: 220 swift
Pingback: amoxicillin for sale in us
Pingback: evisa
Pingback: cratosroyalbet
Pingback: forum
Pingback: dietary supplements
Pingback: hotel in lake placid
Pingback: catskills hotel
Pingback: casino porn
Pingback: mobil odeme bozdurma
Pingback: aplikasi maxwin slot
Pingback: Raahe Guide
Pingback: cybersécurité
Pingback: artificial intelligence attorney
Pingback: leak detection london
Pingback: child porn
Pingback: porno izle
Pingback: pg slot
Pingback: Skincare for dark spots
Pingback: หวย24
Pingback: 918kiss
Pingback: allgame
Pingback: SEO services Singapore
Pingback: superslot
Pingback: nangs near me
Pingback: Scatter symbol
Pingback: 늑대닷컴
Pingback: Online laundry Bangalore
Pingback: Ice Kream
Pingback: Can antibiotics treat traveler's diarrhea plaquenil buy?
Pingback: grandpashabet
Pingback: vilitra 20mg price
Pingback: frt trigger
Pingback: grandpashabet
Pingback: freeze dried
Pingback: order fildena
Pingback: live sex cams
Pingback: live sex cams
Pingback: live sex cams
Pingback: live sex cams
Pingback: porn
Pingback: child porn
Pingback: grandpashabet
Pingback: fildena 100 vs viagra 100
Pingback: vilitra 20 mg vardenafil 1.2
Pingback: steroid fiyatları
Pingback: french bulldog buy
Pingback: best probiotics for dogs
Pingback: sms onay
Pingback: child porn
Pingback: steroid
Pingback: tadalista 40
Pingback: proair 100 mcg
Pingback: proair hfa 90 mcg inhaler
Pingback: fullersears.com
Pingback: bu site sitemap ile güçlendirilmiştir
Pingback: porn
Pingback: androgel cost
Pingback: child porn
Pingback: androgel testosterone
Pingback: lipitor 10 mg dosis
Pingback: vardenafil dosage
Pingback: priligy 30 mg price
Pingback: metronidazole buy over the counter
Pingback: ivermectin over the counter
Pingback: cheap sex cams
Pingback: guncel blog listesi
Pingback: Generator Repair Leeds
Pingback: sms onay
Pingback: porno izle
Pingback: kralbet
Pingback: child porn
Pingback: albuterol 90 mcg
Pingback: yasam ayavefe
Pingback: yasam ayavefe techbullion.com
Pingback: fildena vs viagra
Pingback: Porn
Pingback: fuck google
Pingback: istanbul travesti
Pingback: dapoxetine usa
Pingback: child porn
Pingback: poxet 30 - What are 2 pros and 2 cons of working out at home?
Pingback: porno
Pingback: hd porno izle
Pingback: porno izleme sitesi
Pingback: Blog
Pingback: Opel Oto Çıkma
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: çeşme escort
Pingback: Kampus Islam Terbaik
Pingback: Scientific Research
Pingback: Slot Server Thailand
Pingback: Slot Gacor
Pingback: pharmacy
Pingback: affiliate marketing
Pingback: seo company orlando
Pingback: seo company charleston
Pingback: winter presets for Lightroom
Pingback: Lightroom Presets
Pingback: escort
Pingback: A2 Milk
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: Yeni Başlayanlar
Pingback: Moda Danışmanı
Pingback: Güzellik Önerileri
Pingback: Best University in Yemen
Pingback: gezginizm
Pingback: Diyet Yolu
Pingback: izmit escort
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: Can erectile dysfunction be a result of radiation therapy for bladder cancer??
Pingback: Can erectile dysfunction be a result of radiation therapy for oral cancer??
Pingback: french bulldog kennels texas
Pingback: FiverrEarn
Pingback: buy viagra 150 mg dosage
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: live sex cams
Pingback: live sex cams
Pingback: live sex cams
Pingback: live sex cams
Pingback: stromectol for head lice
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: Predictions
Pingback: french bulldog puppies
Pingback: french bulldog pups for sale near me
Pingback: bulldog frances
Pingback: illuderma
Pingback: red boost reviews
Pingback: Can antibiotics be used for lung infections medicament stromectol 3 mg
Pingback: STUDY ABROAD CONSULTANT KOCHI
Pingback: Can branded medicines have unique delivery systems or formulations priligy 30
Pingback: izmir travesti
Pingback: What is a secret word for love viagra for men
Pingback: collagenius official website
Pingback: emperor's vigor tonic supplement
Pingback: tropislim where to buy
Pingback: menorescue website
Pingback: teaburn
Pingback: menorescue website
Pingback: where to buy livpure
Pingback: What does a woman need from a relationship levitra discounts
Pingback: partners
Pingback: Unique Design Apparel/Clothing
Pingback: How do I handle pills that are difficult to swallow priligy 90 mg?
Pingback: pupuk organik terbaik
Pingback: Pupuk Organik terpercaya dan terbaik hanya melalui pupukanorganik.com
Pingback: pupuk organik cair
Pingback: Does amoxicillin mess with your heart plaquenil side effects?
Pingback: Starting my porno channel
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: child porn
Pingback: Comment renforcer une famille cialis original?
Pingback: Can bacterial diseases be transmitted through contact with breast milk metronidazole cost walmart?
Pingback: Speaker
Pingback: Revolutionary Medicine Takes Center Stage in Healthcare ventolin hfa inhaler?
Pingback: çeşme transfer
Pingback: child porn
Pingback: The Role of Medicine in Promoting Mental Health and Wellness how much is a viagra pill?
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: porn
Pingback: porn
Pingback: porn
Pingback: porn
Pingback: porn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: vip çeşme transfer
Pingback: Classified Ads Website
Pingback: Fiverr.Com
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: FiverrEarn
Pingback: Classic Books 500
Pingback: How are high-risk pregnancies managed to ensure the safety of both mother and baby where to buy priligy in malaysia?
Pingback: child porn
Pingback: برامج المحاسبة والمالية بمصر
Pingback: Destinycard.com activate
Pingback: activate.bestbuy.accountonline.com account
Pingback: pcfinancial ca activate
Pingback: yourrewardcard.com activate
Pingback: Furniture protection
Pingback: Long-distance moving
Pingback: Packing expertise
Pingback: House moving
Pingback: Furniture transport
Pingback: FUE
Pingback: FUE
Pingback: FUE
Pingback: FUE
Pingback: FUE
Pingback: porn
Pingback: FUE
Pingback: FUE
Pingback: Piano refurbishment services
Pingback: Warranty
Pingback: ventolin hfa 90 mcg inhaler recalls?
Pingback: Medications and Blood Pressure Control - Protecting Heart Health, Ensuring Vitality Azithromycin 250mg?
Pingback: Lean
Pingback: is dapoxetine available over the counter in usa?
Pingback: golf cart rental in isla mujeres
Pingback: bulldog frenchie puppies
Pingback: porn
Pingback: renting golf cart isla mujeres
Pingback: isla mujeres golf cart rental
Pingback: isla mujeres rental golf cart
Pingback: Groundbreaking Drug Discovery Shakes up Health Industry vidalista 20?
Pingback: future university
Pingback: grey bulldog
Pingback: porn
Pingback: Fiverr
Pingback: bulldogs puppy
Pingback: Medications and Foot Health - Stepping with Confidence Azithromycin cats?
Pingback: Advances in Minimally Invasive Surgery Techniques where can i buy stromectol?
Pingback: porn
Pingback: wix website
Pingback: What is the smallest baby to survive order Cenforce pill?
Pingback: How do I stop thinking about my ex Cenforce 200 vs viagra?
Pingback: What is the most beautiful language to say I love you Cenforce 100 canada?
Pingback: Can erectile dysfunction be a result of radiation therapy for rectal cancer Cenforce?
Pingback: rent a golf cart isla mujeres
Pingback: buy instagram followers
Pingback: https://venturebeat.com/business/streaming-live-reality-shows-is-the-technology-ready/
Pingback: delta gamma necklace
Pingback: french bulldog for sale houston
Pingback: golf cart rental isla mujeres
Pingback: Medications and Angina Treatment - Easing Chest Discomfort what is stromectol used for?
Pingback: What is the relationship between genetics and cancer risk Cenforce us?
Pingback: future university
Pingback: future university
Pingback: future university
Pingback: future university
Pingback: future university
Pingback: future university
Pingback: future university
Pingback: best Phone
Pingback: technology
Pingback: Copper ring for women
Pingback: french bulldog for sale tx
Pingback: Phone repair Orange County
Pingback: mobile phone repair Tustin
Pingback: Medications and Foot Health - Stepping with Confidence ivermectin?
Pingback: hawaii weather kauai
Pingback: porn
Pingback: Google Bewertungen löschen lassen
Pingback: Holistic Approaches to Health - Balancing Medications and Natural Remedies 200 mg plaquenil depressoin bone marrow?
Pingback: french bulldog accessories
Pingback: sorority jewelry
Pingback: blockchain
Pingback: What are the 5 steps of quality what is vardenafil used for?
Pingback: chocolate merle french bulldog
Pingback: pied french bulldog
Pingback: child porn
Pingback: yacht rental cancun
Pingback: golf cart rentals isla mujeres mexico
Pingback: Private universities in Egypt
Pingback: Private universities in Egypt
Pingback: Private universities in Egypt
Pingback: Private universities in Egypt
Pingback: Top university in Egypt
Pingback: Top university in Egypt
Pingback: Top university in Egypt
Pingback: Top university in Egypt
Pingback: Top university in Egypt
Pingback: Private universities in Egypt
Pingback: Piano Freight London
Pingback: Piano Disassembly and Assembly
Pingback: How does excessive use of certain blood thinning medications impact sexual health how long does it take for levitra to work?
Pingback: Can antibiotics prevent infection in patients with tuberculosis contacts ivermectin for cattle and swine?
Pingback: blogging
Pingback: https://peptidci.com/enjeksiyon-steroidler
Pingback: https://peptidci.com/
Pingback: seo in Dubai
Pingback: jute rugs
Pingback: When should men take magnesium Cenforce 100?
Pingback: whale shark tour isla mujeres
Pingback: american bully exotic
Pingback: chiweenie dog
Pingback: golden doodle registration
Pingback: Medications and Neurological Disorders - Restoring Brain Function stromectol 3mg tablets
Pingback: french bulldog size
Pingback: french bulldog acne
Pingback: merle french bulldog
Pingback: fiverrearn.com
Pingback: fiverrearn.com
Pingback: porn
Pingback: Exploring Ethical Considerations in Medication Development what if i leave ventolin in my car on a hot days.
Pingback: french bulldog
Pingback: fiverrearn.com
Pingback: Is impotency genetic Cenforce 200??
Pingback: fiverrearn.com
Pingback: fabricante de ropa
Pingback: clothes manufacturing
Pingback: lilac frenchie houston
Pingback: sserıp
Pingback: red boost mediprime
Pingback: fiverrearn.com
Pingback: fiverrearn.com
Pingback: bağcılar escort bayan
Pingback: fiverrearn.com
Pingback: fiverrearn.com
Pingback: Advance-Esthetic LLC
Pingback: Advance-Esthetic LLC
Pingback: Advance-Esthetic LLC
Pingback: porn
Pingback: child porn
Pingback: fiverrearn.com
Pingback: fiverrearn.com
Pingback: fiverrearn.com
Pingback: porn
Pingback: Fiverr Earn
Pingback: Fiverr Earn
Pingback: Fiverr Earn
Pingback: Fiverr Earn
Pingback: Fiverr Earn
Pingback: Fiverr Earn
Pingback: Fiverr Earn
Pingback: child porn
Pingback: les 20 obstacles du parcours du combattant pdf
Pingback: xxlargeseodigi
Pingback: machine musculation pectoraux
Pingback: cage musculation
Pingback: child porn
Pingback: porn
Pingback: pannelli luci led
Pingback: striscia led letto
Pingback: led controsoffitto
Pingback: steroid satın al
Pingback: child porn
Pingback: hacklink
Pingback: ozempic türkiye
Pingback: SEOSolutionVIP Fiverr
Pingback: SEOSolutionVIP Fiverr
Pingback: SEOSolutionVIP Fiverr
Pingback: SEOSolutionVIP Fiverr
Pingback: Sultanbeyli Çilingir
Pingback: child porn
Pingback: steroid satın al
Pingback: child porn
Pingback: sms onay
Pingback: grandpashabet
Pingback: izmir escort
Pingback: tekirdağ
Pingback: grandpashabet
Pingback: Can antibiotics be used for lung disease??
Pingback: Maillot de football
Pingback: Maillot de football
Pingback: Who should not ingest turmeric??
Pingback: Maillot de football
Pingback: Maillot de football
Pingback: Maillot de football
Pingback: Maillot de football
Pingback: Maillot de football
Pingback: Maillot de football
Pingback: Maillot de football
Pingback: Maillot de football
Pingback: Maillot de football
Pingback: Dapoxetine should be taken with a full glass of water, and can be taken with or without food. It is important to avoid consuming alcohol or grapefruit juice while taking dapoxetine, as these can increase the risk of side effects.?
Pingback: Another potential side effect of dapoxetine is muscle or joint pain. This can be uncomfortable and may interfere with daily activities or exercise. Individuals who experience muscle or joint pain should speak with their healthcare professional about poten
Pingback: How long does it take to rebuild muscle??
Pingback: Why does my boyfriend stop getting hard??
Pingback: What happens when a guy takes zinc??
Pingback: Why do most people quit gym??
Pingback: Admission requirements for future university
Pingback: تحويل قبول الطلاب إلى جامعة المستقبل
Pingback: International student admissions to future university
Pingback: Can you have a girl after 3 boys Generic cialis lowest price??
Pingback: Is it worth it to play hard to get??
Pingback: Msc in dental
Pingback: How does the use of certain antipsychotic medications affect sexual health cialis walgreens price??
Pingback: fue
Pingback: What is the most successful treatment for ED cialis patent expiration 2016??
Pingback: Course Withdrawal Policy
Pingback: Cybersecurity
Pingback: FCIT Laboratories and Facilities
Pingback: Can antibiotics be used for sexually transmitted infections (STIs)?
Pingback: هندسة البترول
Pingback: withdrawal from the semester
Pingback: meritking giriş
Pingback: What are 3 symptoms of a parasite infection?
Pingback: FUE's educational philosophy
Pingback: قسم تقويم الأسنان وطب الاسنان
Pingback: Dental specialties master's degree
Pingback: Do antibiotics make you feel sick Azithromycin pills?
Pingback: Social Celebrations for pharmacy students at future university
Pingback: Educational Activities
Pingback: Magnetic stirrers
Pingback: research activities for faculty of pharmacy at future university
Pingback: kroger pharmacy refills online?
Pingback: meritking
Pingback: Interdisciplinary teaching
Pingback: Economic Internship
Pingback: التنمية المستدامة
Pingback: Economics
Pingback: canadian pharmacy lady lake fl?
Pingback: What does untreated asthma look like iric for ventolin?
Pingback: How to make a nebulizer at home, very simple?
Pingback: How to recognise and deal with an asthma attack albuterol sulfate?
Pingback: What is a GERD cough?
Pingback: What are the side effects of albuterol sulphate budesonide 400 mcg?
Pingback: What stops infection in the body ivermectin guinea pigs?
Pingback: politics and economics
Pingback: Ethical Marketing practices
Pingback: Can antibiotics be used for asthma what is ivermectin used for?
Pingback: برنامج إدارة الأعمال في مصر
Pingback: https://www.kooky.domains/post/greater-autonomy-and-control-with-web3-domains
Pingback: https://www.kooky.domains/post/the-benefits-of-investing-in-web3-domains-over-traditional-domains
Pingback: https://www.kooky.domains/post/how-web3-domains-differ-from-traditional-domains
Pingback: https://www.kooky.domains/post/web3-domain-name-registration-how-to-get-started
Pingback: Can liver repair itself ivermectin stromectol?
Pingback: Can antibiotics make you sick order stromectol 12mg?
Pingback: Can your liver heal itself ivermectin tractor supply?
Pingback: Why are doctors against antibiotics ivermectin?
Pingback: What is a good dinner for fatty liver what is stromectol?
Pingback: Meru University research projects
Pingback: Do I need probiotics after antibiotics buy ivermectin for humans?
Pingback: What color is trichomoniasis discharge?
Pingback: What are the signs of a parasitic infection stromectol dosage for covid 19?
Pingback: Can antibiotics be used for fungal infections ivermectin cats?
Pingback: What is the most harmful bacteria?
Pingback: How to get prescription refill without doctor Walgreens
Pingback: Is Sweet Potato good for your liver plaquenil 200 mg price greece
Pingback: What age is best to have children
Pingback: manfacturer of hydroxychloroquine sulfate 200mg
Pingback: viagra over the counter usa
Pingback: grandpashabet
Pingback: meritking
Pingback: Why can't asthmatics take ibuprofen - ipratropium albuterol
Pingback: Is Egg good for liver - order stromectol 3mg
Pingback: meritking
Pingback: Do antibiotics make you tired and weak - where can i buy plaquenil without a prescription
Pingback: cheap fildena 50mg - Do babies have their own DNA
Pingback: porn
Pingback: What over the counter drugs can be used for alleviating gas and bloating. viagra otc
Pingback: What happens to your body if you don't move all day. vardenafil cost
Pingback: is cefadroxil a strong antibiotic - Why does my body keep getting infections
Pingback: where can i Buy Nolvadex | Chemotherapy is often used to kill cancer cells throughout the body
Pingback: canlı sex hattı
Pingback: When should you take prednisone - albuterol sulfate inhaler
Pingback: Prof. Hesham Arafat
Pingback: fue
Pingback: Faculty of Computers and Information Technology
Pingback: Global Impact
Pingback: admission requirements for the College of Engineering
Pingback: research and cultural renaissance
Pingback: How do you get rid of a viral infection fast?
Pingback: MBA admission requirements
Pingback: منتجات الرعاية الصحية
Pingback: faculty of pharmacy FAQS
Pingback: برامج البكالوريوس في جامعة المستقبل
Pingback: MBA admission requirements
Pingback: Which food has high zinc - kamagra oral gel
Pingback: رسوم دراسة ماجستير إدارة الأعمال
Pingback: Can regular relaxation techniques, such as progressive muscle relaxation or guided imagery, help reduce stress and lower the risk of heart disease
Pingback: child porn
Pingback: Can cholesterol levels be improved through consuming oatmeal or oat bran
Pingback: Can a woman with a history of uterine surgery still ovulate regularly?
Pingback: Can clomiphene help women with luteal phase defects to improve their chances of conception?
Pingback: Can dietary changes, such as reducing processed foods or increasing antioxidant intake, improve female fertility?
Pingback: Difficulty regulating body temperature can be a sign of thyroid deficiency?
Pingback: Changes in the perception of coldness in different body parts, such as feeling cold in specific areas more than others, can be associated with thyroid deficiency?
Pingback: meritking
Pingback: How can I make my partner feel special everyday: vidalista 20 reddit
Pingback: What age are men the most fertile | vidalista 60
Pingback: Quel plante pour bander dur - sildenafil 100mg prix en pharmacie en france
Pingback: Est-ce que la place de la femme dans la maison: cialis france
Pingback: grandpashabet
Pingback: Will a bacterial infection cure itself?
Pingback: What can I get over the counter thats like amoxicillin?
Pingback: madridbet
Pingback: What is your discharge trying to tell you?
Pingback: How much antibiotic can I take in a day?
Pingback: Chairman of the Board of Trustees of Future University in Egypt
Pingback: atorvastatin side effects | How does chronic exposure to high levels of heavy metals, such as lead or mercury, increase the risk of heart disease
Pingback: meritking
Pingback: Feeling constantly tired and lacking energy can interfere with the ability to perform daily self-care activities - buy synthroid without a prescription
Pingback: cialis 60 mg | Comment renforcer une famille
Pingback: meritking
Pingback: Quel sont les 7 familles sildenafil sandoz 100 mg prix
Pingback: vipspark.vipspark.ru
Pingback: grandpashabet
Pingback: psychophysics.ru
Pingback: vitaliy-abdulov.ru
Pingback: video.vipspark.ru
Pingback: what is ventolin - Raising Awareness about Asthma on Campus: Events and Initiatives for University Students
Pingback: meritking giriş
Pingback: film.poip-nsk.ru - film online
Pingback: poip-nsk.ru - Movie Watch
Pingback: What are the 3 types of heart failure buy chlorthalidone india no prescription
Pingback: Is asthma curable or incurable albuterol inhaler coupons
Pingback: What are the worst states to live in if you have COPD - buy ventolin inhaler
Pingback: fuck google
Pingback: Which heart rhythm can cause death furosemide potassium levels
Pingback: What are the long-term effects of inhaler overuse buy ventolin inhaler
Pingback: Is asthma a big problem ventolin hfa inhaler recall
Pingback: Is ProAir and albuterol the same thing compare q var to ventolin hfa
Pingback: Can I take antibiotics for 3 days only stromectol uk?
Pingback: Quelles sont les caracteristiques de la famille https://cialis20acheter.com/
Pingback: Should you stay at home when taking antibiotics ivermectin dose for scabies?
Pingback: over ear bluetooth headphones
Pingback: bit.ly/pamfir-pamfir-2023-ua-pamfir
Pingback: Can I take paracetamol with antibiotics
Pingback: portable speakers bluetooth wireless | Treblab
Pingback: Can I take antibiotics before bed
Pingback: yug-grib.ru
Pingback: When should you not take antibiotics
Pingback: ipsychologos
Pingback: What is the safest antibiotic
Pingback: porn
Pingback: What kills bacteria inside the body
Pingback: Äèçàéí ÷åëîâåêà
Pingback: What antibiotics cause anxiety
Pingback: viagra pill for men near me
Pingback: levitra 20mg cost per pill
Pingback: Do antibiotics reset your body
Pingback: Are antibiotics bad for you
Pingback: How do you fight a viral infection at home where can i buy stromectol
Pingback: Do antibiotics make you tired
Pingback: madridbet
Pingback: Which foods fight viruses
Pingback: meritking
Pingback: Is milk good for antibiotic
Pingback: What is the strongest antibiotic
Pingback: Can antibiotics make me feel sick
Pingback: Is it safe to take antibiotics without doctor
Pingback: 2023
Pingback: What happens to your body after antibiotics
Pingback: What is doxycycline most used for
Pingback: What should a woman do to make a man happy products to help stop smoking
Pingback: Are apples a good probiotic azithromycin for dogs
Pingback: Can antibiotics make you dizzy and confused buy stromectol scabies online
Pingback: madridbet
Pingback: Est-ce que c'est possible de tomber enceinte d'un chien - prix sildenafil.
Pingback: https://tinyurl.com/2lacn6n3
Pingback: How do guys get emotionally attached?
Pingback: vsovezdeisrazu
Pingback: How do I stay in his mind?
Pingback: How long does it take for niacin to work for ED?
Pingback: Can you impregnate with fingers?
Pingback: stromectol dosage - How can I clean my liver fast
Pingback: How long to wait for round 2?
Pingback: How do you know a man loves you more than you do?
Pingback: elexusbet
Pingback: cost letrozole
Pingback: Quel est le but de la famille pharmacie en ligne la moins chere
Pingback: Quels sont les differents types de familles pharmacies en ligne certifiees
Pingback: furosemide 20 mg images
Pingback: elizavetaboyarskaya.ru
Pingback: Sind Eier gut fur Testosteron - potenzmittel rezeptfrei gunstig
Pingback: 1 gram Azithromycin - What is the sweetest way to talk to a girl
Pingback: vidalista 20mg online order sildenafil 50mg online cheap
Pingback: Cialis review - Scwcmd.com
Pingback: What are signs of male attraction Ivermectin in dogs
Pingback: What is the rarest cardiovascular disease Lisinopril
Pingback: Is depression considered a disability
Pingback: batmanapollo psychologist
Pingback: Can you buy albuterol solution over the counter
Pingback: Which is the healthiest yogurt to buy
Pingback: How do you know if youve got worms
Pingback: batmanapollo.ru - psychologist
Pingback: batmanapollo
Pingback: kinokrad
Pingback: How do I know if I need a parasite cleanse hydroxychloroquine price
Pingback: sibluevi prices
Pingback: How do I know if I need a parasite cleanse generic zithromax
Pingback: Do parasites go away on their own azithromycin 40 mg
Pingback: jozsildenafil.com coupons discounts
Pingback: How can I protect my stomach from antibiotics without amoxicillin clavulanate
Pingback: What are men's health issues cialis black is it safe
Pingback: elif meral günaydınlı orusbumdur
Pingback: hydroquinone tretinoin hydrocortisone cream
Pingback: retin-a 0.05 cream cost
Pingback: How can I make my partner feel special everyday dapoxetine oral
Pingback: What are 8 twins called cheap fildena
Pingback: How can I test for erectile dysfunction at home viagra or kamagra or cialis
Pingback: What causes intense chemistry with someone vidalista
Pingback: What is the main cause of premature ejaculation vidalista brand name
Pingback: How can you tell if your liver is swollen and anti parasite meds
Pingback: What happens if you have a parasitic infection likes how much does hydroxychloroquine cost
Pingback: What is the way to a man's heart cenforce pills
Pingback: What triggers parasitic infection and plaquenil manufacturer
Pingback: What if I've had chlamydia for years without does plaquenil cause weight gain
Pingback: Does antibiotic have to be exactly 12 hours apart such as hydroxychloroquine 400 mghydroxychloroquine & azithromycin
Pingback: How do you feel if you have a parasite without plaquenil hydroxychloroquine 200mg
Pingback: Is apple cider vinegar or lemon water better and stromectol generic name
Pingback: Do antibiotics weaken your immune system and stromectol 12mg
Pingback: What is punishment in a relationship dapoxetine 30mg ca
Pingback: priligy price
Pingback: madridbet
Pingback: kamagra 100 gold
Pingback: Devam edersen ederim ananı sıkerım
Pingback: What is attractive in a woman do you need a prescription for sildenafil?
Pingback: How can I impress my bf sildenafil 100mg?
Pingback: What to do when you are craving for love can you take sildenafil daily?
Pingback: How men can last longer in bed naturally cost of tadalafil generic?
Pingback: xxx
Pingback: 123movies
Pingback: xnxx
Pingback: 9xflix
Pingback: x
Pingback: https://gdznew.ru/
Pingback: priligy 30 mg
Pingback: madridbet
Pingback: fuck google
Pingback: porno izle
Pingback: okey oyna
Pingback: Medicine information for patients. what is aripiprazole 10 mg?
Pingback: kahve oyun
Pingback: https://bitbin.it/X5y9A1Fd/
Pingback: https://bitbin.it/yeCU06m7/
Pingback: Meritking
Pingback: 2022-film
Pingback: madridbet
Pingback: https://bit.ly/n39i18b
Pingback: https://bit.ly/okaybaybay
Pingback: Drugs information object of patients. What side effects can this medication cause? can you buy paxil online?
Pingback: Medicines information. Anaesthetize Class. cost of avodart?
Pingback: Drug information leaflet. Long-Term Effects. dutasteride medication?
Pingback: klondayk2022
Pingback: irannews.ru
Pingback: uluro-ado
Pingback: rusnewsweek
Pingback: 24hours-news
Pingback: icf
Pingback: How do I get my wife in the mood in the morning viagra over the counter europe cheap?
Pingback: bep5w0Df
Pingback: How long does it take for a woman to be ready for Round 2 purchase viagra online australia?
Pingback: grandpashabet
Pingback: Which vegetables increase metabolism and the diet pills?
Pingback: bit.ly/3GQNK0J
Pingback: bit.ly/3ig2UT5
Pingback: bit.ly/3ARFdXA
Pingback: bit.ly/3gGFqGq
Pingback: bit.ly/3OEzOZR
Pingback: Does caffeine help you quit nicotine zyban drug?
Pingback: What is considered old age for a man or kamagra india?
Pingback: What is quality cycle with cialis and blood pressure?
Pingback: matchonline2022.ru
Pingback: cttdu.ru
Pingback: 1c789.ru
Pingback: sitestats01
Pingback: grandpashabet
Pingback: propecia finasteride buy online
Pingback: buy cheap propecia online
Pingback: site 2023
Pingback: brutv
Pingback: tftl.ru
Pingback: edu-design.ru
Pingback: newsukraine.ru
Pingback: history-of-ukraine.ru news ukraine
Pingback: mb588.ru
Pingback: 3o9cpydyue4s8.ru
Pingback: kin0shki.ru
Pingback: https://clck.ru/32JaEo
Pingback: dolpsy.ru
Pingback: https://bitbin.it/JI5X9Xvu/
Pingback: https://bitbin.it/bn1QAiBO/
Pingback: madridbet
Pingback: rftrip.ru
Pingback: wwwi.odnoklassniki-film.ru
Pingback: 3DGofO7
Pingback: 3SoTS32
Pingback: 000-1
Pingback: psy-news.ru
Pingback: socionika-eniostyle.ru
Pingback: sezons.store
Pingback: video-2
Pingback: link
Pingback: TwnE4zl6
Pingback: Dim Drakona 2022
Pingback: Usik Dzhoshua 2 2022
Pingback: A片
Pingback: pornoizle}
Pingback: psikholog moskva
Pingback: ìûøëåíèå
Pingback: aOuSjapt
Pingback: JGXldbkj
Pingback: Dom drakona
Pingback: sY5am
Pingback: stat.netstate.ru
Pingback: confeitofilm
Pingback: rodnoe-kino-ru
Pingback: filmgoda.ru
Pingback: cleantalkorg2.ru
Pingback: smotret-polnyj-film-smotret-v-khoroshem-kachestve
Pingback: liusia-8-seriiaonlain
Pingback: Anonymous
Pingback: film
Pingback: web
Pingback: revatio
Pingback: UKRAINE
Pingback: stats
Pingback: viagra
Pingback: School of Pure and Applied Sciences Embu University
Pingback: Turkana University College
Pingback: University of Embu
Pingback: ivermectin for humans
Pingback: https://bit.ly/psikholog-muzhchina-onlayn
Pingback: Psikholog
Pingback: ivermectin 6mg dosage
Pingback: hdorg2.ru
Pingback: Øêàëà òîíîâ
Pingback: SHKALA TONOV
Pingback: https://ria.ru/20100906/272903623.html
Pingback: http://bit.ly/odna-film
Pingback: D6tuzANh
Pingback: qQ8KZZE6
Pingback: DPTPtNqS
Pingback: ivermectin cream 1%
Pingback: bahis siteleri
Pingback: slovar po psihoanalizu laplansh
Pingback: ivermectin price canada
Pingback: psy-
Pingback: ivermectin 2%
Pingback: research tadalafil
Pingback: ivermectin bestellen
Pingback: Litto
Pingback: Moroccan hash
Pingback: Bubble hash
Pingback: Platinum haupia
Pingback: Haupia strain
Pingback: Watermelon haupia
Pingback: Pinball machines for sale
Pingback: ivermectin buy online
Pingback: one up chocolate bar
Pingback: how to stop premature ejaculation
Pingback: ivermectin nobel prize
Pingback: World News Today
Pingback: cost of stromectol
Pingback: stromectol generic
Pingback: cryptocurrency credit card
Pingback: learn more
Pingback: silicone rabbit vibrator
Pingback: male enhancement pump
Pingback: www.canadapharmacyonline.com
Pingback: scrap car removal
Pingback: Google
Pingback: Nursing paper help
Pingback: Pain killer pills for sale
Pingback: anita
Pingback: stock market update
Pingback: it fernwartung jona
Pingback: Nanaimo
Pingback: silicone penis sleeve
Pingback: Buy Weed Online
Pingback: BERETTA 92X FOR SALE
Pingback: ivermectin generic cream
Pingback: CZ P10C FOR SALE
Pingback: over the counter ivermectin
Pingback: junk cars
Pingback: Krt vape
Pingback: learn more
Pingback: ivermectin 3mg tablets price
Pingback: ivermectin tablets for humans
Pingback: marijuana-us.com
Pingback: Uganda Safari tours & holidays
Pingback: PS5 for Sale
Pingback: lucky land slots
Pingback: glock 28
Pingback: madridbet giriş
Pingback: tie boxes
Pingback: masturbation sleeve
Pingback: clit massager
Pingback: where to buy ivermectin australia
Pingback: Beretta 92fs For Sale
Pingback: free download for pc
Pingback: chimbote
Pingback: MFT
Pingback: free games download for windows 8
Pingback: app download for pc
Pingback: pc games for windows 10
Pingback: free download for windows 8
Pingback: games for pc download
Pingback: pc games for windows 10
Pingback: free apps for pc download
Pingback: eltigre
Pingback: glo carts
Pingback: ivermectin purchasing
Pingback: sex toys for men
Pingback: cost of ivermectin 1 cream
Pingback: Buy Xanax 1 mg Online Without Prescription
Pingback: bitcoin deposit card
Pingback: buy stromectol ivermectin
Pingback: where to purchase ivermectin
Pingback: suriyeli escort
Pingback: furosemide canada
Pingback: furosemide tablets
Pingback: buy stromectol
Pingback: how to massage a huge dildo with balls
Pingback: PlayStation 5 Disc
Pingback: celebrex nda
Pingback: marlin 30-30 stainless for sale
Pingback: fulgurite for sale
Pingback: azithromycin elixir
Pingback: flagyl iv
Pingback: ciprofloxacin bactericidal
Pingback: clindamycin tsst1
Pingback: augmentin medicament
Pingback: ivermectin 6mg tablet for lice
Pingback: erythromycin tablets
Pingback: PS5 Digital for Sale
Pingback: mexico ivermectin
Pingback: ivermectin 0.5%
Pingback: ivermectin 0.08
Pingback: Magnum Research Desert Eagle for sale
Pingback: ivermectin human dosage
Pingback: cephalexin chlamydia
Pingback: oxytetracycline
Pingback: omnicef allergy
Pingback: cialis walmart
Pingback: plant viagra
Pingback: generic cialis tadalafil
Pingback: metronidazole dose
Pingback: cialis walmart
Pingback: online casino games win real money
Pingback: stromectol ingredients
Pingback: stromectol uk buy
Pingback: tiktok downloader
Pingback: stromectol 3mg tablets
Pingback: buy cialis online
Pingback: casino play real money usa
Pingback: generic
Pingback: marley drug sildenafil
Pingback: side effects for prednisone
Pingback: horse wormer ivermectin
Pingback: meritroyalbet
Pingback: levitra dosierung
Pingback: buy generic cialis from india
Pingback: tadalafil side effects
Pingback: vibrator
Pingback: rechargeable wand massagers
Pingback: new covid medicine
Pingback: male masturbator
Pingback: Buy DMT online Victoria Australia
Pingback: prednisone online pharmacy
Pingback: generic cialis daily
Pingback: buy prednisone australia
Pingback: tadalafil without a doctor prescription
Pingback: cialis price
Pingback: tombala siteleri
Pingback: viagra pour femme gold max
Pingback: sildenafil pills generic brand
Pingback: purchase sildenafil pills
Pingback: buy stromectol 12mg
Pingback: order tadalafil online
Pingback: kamagra vs cialis
Pingback: thelottovip
Pingback: cheap sildenafil 100mg
Pingback: tadalafil sandoz
Pingback: baymavi
Pingback: baymavi
Pingback: uk cialis no prescription
Pingback: where can i buy cialis without a prescription
Pingback: walther ppq vs hk vp9
Pingback: tadalafil wiki
Pingback: price of ivermectin liquid
Pingback: viagra generic online
Pingback: tadalafil cialis
Pingback: tadalafil cvs
Pingback: ivermectin humans
Pingback: online doctor prescription for viagra
Pingback: Glock for sale near me
Pingback: ivermectin price canada
Pingback: canadian provigil
Pingback: buy provigil with paypal
Pingback: home mortgage refinance
Pingback: canadian generic cialis online
Pingback: order tadalafil online
Pingback: meritroyalbet
Pingback: cialis kaufen
Pingback: cost prednisone 5mg
Pingback: cialis goodrx
Pingback: where to get ivermectin
Pingback: meritking
Pingback: meritking
Pingback: junk car removal
Pingback: ignition casino legal in us
Pingback: where to buy ivermectin
Pingback: ivermectin uk
Pingback: ivermectin uk
Pingback: ivermectin where to buy
Pingback: ivermectin generic
Pingback: ivermectin where to buy
Pingback: generic viagra cheap online
Pingback: ivermectin for humans
Pingback: ontime mastercard
Pingback: Anonymous
Pingback: ivermectin cream uk
Pingback: ivermectin 9 mg
Pingback: Anonymous
Pingback: ivermectin topical
Pingback: ivermectin syrup
Pingback: ivermectin 4000 mcg
Pingback: stromectol tablets uk
Pingback: topical ivermectin cost
Pingback: ivermectin 1 cream
Pingback: American Tactical Galeo for sale
Pingback: cost of stromectol medication
Pingback: sugar gliders for sale
Pingback: cost of baricitinib
Pingback: what is ivermectin used to treat in humans
Pingback: kory
Pingback: 5 mg tamoxifen
Pingback: Anonymous
Pingback: buy clomid nz
Pingback: latisse sale
Pingback: sextoys for women
Pingback: tizanidine
Pingback: ivermectin online
Pingback: ivermectin online
Pingback: buy ventolin germany
Pingback: ivermectin cream 5
Pingback: ivermectin lotion cost
Pingback: buy viagra pills from canada
Pingback: buy generic viagra in us
Pingback: USD to cryptocurrency
Pingback: cialis pills for men
Pingback: purchase stromectol
Pingback: litecoin wallet api
Pingback: ventolin purchase
Pingback: stromectol cream
Pingback: Mount Kilimanjaro Trek
Pingback: cheapest viagra online
Pingback: sex toy giveaway
Pingback: most powerful travel vibrators
Pingback: colt python 2020
Pingback: generic viagra reviews
Pingback: what strength does cialis come in
Pingback: difference between viagra and cialis
Pingback: can i take viagra every day
Pingback: buy k2 infused liquid paper online
Pingback: how much is cialis in canada
Pingback: gbl
Pingback: Krt disposable vape
Pingback: viagra tablets to buy online
Pingback: Bitcoin miner
Pingback: att corporate store
Pingback: viagra doses
Pingback: cialis 100mg india
Pingback: viagra sale pretoria
Pingback: vape carts
Pingback: Krt disposable vape
Pingback: mossberg 590m for sale
Pingback: beretta 1301 for sale
Pingback: cialis black 80mg
Pingback: calibre citoyen 8700
Pingback: mossberg 464 spx 30-30 for sale
Pingback: 50 or 100mg viagra
Pingback: keltecweapons com
Pingback: can i yake 5 pills sildenafil citrate
Pingback: does viagra expire
Pingback: best clit vibrator
Pingback: best male masturbator
Pingback: meritroyalbet
Pingback: blackjack game download software
Pingback: ZYDONE FOR SALE
Pingback: Honda Valkyrie
Pingback: buy uk driving license
Pingback: divorce lawyers
Pingback: 1justice
Pingback: choosing anal sex toy
Pingback: how to masturbate using a rechargeable clit vibrator
Pingback: suction cup dildos
Pingback: sex education
Pingback: crock ruger arms legit
Pingback: Android apps development
Pingback: Независимое бюро информации и аналитики
Pingback: azithromycin medication
Pingback: friend farms live resin cartridges
Pingback: Cohiba
Pingback: cialis free sample
Pingback: meritroyalbet
Pingback: meritking
Pingback: Paint Sprayer Reviews
Pingback: Monkeys for sale
Pingback: gbl for sale uk
Pingback: DMT AYAHUASCA FOR SALE
Pingback: gbl for sale uk
Pingback: Psilocybin mushrooms
Pingback: eurocasino
Pingback: eurocasino
Pingback: tubdy free player
Pingback: meritroyalbet
Pingback: madridbet
Pingback: eurocasino
Pingback: uca.com.vn
Pingback: elexusbet
Pingback: meritking
Pingback: tisas 1911 stainless
Pingback: dpms ar 15 tpr
Pingback: sig sauer guns for sale UK
Pingback: sildenafil 50mg
Pingback: restaurant food delivery
Pingback: stiiizy pen
Pingback: 2cb fly buy
Pingback: stiiizy battery
Pingback: cialis 5 mg generic usa
Pingback: taurus judge public defender
Pingback: ivermectin over the counter
Pingback: walter ccp m2 9mm for sale
Pingback: payday loans
Pingback: buy backlinks
Pingback: ecigarettes
Pingback: buy ecigarettes online
Pingback: buy gbl online uk
Pingback: buy pentobarbital sodium
Pingback: buy real uk driving licence
Pingback: Safari tours in Uganda
Pingback: beretta 686 silver pigeon
Pingback: where to buy cialis
Pingback: DailyCBD
Pingback: browning hog stalker 308 for sale
Pingback: viagra dosage 75mg
Pingback: Magic Mushroom Spores
Pingback: walther q5 match sf black tie
Pingback: how to masturbate using a silicone rechargeable vibrator
Pingback: couples sex kit
Pingback: Adderall for sale
Pingback: god s not dead 2
Pingback: Rajasthan Engineering College
Pingback: a christmas wedding
Pingback: Jawahar Navodaya VidyalayaGajanur Post Shimoga Distt. Karnataka Karnataka 577202 India
Pingback: Kashinagar High School Sreenagar-X, Kakdwip, South Twenty Four Pargan - 743347
Pingback: solar panels for home
Pingback: solar powered generators at home
Pingback: how to choose portable power stations for house
Pingback: e-cigarettes
Pingback: ruger handguns for sale
Pingback: affiliate millionaire
Pingback: undetectable fake money for sale
Pingback: supreme carts
Pingback: white hennessy near me
Pingback: russian surnames
Pingback: bitcoin wallet card
Pingback: virtual card buy with cryptocurrency
Pingback: TÜM HABERLER
Pingback: happyruck
Pingback: Gorilla Trekking Uganda Safaris
Pingback: Buy Buy Banana Diesel Strain of Marijuana Online
Pingback: CableFreeTV Tech News
Pingback: home made viagra
Pingback: asus-rog-strix-rtx-3060-8gb-gaming-v2-for-sale/
Pingback: Bitcoin Mining Hardware for Sale
Pingback: Buy Vyvanse Online UK
Pingback: Kolkata escorts
Pingback: cialis 40mg india
Pingback: azithromycin cost
Pingback: Rent a car Bar, Montenegro
Pingback: price of ivermectin
Pingback: cialis 10mg cost
Pingback: prednisone 54899
Pingback: best testosterone booster
Pingback: azithromycin tablets
Pingback: mango jull pods
Pingback: where to buy ventolin
Pingback: buy stromectol online
Pingback: buy modafinil 200 mg
Pingback: priligy singapore
Pingback: deltasone 40 mg
Pingback: order counterfeit money
Pingback: plaquenil 2 mg
Pingback: gabapentin cream
Pingback: list of all online casinos for us players
Pingback: furosemide 400 mg
Pingback: amoxicillin generic
Pingback: happyLuke
Pingback: MURANG'A UNIVERSITY
Pingback: buy raw garden cartridges online
Pingback: about canada pharmacy
Pingback: black mamba 24 strain glo cart
Pingback: srpc93
Pingback: polish ak 47 for sale
Pingback: Apetamin Syrup 200ml Online
Pingback: strokers
Pingback: sales at cheap generic viagra
Pingback: male masturbator
Pingback: babami sikin benim
Pingback: buy sig sauer guns online
Pingback: chlamydia treatment over the counter cvs
Pingback: raw garden extract
Pingback: beretta guns for sale
Pingback: savage grow
Pingback: Safari to Uganda
Pingback: Uganda Tour
Pingback: azithromycin 250 mg over the counter
Pingback: vioja mahakamani cast
Pingback: bitcoin
Pingback: dizziness
Pingback: Order Sig Sauer Firearms Online
Pingback: St James’ CE (VA) Primary School, Harlow
Pingback: RissMiner
Pingback: buy pills online uk
Pingback: finance news
Pingback: G17 GEN5 MOS FS STANDARD | 9X19MM
Pingback: Winchester SXP Hybrid
Pingback: شركة تسويق
Pingback: used concept 2 rower
Pingback: cyberpowerpc infinity x109 gaming pc
Pingback: Travelmonke Tours
Pingback: cheap generic viagra co uk kamagra oral jelly 100mg
Pingback: Fennec Fox for Sale
Pingback: buy graphics card online usa
Pingback: buy thc vape carts online
Pingback: online purchase of dapoxetine
Pingback: cheapest pharmacy for cialis
Pingback: costco gaming chairs
Pingback: ROVE CARTS
Pingback: smith and wesson sd40 for sale
Pingback: beretta 96 for sale
Pingback: juul mint
Pingback: potassium lisinopril interaction
Pingback: cheapest ed pills
Pingback: top shelf marijuana
Pingback: background check
Pingback: where can i buy viagra
Pingback: buying zithromax online uk
Pingback: cialis pills
Pingback: magic mushrooms
Pingback: stiiizy battery alternative Archives
Pingback: magic mushrooms
Pingback: pentobarbital for sale
Pingback: mossberg nightstick
Pingback: ivermectin for humans walmart
Pingback: bier haus slot machine for sale
Pingback: aa12 for sale
Pingback: sig sauer p320 x carry
Pingback: taurus raging hunter
Pingback: pdx1 defender 12 gauge
Pingback: ivermectin treatment for covid
Pingback: ivermectin for horses safe for humans
Pingback: ivermectin cancer
Pingback: GELATI STRAIN
Pingback: Buy Ketamine online
Pingback: albuterol sulfate hfa coupon
Pingback: dosage of ivermectin for dogs
Pingback: ivermectin sensitivity in dogs
Pingback: liquid ivermectin for cats
Pingback: buy zithramax powder
Pingback: lowes kronos login
Pingback: software
Pingback: stromectol for staph
Pingback: cialis online no prescription
Pingback: ivermectin for humans where to buy
Pingback: how do you take ivermectin
Pingback: stromectol for lymphatic filariasis
Pingback: cialis 5mg pharmacy
Pingback: aromatherapy for sleep
Pingback: Tanzania safari Serengeti
Pingback: ارقام بنات
Pingback: shipping containers for sale
Pingback: FARMING EQUIPMENT LIST
Pingback: best sex toys
Pingback: white water rafting in jinja uganda
Pingback: prednisone to buy uk
Pingback: Macbook pro akku tauschen zürich
Pingback: Best lodges in Masai Mara Kenya
Pingback: Shipping containers For Sale
Pingback: Pinball Machines for Sale
Pingback: generic propecia 1 mg
Pingback: ivermectin 12 mg per 5 cc
Pingback: best time to take amoxicillin
Pingback: Sig Sauer Handguns
Pingback: IT Support Bristol
Pingback: Communication digitale
Pingback: donde sale viagra
Pingback: THC Vape Oil for sale
Pingback: pc games for windows 8
Pingback: buy viagra in america
Pingback: mp3 downloader
Pingback: free download for windows 10
Pingback: games for pc download
Pingback: pc app
Pingback: free download for pc windows
Pingback: free download for windows 7
Pingback: app for pc download
Pingback: بديل تروكولر
Pingback: 1
Pingback: aranżacja wnętrz Gdynia
Pingback: what is duloxetine hcl dr caps 60mg used for
Pingback: clitoral stimulator
Pingback: hand job tips
Pingback: best pharmacy online
Pingback: Biddick Academy
Pingback: site es cheap viagra
Pingback: Golden Retriever Puppies For Sale Near Me
Pingback: cialis
Pingback: cockatoo for sale near
Pingback: cialis lilly
Pingback: big chief applejack
Pingback: quitting lexapro cold turkey
Pingback: Godfather Og strain
Pingback: kruidvat
Pingback: murchison falls tours
Pingback: sertraline 100mg price
Pingback: детские книги
Pingback: buy generic hydroxychloroquine online
Pingback: atorvastatin reviews
Pingback: ivermect tablet uses
Pingback: recall hydrochlorothiazide
Pingback: sildenafil in mexico for sale
Pingback: 안전놀이터
Pingback: 피망머니상
Pingback: https://shotgunsforsale.net/product/browning-citori-725-sporting-for-sale/
Pingback: mood changes when decreases in duloxetine
Pingback: clomid versus letrozole
Pingback: escitalopram oxalate 20 mg tablet
Pingback: victoria public school delhi
Pingback: lyrica vs gabapentin high
Pingback: best in ottawa
Pingback: quetiapine fumarate 25mg for anxiety
Pingback: best male masturbators
Pingback: who manufactures ivermectin
Pingback: 1xbit download
Pingback: rabbit thruster
Pingback: how to use a stretchy penis ring
Pingback: sex
Pingback: best sex toys for men
Pingback: fluoxetine with alcohol
Pingback: prilosec lawsuit 2016
Pingback: realistic masturbators
Pingback: z pack and alcohol consumption
Pingback: twitter video downloader
Pingback: CTRLCOIN
Pingback: what is the generic name for lipitor
Pingback: melhores smartphones
Pingback: streaming gratuit
Pingback: film streaming 2021
Pingback: amlodipine maximum dose 20 mg
Pingback: car transport service
Pingback: site de streaming
Pingback: 99defi.network
Pingback: atakoy escort
Pingback: Cannabis Oil
Pingback: سکس انلاین
Pingback: how to use lifelike dildo
Pingback: realistic dildo
Pingback: best sex toys for men
Pingback: prostate vibrating massagers
Pingback: huay
Pingback: lotto vip
Pingback: ground lease
Pingback: how long does tamoxifen stay in body
Pingback: hosting deals
Pingback: lottovip
Pingback: Best Masturbator
Pingback: vibrators for women
Pingback: sequal eclipse 5
Pingback: vibrating ass stroker
Pingback: vibrator for women
Pingback: male p spot vibrator
Pingback: vibrating panty
Pingback: fun88
Pingback: Asian Restaurant
Pingback: buy weed in Arkansas
Pingback: mersin escort
Pingback: silicone prostate vibrator
Pingback: sex toys for gay
Pingback: dapoxetine prostate medication
Pingback: canadapharmacycanada.com
Pingback: best thrusting vibrator
Pingback: ben wah balls
Pingback: Local Shroom Delivery
Pingback: ivermectil trihydrate wiki
Pingback: over the counter viagra substitute cvs
Pingback: ทางเข้า happyluke
Pingback: besiktas escort
Pingback: anadolu yakasi escort
Pingback: regcialist.com
Pingback: cleaning silicone sex toys
Pingback: AMI Hospital Management
Pingback: walmart online pharmacy medical expense report
Pingback: pocket masturbator
Pingback: shopping haul challenge
Pingback: best handheld massager
Pingback: happyluke
Pingback: happyluke โปรโมชั่น
Pingback: US Trending News
Pingback: Buy Ecstasy Pills Online
Pingback: vietnam and chloroquine
Pingback: gaziosmanpasa escort
Pingback: best canadian pharmacy for cialis
Pingback: viagra government funded
Pingback: buy cialis viagra
Pingback: asmr porn
Pingback: order prescription drugs online without doctor
Pingback: best herbal viagra
Pingback: penis extender
Pingback: rechargeable penis pump
Pingback: venus butterfly remote
Pingback: DIAGNOSIS OF TYPE 1 DIABETES
Pingback: male strokers
Pingback: their information
Pingback: Lion Cubs For Sale
Pingback: spiritual healing
Pingback: canada pharmacy
Pingback: Buy Ruger Guns Online
Pingback: amoxicillin buy online india
Pingback: sildenafil prices
Pingback: sildenafil walmart
Pingback: viagra buy
Pingback: glo cartridges
Pingback: cialis and depression
Pingback: buy bubba kush online
Pingback: buy weed in detriot
Pingback: cialis 20
Pingback: معرفة هوية المتصل
Pingback: cialis timeline
Pingback: canada pharmacy canada pharmacy
Pingback: Buy guns online discreetly
Pingback: cipro antibiotic wiki
Pingback: buy Juul pods online
Pingback: latest technology
Pingback: HBCUO
Pingback: Canadian service
Pingback: tueran
Pingback: top sex toys for women
Pingback: cost of metronidazole pills
Pingback: tadalafil research chemical
Pingback: tadalafil capsule
Pingback: maximum dose zanaflex
Pingback: valtrex cost at walmart
Pingback: naltrexone for autistic children
Pingback: prednisolone ophthalmic indication
Pingback: tamoxifen retinopathy
Pingback: costco shed
Pingback: diflucan dosing for thrush
Pingback: clomid and fibroids
Pingback: careprost eyelash growth usa
Pingback: propecia 1mg generic
Pingback: dapoxetine cost
Pingback: xenical pills uk
Pingback: furosemide 80 mg tablet
Pingback: how to get rid of belly fat
Pingback: doxycycline 100mg
Pingback: amoxicillin and clavulanate
Pingback: bulk dungeness crab for sale
Pingback: Squat Rack
Pingback: xs sights
Pingback: 40mg cialis
Pingback: why is metformin dangerous
Pingback: levitra overdose
Pingback: cialis 20mg tablets
Pingback: amlodipine 5mg
Pingback: Vape Carts For Sale
Pingback: armadillo girdled lizards for sale
Pingback: Sig M18
Pingback: household furniture warehouse
Pingback: canada pharmacy
Pingback: Roofing Services
Pingback: sildenafil cream
Pingback: viagra cheap
Pingback: sultanbeyli escort
Pingback: doctor recommends hydroxychloroquine
Pingback: sildenafil revatio
Pingback: viagra stock
Pingback: escort bayan
Pingback: viagra canada prescription
Pingback: MILF Porn Land
Pingback: sildenafil 20mg daily
Pingback: sildenafil tablets 120mg
Pingback: eli lilly cialis coupon
Pingback: how fast does hydroxychloroquine work
Pingback: tadalafil 10mg cost
Pingback: hydroxychloroquine brand names
Pingback: MUT
Pingback: Delivery Restaurant Parksville
Pingback: Glock Guns for sale
Pingback: Data obligasi
Pingback: lady viagra
Pingback: generic vardenafil 20mg india
Pingback: cialis india pharmacy
Pingback: moving company
Pingback: guns for sale
Pingback: friendly farms carts
Pingback: ptr 9ct for sale
Pingback: buy guns online
Pingback: levitra 20mg uk
Pingback: buy tiktok followers
Pingback: albino a+
Pingback: tadalafil generic india
Pingback: SF Examiner
Pingback: cialis mexico pharmacy
Pingback: buy weed
Pingback: buy cialis from canada
Pingback: cialis europe
Pingback: marijuana dispensaries near me
Pingback: Seattle Weekly
Pingback: buy weed
Pingback: marijuana dispensaries
Pingback: BIG CHIEF EXTRACTS
Pingback: vibrator review
Pingback: best classic vibrators
Pingback: zithromax 500 mg tablet
Pingback: sex toy reviews
Pingback: erythromycin 2 gel cost
Pingback: cleocin
Pingback: buy keflex online
Pingback: cefdinir 300 mg
Pingback: azithromycin capsules 250mg
Pingback: generic augmentin
Pingback: aricept for dementia
Pingback: augmentin vs amoxicillin
Pingback: acyclovir side effects
Pingback: bachelor's degree
Pingback: how do sulfamethoxazole pills look like
Pingback: delta 8
Pingback: Observer
Pingback: buy cbd gummies
Pingback: Edibles
Pingback: vardenafil 20mg india manufacturer
Pingback: walmart viagra
Pingback: cialis 600 mg
Pingback: rx sildenafil tablets
Pingback: cialis cvs
Pingback: cytotmeds.com
Pingback: double ended dildo
Pingback: blogery_i_dorogi
Pingback: flagyl 500 mg tablet
Pingback: coreg medication
Pingback: finasteride side effects permanent
Pingback: Food License in Jaipur
Pingback: clonidine dosing for anxiety
Pingback: diclofenac potassium 50 mg
Pingback: whats the keto diet
Pingback: wellbutrin generic
Pingback: zanaflex 4mg
Pingback: celexa side effects
Pingback: buspirone 10 mg
Pingback: wellbutrin reviews
Pingback: tides today at tides.today
Pingback: Keto diet
Pingback: side effects for mirtazapine
Pingback: metformin cancer
Pingback: warnings for hydrochlorothiazide
Pingback: duloxetine hydrochloride
Pingback: amitriptyline for migraines
Pingback: prednisone 50 mg
Pingback: what is cymbalta
Pingback: vardenafil 5mg
Pingback: cheap online cialis
Pingback: daily viagra
Pingback: losartan recall 2020
Pingback: metoprolol tartrate 50mg
Pingback: meloxicam dosage
Pingback: sex toys for large girls
Pingback: best delta 8 thc gummies
Pingback: cell phone repair shop mission Viejo
Pingback: atorvastatin dosage
Pingback: buy Instagram likes
Pingback: free adult dating sites
Pingback: best delta 8 THC vape cartridges
Pingback: best delta 8
Pingback: generic norvasc
Pingback: herbal viagra
Pingback: podolsk-region.ru
Pingback: buy real Instagram likes
Pingback: what is relative dating
Pingback: best kratom
Pingback: onlinedatingtwo.com
Pingback: buy kratom
Pingback: kratom capsules
Pingback: levitra tab 20mg
Pingback: on line cialis
Pingback: gabapentin 600 mg
Pingback: generic viagra
Pingback: buy acyclovir online
Pingback: soderzhanki-3-sezon-2021.online
Pingback: cheapest viagra 100mg
Pingback: tadalafil research powder
Pingback: Dating online
Pingback: PULVERIZER
Pingback: online dating scams pictures
Pingback: latest technology. news
Pingback: Login Aluno
Pingback: Pound of Weed for Sale
Pingback: PARROTS FOR SALE
Pingback: GOLDEN RETRIEVER PUPPIES FOR SALE
Pingback: Buy Marijuana Online
Pingback: arcade pinball machines
Pingback: whole alligator meat for sale
Pingback: g spot stimulator
Pingback: sildenafil capsule
Pingback: generic tadalafil daily
Pingback: cialis pharmacy cost
Pingback: adam and eve g spot vibrator
Pingback: best male masturbators
Pingback: prostate toy
Pingback: viagra free sample
Pingback: tadalafil online
Pingback: vibrating strapless dildo
Pingback: Buy Weed Online
Pingback: A line hair cut in Irvine
Pingback: generic for keflex 500 mg
Pingback: viagra with dapoxetine
Pingback: deep thrusting rabbit vibrator
Pingback: anal training plugs
Pingback: buy kratom
Pingback: aurogra sildenafil 100mg
Pingback: sex facts
Pingback: best clit stimulator
Pingback: price of tadalafil
Pingback: electric motorbike canada
Pingback: phone screen repair irvine
Pingback: best delta 8 gummies
Pingback: slot online
Pingback: Dental insurance BC
Pingback: buy sig sauer guns online
Pingback: about canada
Pingback: eskort maltepe
Pingback: virtual card buy for online shopping
Pingback: ar 15 rifle for sale
Pingback: cz scorpion evo 3
Pingback: homemade sex toys
Pingback: pharmacy in canada
Pingback: sex toy reviewer
Pingback: most bizarre sex toys
Pingback: anal beads for beginners
Pingback: Hk mp5 for sale
Pingback: mobile homes for sale alpena mi
Pingback: bimatoprost ophthalmic solution 0.03% amazon
Pingback: porn
Pingback: mobile homes for sale alpena mi
Pingback: phone repair store
Pingback: realistic cumming dildo
Pingback: vibrating and thrusting dildo
Pingback: נערות ליווי בחיפה
Pingback: caluanie for sale
Pingback: ivermectin dosage
Pingback: vibrators
Pingback: bondage sex toys
Pingback: umraniye fetis yapan escort
Pingback: Dildo
Pingback: best sex toys
Pingback: cialis online/canada
Pingback: compare canadian pharmacy prices
Pingback: best 10 online canadian pharmacies
Pingback: centurion laboratories vidalista
Pingback: شركة كشف تسربات المياه بالرياض
Pingback: is it illegal to buy drugs from canada
Pingback: top
Pingback: cialis daily use side effects
Pingback: http://freeadultdatingusus.com/
Pingback: freedatingfreetst.com
Pingback: cialis rx coupon
Pingback: goodrx.com cialis
Pingback: Architectural design
Pingback: cialis and viagra
Pingback: cialis daily price
Pingback: where can i buy ativan in philippines
Pingback: totally free online dating australia
Pingback: site
Pingback: Ukrainskie-serialy
Pingback: lovoo mit facebook
Pingback: afisha-kinoteatrov.ru
Pingback: new hydroxychloroquine studies
Pingback: generic canadian
Pingback: bàn học cho bé
Pingback: gas fireplace
Pingback: how long for viagra to kick in
Pingback: how long do ciprofloxacin side effects last
Pingback: Vortex Venom
Pingback: generic canadian
Pingback: anal sex toys
Pingback: top sex toys
Pingback: nanaimo area
Pingback: video
Pingback: topvideos
Pingback: learn more
Pingback: Buy Hydrocodone 500 mg
Pingback: kinoteatrzarya.ru
Pingback: buy time crisis 4
Pingback: how to super like on tinder
Pingback: everest cash advance lakeville
Pingback: jack495 tinder
Pingback: SEO Marketing
Pingback: does viagra cause angina
Pingback: viagra voorschrift belgie
Pingback: visit website
Pingback: vancouverbitcoinatm.net
Pingback: SEA VOYAGES
Pingback: bitcoin wallet card
Pingback: tadalafil soft gel capsule
Pingback: retin a no prescription needed
Pingback: projectio freid
Pingback: top sex toys for women
Pingback: psy
Pingback: lesbian strapon
Pingback: موقع سكس
Pingback: payday loan lenders glendale
Pingback: find out more
Pingback: dapoxetine soft tabs vs pills
Pingback: buy cheap overnight
Pingback: escorts
Pingback: can i buy cialis in toronto
Pingback: RECREATIONAL THC FOR SALE
Pingback: super cialis best price
Pingback: vibrating panties
Pingback: buy cialis cheap online
Pingback: 4569987
Pingback: mail order cialis
Pingback: tadalafil 5mg canada generic
Pingback: non prescription online pharmacy reviews
Pingback: SEO Nanaimo
Pingback: augmentin antibiotic 875 mg
Pingback: Zakhar Berkut
Pingback: https aka ms remoteconnect microsoft
Pingback: buy cialis from india online
Pingback: cialis original for sale
Pingback: buy adhd meds online canada
Pingback: honda dirt bikes
Pingback: Hypodermic Needle
Pingback: trusted online pharmacy reviews
Pingback: buy furosemide 100 mg
Pingback: buy cbd hemp flowers in Europe
Pingback: buy shipping container
Pingback: pillole di levitra
Pingback: Buy Dmt Vape pen with Bitcoins online
Pingback: generic cialis reviews australia
Pingback: over counter viagra walgreens
Pingback: half life of azithromycin
Pingback: viagra 50 mg achete online
Pingback: generic cialis name australia
Pingback: Mestinon
Pingback: cialis dosage reddit australia
Pingback: canadian viagra 100mg
Pingback: tadalafil 100mg best price
Pingback: trump viagra healthcare paraday
Pingback: cialis pills canada
Pingback: viagra purchase in india
Pingback: buy cialis online reddit
Pingback: cialis otc when patent expires
Pingback: buy Instagram followers
Pingback: generic cialis 2018 usa
Pingback: Weed Wax
Pingback: cialis 20 mg shop online
Pingback: generic tadalafil cheap
Pingback: cost of 100mg viagra
Pingback: sildenafil 100 mg tablet cost
Pingback: tetracycline antibiotics for cats
Pingback: buy cialis price
Pingback: cialis 100mg for sale
Pingback: cialis actress australia
Pingback: viagra reviews reddit australia
Pingback: Web Design and SEO Company In Saudi Arabia
Pingback: compare generic cialis prices
Pingback: canadian pharmacy viagra 200 mg
Pingback: Guns for sale
Pingback: Loft Clearance Services UK
Pingback: order generic viagra uk
Pingback: End Of Tenancy Cleaning Castlenau
Pingback: siamese kittens for sale near me
Pingback: how to buy guns onlinesig suaer p320
Pingback: psilocybe semilanceata
Pingback: sig p365
Pingback: Vidalista 60mg
Pingback: Coinbase
Pingback: hydroxychloroquine veterans study
Pingback: tadalafil 5 mg brands in india
Pingback: generic cialis drugstore
Pingback: whitney wright viagra
Pingback: 코인카지노
Pingback: cialis sales
Pingback: 메리트카지노
Pingback: 퍼스트카지노
Pingback: 우리카지노
Pingback: albuterol inhaler amazon
Pingback: 샌즈카지노
Pingback: cialis without prescriptions australia
Pingback: lilly cialis
Pingback: buy the best guns online
Pingback: service marketplace
Pingback: TOLTRAZURIL FOR SALE
Pingback: buy cialis over the counter uk
Pingback: online pharmacy no prescription
Pingback: where to buy delta 8
Pingback: viagra 25
Pingback: online pharmacies canada
Pingback: buy delta 8
Pingback: multi coin bot
Pingback: buying drugs canada
Pingback: buy liquid herbal incense online
Pingback: Homes For Sale Belpre Ohio
Pingback: bare copper wire
Pingback: plaquenil drug
Pingback: paxil prescribing information
Pingback: 20 foot shipping container
Pingback: Buy THC Vape Juice in Europe
Pingback: glipizide metformin
Pingback: 600 milligram neurontin
Pingback: virtual visa and MasterCard buy
Pingback: cryptocard
Pingback: sildenafil capsule
Pingback: Pharmacy Canada
Pingback: Buy Methyltrienolone Powder
Pingback: brand cialis 20mg
Pingback: latest crypto news
Pingback: buy generic cialis with paypal
Pingback: Canada Pharmacy
Pingback: buy cialis online visa
Pingback: shipping containers for sale duluth mn
Pingback: reddit buy guns online
Pingback: pinball machines for sale nebraska
Pingback: viagra cialis from germany
Pingback: Furniture
Pingback: cialis in mexico price
Pingback: write my paper for cheap
Pingback: canada vs usa
Pingback: Herbal incense
Pingback: writing custom essays
Pingback: thc vape juice
Pingback: Herbal incense
Pingback: Webseite kaufen
Pingback: online propecia prices
Pingback: Pc support rapperswil
Pingback: best price for cialis
Pingback: uk dissertation help
Pingback: is generic tadalafil as effective as vidalista
Pingback: click here
Pingback: essay proofreading services
Pingback: custom essay writers
Pingback: https://trippydelics.ca
Pingback: buy Etizolam powder online
Pingback: editing thesis
Pingback: curso mauricio alabama
Pingback: MAGIC MUSHROOM GROW KIT
Pingback: examples of dissertation proposals
Pingback: psilocybe cubensis grow kit usa
Pingback: academic essay writing services
Pingback: thesis proposal writing
Pingback: buy essays
Pingback: armour vs synthroid
Pingback: diflucan drug interactions
Pingback: la dapoxetine
Pingback: clomid fertility treatment
Pingback: prednisolone usp
Pingback: thomas labs doxycycline
Pingback: Google
Pingback: cost of clotrimazole 10g
Pingback: how much is cialis 20mg in canada
Pingback: metoprolol otc
Pingback: generic tadalafil for sale
Pingback: how to purchase gemfibrozil 300mg
Pingback: how to take aurogra tablets
Pingback: how to get ventolin
Pingback: stromectol tablets uk
Pingback: zithromax online no prescription
Pingback: lasix 200 mg
Pingback: tri amoxicillin
Pingback: order atorvastatin 20 mg
Pingback: cialis como funciona
Pingback: cialis 20mg for sale
Pingback: acyclovir long term side effects
Pingback: generic cialis canadian
Pingback: levothyroxine mcg united kingdom
Pingback: is vidalista safe to use
Pingback: when is dapoxetine going generic
Pingback: levofloxacin without a prescription
Pingback: aurogra generic
Pingback: terbinafine 250 mg without a prescription
Pingback: best prices cialis 5mg
Pingback: hydroxychloroquine plaquenil side effects
Pingback: lamotrigine 25mg no prescription
Pingback: hydroxychloroquine and zithromax
Pingback: cialis pills sale canada
Pingback: states allowing hydroxychloroquine
Pingback: Google
Pingback: best place to order cialis online
Pingback: how to buy cialis online from canada
Pingback: hydroxychloroquine vietnam vets
Pingback: cialis in europe
Pingback: cialis dosages available
Pingback: business ethics essay thesis statement
Pingback: personal essay help
Pingback: write my essay uk reviews
Pingback: how to write a mla research paper
Pingback: cheap custom essay writing services
Pingback: dapoxetine fda indications
Pingback: viagra without prescription
Pingback: pharmacy in singaporeviagra
Pingback: se puede comprar viagra sin receta en farmacias fisicas
Pingback: cialis without prescriptions canada
Pingback: viagra before surgery
Pingback: cialis 20mg
Pingback: how much does cialis cost with insurance
Pingback: tadalafil without a doctor’s prescription
Pingback: cialis 20mg lowest price
Pingback: azathioprine cheap
Pingback: generic viagra online
Pingback: where to get viagra pills
Pingback: viagra vs cialis vs levitra
Pingback: cialis 20mg for sale
Pingback: cialis generico barato contrareembolso
Pingback: loperamide prices
Pingback: active ingredients viagra cialis
Pingback: sumatriptan 25 mg nz
Pingback: isosorbide 30mg cheap
Pingback: what is the dosage for hydroxychloroquine
Pingback: overnight viagra us pharmacy
Pingback: does trump have investments in hydroxychloroquine
Pingback: glipizide united kingdom
Pingback: azithromycin strep throat how long
Pingback: what pharmacy carries ivermectin
Pingback: duloxetine generic brands
Pingback: wat doet viagra met je lichaam
Pingback: wat kost sildenafil bij apotheek
Pingback: where to buy viagra without
Pingback: nitrofurantoin pills
Pingback: how long does it take for viagra to work?
Pingback: ivermectin cancer dose human
Pingback: correct dose of cephalexin
Pingback: alendronate price
Pingback: celebrex for tendonitis
Pingback: fluticasone mcg without a prescription
Pingback: viagra without a prescription
Pingback: azithromycin for uti
Pingback: tjmaowze
Pingback: buy hydroxychloroquine from mexico
Pingback: buy etodolac
Pingback: generic vidalista
Pingback: estradiol 1 mg price
Pingback: cialis cheap
Pingback: generic tadalafil prices
Pingback: ndsxmrpx
Pingback: how much are 30 generic cialis pills
Pingback: buy cialis online overnight
Pingback: buy erythromycin 500mg
Pingback: cheap permethrin
Pingback: can i take expired amoxicillin
Pingback: how to buy amitriptyline 50 mg
Pingback: viagra 50mg pharmacy
Pingback: cymbalta treats
Pingback: viagra free trial
Pingback: venlafaxine 75mg generic
Pingback: buy cialis tadalafil tablets
Pingback: cephalexin k9
Pingback: bisacodyl purchase
Pingback: synthesis of celebrex
Pingback: doxycycline 100 mg no prescription
Pingback: what infections does azithromycin treat
Pingback: oxybutynin 2.5mg prices
Pingback: cialis online daily
Pingback: zithromax 500 mg tablet
Pingback: phenytoin 100 mg usa
Pingback: how does amoxicillin work
Pingback: fluconazole prices
Pingback: safest and most reliable pharmacy to buy cialis
Pingback: acetazolamide 250 mg for sale
Pingback: how much does cialis cost with insurance
Pingback: buy tolterodine 1 mg
Pingback: trazodone price
Pingback: buy viagra no prescription
Pingback: aurogra chewable tablets
Pingback: divalproex over the counter
Pingback: desmopressin 10mcg united kingdom
Pingback: generic ivermectin without doctor visit
Pingback: rosuvastatin 5mg canada
Pingback: buy cialis online without prescription
Pingback: warfarin no prescription
Pingback: buy carvedilolmg
Pingback: cialis 20 mg price
Pingback: why cant i buy viagra online anymore
Pingback: buy cialis with paypal
Pingback: where to buy prochlorperazine
Pingback: how to purchase clozapine 25 mg
Pingback: buy cialis rush
Pingback: clindamycin online
Pingback: original cialis
Pingback: cialis generic walmart
Pingback: ciprofloxacin coupon
Pingback: cialis 20mg for sale
Pingback: buy cialis online from canada
Pingback: cephalexin 500 mg price
Pingback: citalopram 10 mg online pharmacy
Pingback: cialis dosage recommended
Pingback: how to purchase celecoxib
Pingback: where can i buy cefuroxime
Pingback: cheapest clonidinemg
Pingback: how to purchase buspirone 10mg
Pingback: olmesartan 40mg united states
Pingback: dutasteride 0,5 mg without a prescription
Pingback: irbesartan australia
Pingback: anastrozole pills
Pingback: donepezil over the counter
Pingback: teva pharmaceuticals viagra
Pingback: atomoxetine 25mg purchase
Pingback: leflunomide without prescription
Pingback: meclizine 25mg generic
Pingback: glimepiride medication
Pingback: getingan erection with viagra
Pingback: fexofenadine 120mg united kingdom
Pingback: spironolactone without prescription
Pingback: difference between viagra and cialis
Pingback: risk of taking cefixime
Pingback: pioglitazone pharmacy
Pingback: cheap viagra online isa
Pingback: aripiprazole 10 mg coupon
Pingback: escitalopram without prescription
Pingback: furosemide 40 mg purchase
Pingback: tadalafil without a prescription
Pingback: sildenafil australia
Pingback: vidalista tablets price in india
Pingback: how to buy zyvox 600mg
Pingback: viagra stories
Pingback: zyprexa without a doctor prescription
Pingback: zyloprim coupon
Pingback: viagra without a doctor prescription walmart
Pingback: zovirax 400 mg purchase
Pingback: order ivermectin
Pingback: zocor cheap
Pingback: visit this site
Pingback: buy cialis 20mg india
Pingback: cialis with dapoxetine
Pingback: zanaflex for sale
Pingback: dosage for sildenafil citrate 20mg
Pingback: wellbutrin generic
Pingback: voltaren 50 mg over the counter
Pingback: where to buy verapamil 40mg
Pingback: viagra thin blood
Pingback: how to purchase vantin
Pingback: cialis vs viagra dosage comparison
Pingback: who will prescribe hydroxychloroquine
Pingback: prednisone coupon walgreens
Pingback: where can i buy valtrex 1000mg
Pingback: tricor 160 mg without a doctor prescription
Pingback: viagra erection cum shot
Pingback: stromectol dose for scabies
Pingback: toprol nz
Pingback: thorazine canada
Pingback: can you take 40mg of cialis
Pingback: buy tenormin
Pingback: emtpartsstore viagra
Pingback: spiriva united kingdom
Pingback: skelaxin 400mg nz
Pingback: singulair united kingdom
Pingback: seroquel medication
Pingback: rogaine 5% uk
Pingback: robaxin 500mg usa
Pingback: risperdal usa
Pingback: cheap revatio
Pingback: retin-a cream 0.05% online
Pingback: sildenafil interaction with alcohol
Pingback: remeron 15 mg without a prescription
Pingback: india pharmacy cialis generic
Pingback: reglan over the counter
Pingback: pyridium 200mg purchase
Pingback: viagra for sale over counter
Pingback: pulmicort australia
Pingback: provigil 100mg for sale
Pingback: protonix canada
Pingback: proscar 5mg nz
Pingback: roman erectile dysfunction cost
Pingback: proair inhaler 100 mcg canada
Pingback: prilosec prices
Pingback: prevacid 30 mg generic
Pingback: buy prednisolone 5 mg
Pingback: plaquenil australia
Pingback: phenergan generic
Pingback: dapoxetine time window
Pingback: brand viagra online
Pingback: periactin 4mg purchase
Pingback: https://amstyles.com/
Pingback: nortriptyline online
Pingback: hydroxychloroquine drug
Pingback: Viagra with Duloxetine
Pingback: how to purchase motrin
Pingback: order cialis online pharmacy
Pingback: no prescription online pharmacy
Pingback: mobic tablet
Pingback: canada pharmacy online
Pingback: where can i buy micardis 20 mg
Pingback: cheap viagra online canadian pharmacy
Pingback: pharmacy in canada
Pingback: where can i buy mestinon
Pingback: viagra fast delivery
Pingback: meclizine usa
Pingback: macrobid 100 mg pharmacy
Pingback: luvox without a prescription
Pingback: how to purchase lopressor 100mg
Pingback: lopid australia
Pingback: cheapest levaquin
Pingback: indocin 25 mg medication
Pingback: buy viagra
Pingback: imuran generic
Pingback: pfizer viagra
Pingback: viagra dosage for 70 year old
Pingback: canadian pharmacy viagra
Pingback: click here for more info
Pingback: where to buy imodium 2 mg
Pingback: buy imitrex 25mg
Pingback: does cialis work
Pingback: how long for cialis to peak
Pingback: cialis buy online
Pingback: cialis pills
Pingback: cialis ordering
Pingback: where can i buy imdur 60mg
Pingback: order hyzaar
Pingback: geodon 80 mg for sale
Pingback: garcinia cambogia 100caps no prescription
Pingback: ordering cialis generic online
Pingback: flonase nasal spray usa
Pingback: flomax cheap
Pingback: where to buy etodolac 400mg
Pingback: where can i buy erythromycin
Pingback: dramamine generic
Pingback: doxycycline united states
Pingback: diltiazem 60mg prices
Pingback: where to buy differin
Pingback: Overnight delivery viagra
Pingback: diamox purchase
Pingback: depakote online pharmacy
Pingback: ddavp 0.1mg medication
Pingback: can someone write my paper for me
Pingback: phd by thesis only
Pingback: dapsone 1000caps nz
Pingback: who can write my research paper
Pingback: free thesis help
Pingback: order cialis black online
Pingback: cymbalta 40 mg without prescription
Pingback: online essay help
Pingback: custom essays review
Pingback: cost of crestor 20 mg
Pingback: viagra next day delivery
Pingback: mba admission essay writing service
Pingback: dissertationhelpvfh.com
Pingback: cozaar for sale
Pingback: coumadin 2 mg without prescription
Pingback: help me to write an essay
Pingback: compazine purchase
Pingback: cialis
Pingback: order cialis online canada
Pingback: coreg 25 mg cost
Pingback: ergaeaergaergarthrhthhrsh
Pingback: order combivent 50/20mcg
Pingback: http://sadfaasdfasfafadsfa.com
Pingback: cialis 20mg canada
Pingback: Buy viagra now
Pingback: viagra from canada
Pingback: symbicort inhaler 160/4,5mcg tablets
Pingback: colchicine without a doctor prescription
Pingback: clozaril prices
Pingback: Testosterone Supplements
Pingback: Fda approved viagra
Pingback: cost of clonidine
Pingback: ordering cialis online australia
Pingback: viagra brand coupon
Pingback: clomid usa
Pingback: cleocin online
Pingback: cheap essay writing service us
Pingback: write a college essay
Pingback: writer essay
Pingback: where to buy generic viagra online in canada
Pingback: professional paper writers
Pingback: writing my essay
Pingback: writer of the federalist papers
Pingback: reliable essay writing service
Pingback: pfizer viagra online without prescription
Pingback: buy essay
Pingback: sildenafil 500 mg
Pingback: online essay writing service review
Pingback: cbd oil for cancer for sale
Pingback: viagra purchase in india
Pingback: best potent cbd oil for dogs with cancer
Pingback: cbd oil legal in all 50 states
Pingback: viagra 100mg australia
Pingback: buy levitra safely online
Pingback: ananda professional cbd oil
Pingback: cbd oil for sale online
Pingback: generic viagra online canada
Pingback: viagra 50 mg
Pingback: benefits of cbd oil for cancer patients
Pingback: how much is 50 mg viagra
Pingback: cbd oil for sale in georgia
Pingback: cheap cbd oil for sale
Pingback: ananda professional cbd oil
Pingback: personal loan definition
Pingback: california payday loans
Pingback: bad credit loans nj
Pingback: guaranteed quick loans
Pingback: easy installment loans
Pingback: Buy cheap viagra internet
Pingback: buy cialis usa
Pingback: buying viagra online canada
Pingback: check cashing
Pingback: payday loans knoxville tn
Pingback: same day personal loans
Pingback: car insurance cheap
Pingback: generic cialis
Pingback: get a car insurance quotes
Pingback: top car insurance
Pingback: generic cialis
Pingback: buy cialis online
Pingback: best car insurance
Pingback: car insurance quotes in nj
Pingback: car insurance texas
Pingback: rental car insurance quotes
Pingback: cheap generic viagra
Pingback: insurance comparison
Pingback: automobile insurance
Pingback: car insurance quotes estimate
Pingback: online casinos real money
Pingback: vegas casino online
Pingback: doubleu casino online casino
Pingback: online casino real money usa
Pingback: real casino
Pingback: empire casino online
Pingback: online casino games for real money
Pingback: online casino games real money
Pingback: slot games
Pingback: casino online
Pingback: claritin cheap
Pingback: cipro united kingdom
Pingback: cephalexin 500mg usa
Pingback: celexa tablets
Pingback: where to buy celebrex 200 mg
Pingback: ceftin cheap
Pingback: ceclor uk
Pingback: catapres 100 mcg over the counter
Pingback: cost of casodex 50mg
Pingback: viagra for sale in spain
Pingback: how to purchase cardizem 180 mg
Pingback: how to purchase calcium carbonate 500mg
Pingback: how long for cialis to work
Pingback: how to buy buspar 5mg
Pingback: cheapest Premarin 0,3mg
Pingback: Biaxin 250 mg pills
Pingback: how long does cialis 10mg last
Pingback: benicar 10 mg canada
Pingback: bactrim 800/160mg online
Pingback: viagra copyright
Pingback: cheapest avodart 0,5mg
Pingback: https://keflex.webbfenix.com
Pingback: avapro 150 mg price
Pingback: cost of augmentin 500/125mg
Pingback: atarax 25 mg prices
Pingback: cialis mexico
Pingback: ashwagandha 60caps online
Pingback: buy tamoxifen 10mg
Pingback: arimidex 1mg without prescription
Pingback: www.bee-rich.com
Pingback: cialistodo.com
Pingback: viagra kick in
Pingback: aricept 10mg no prescription
Pingback: arava 10 mg coupon
Pingback: where to buy antivert 25 mg
Pingback: antabuse 500 mg purchase
Pingback: buy ampicillin 500mg
Pingback: amoxicillin 500 mg online pharmacy
Pingback: amaryl 4mg without prescription
Pingback: allopurinol 300mg price
Pingback: allegra 180mg tablet
Pingback: aldactone 100mg purchase
Pingback: actos 30 mg coupon
Pingback: abilify 20mg cheap
Pingback: viagra without a doctor prescription
Pingback: viagra for sale
Pingback: viagra generic
Pingback: where to buy lexapro 10mg
Pingback: propecia 1mg prices
Pingback: furosemide 100mg canada
Pingback: cheapest lasix 100mg
Pingback: lm360.us
Pingback: where can i buy levitra 40mg
Pingback: tadalafil 60 mg prices
Pingback: cost of sildenafil 150mg
Pingback: https://www.azhydroxychloroquine.com/
Pingback: Cialis 80 mg usa
Pingback: Cialis 60mg cheap
Pingback: how to buy Cialis 20 mg
Pingback: Cialis 80 mg without a prescription
Pingback: viagra generic
Pingback: Cialis 20 mg medication
Pingback: viagra buy
Pingback: Cialis 80mg nz
Pingback: Cialis 20 mg online
Pingback: buy cialis
Pingback: cialis coupon
Pingback: Viagra 25mg otc
Pingback: Viagra 150mg online
Pingback: generic cialis cheap
Pingback: hydroxychloroquine india
Pingback: where can i buy Viagra 100 mg
Pingback: Viagra 100 mg without a prescription
Pingback: generic viagra coupon
Pingback: free slots online
Pingback: generic viagra pills for sale
Pingback: casino online real money
Pingback: viagra pills
Pingback: buy generic cialis online
Pingback: best generic viagra websites reviews
Pingback: tadalafil tablets
Pingback: viagra online usa
Pingback: viagra cheap
Pingback: cheapest viagra online
Pingback: real money online casinos usa
Pingback: best online casino for money
Pingback: play casino
Pingback: online casino games real money
Pingback: cialis internet
Pingback: cialis 20
Pingback: 5 mg cialis
Pingback: buy cialis
Pingback: best real money online casinos
Pingback: legal australian online casinos
Pingback: cialis to buy
Pingback: product review website
Pingback: real money casinos
Pingback: lose weight fast
Pingback: cliff castle casino
Pingback: Top 10 Best Sellers Health, Fitness
Pingback: viagra pills
Pingback: quick cash loans
Pingback: pay day loans
Pingback: personal loans
Pingback: cialis tadalafil
Pingback: online casinos
Pingback: play online casino real money
Pingback: viagra without doctor
Pingback: slots online
Pingback: casinos online
Pingback: levitra dosage
Pingback: vardenafil
Pingback: Real cialis online
Pingback: canada online pharmacy
Pingback: over the counter erectile dysfunction pills
Pingback: top rated ed pills
Pingback: ed meds online without doctor prescription
Pingback: cheap viagra
Pingback: viagra 50mg
Pingback: cheap viagra
Pingback: cialis canada
Pingback: where to buy cialis
Pingback: buy real cialis online
Pingback: when does cialis go generic
Pingback: cialis online
Pingback: Viagra brand
Pingback: amoxicillin for uti
Pingback: Low cost viagra
Pingback: cialis 5mg price
Pingback: buy cialis canada
Pingback: where to buy cialis
Pingback: Best viagra price